- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Problems with traffic through a S2S VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Problems with traffic through a S2S VPN
Hello, everyone.
I have a problem with a S2S VPN.
Currently, the traffic originating from our side, to the remote peer, is not "obeying" the security rule it has created.
The traffic is MATCHING a rule, which is almost at the end of the rulebase.
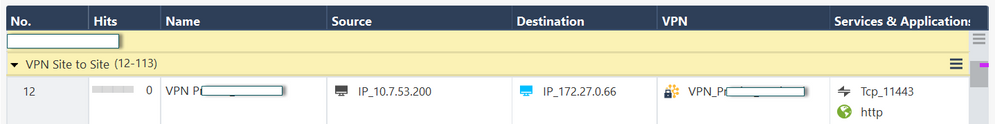
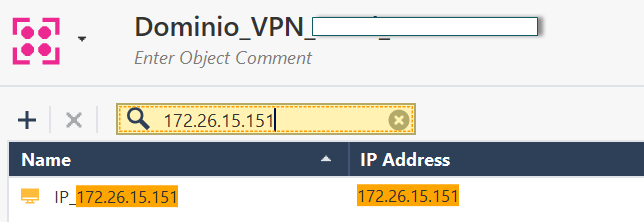
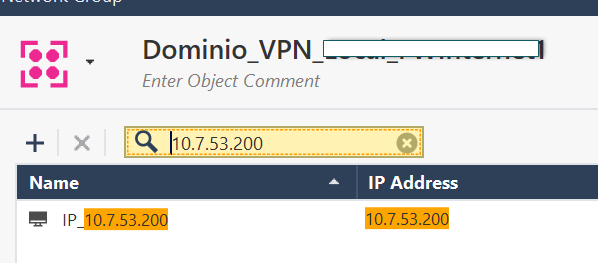
Real IP: 10.7.53.200
NAT IP: 172.26.15.151 (We don't want the remote end to know our REAL IP).
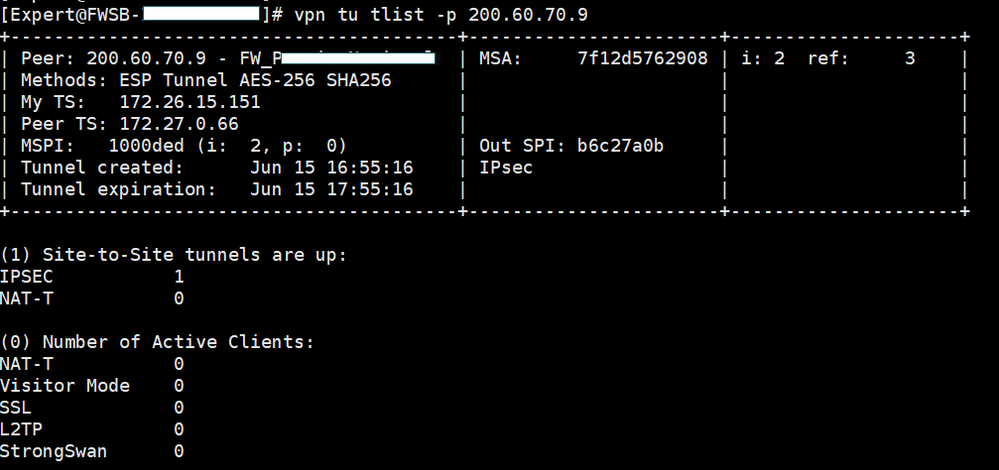
Remote End IP: 172.27.0.66
This image represents the actual rule that has been created for the VPN traffic.
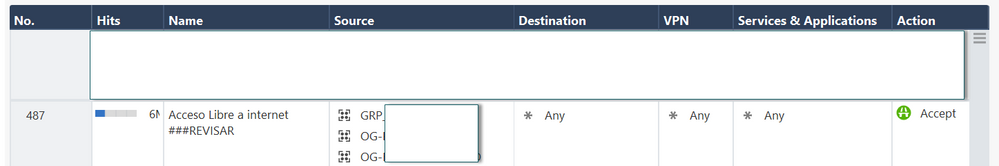
This other image represents the rule with which the traffic is currently MATCHING.
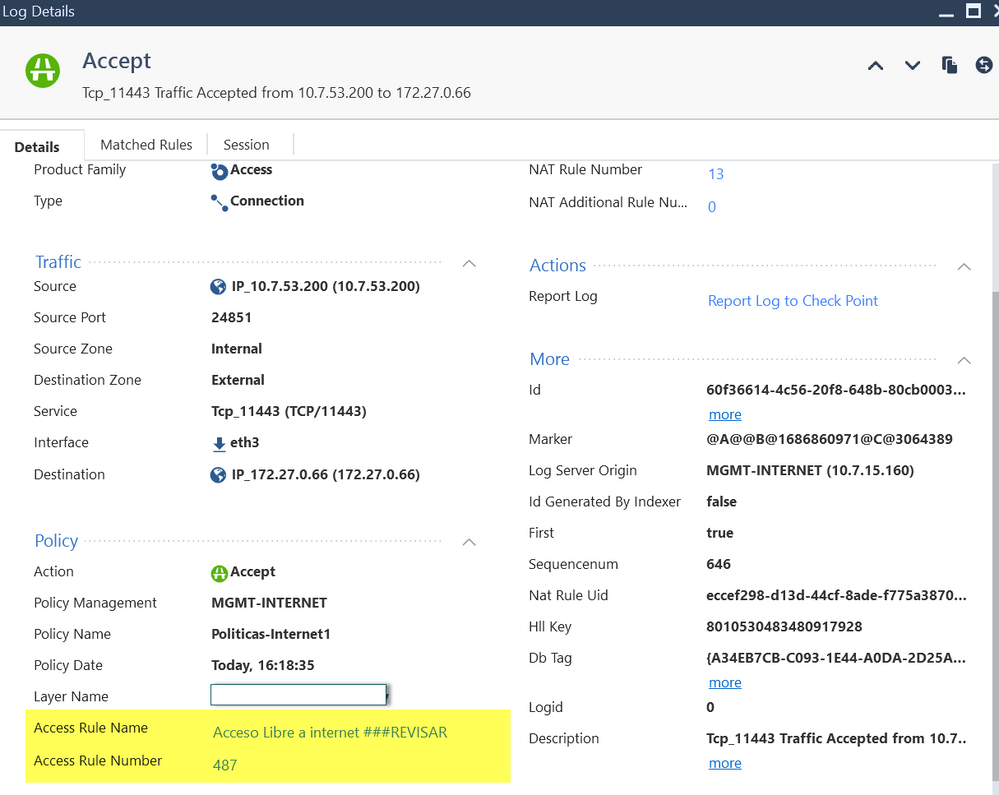
This image represents the detail of a log.
Does anyone know why this is happening?
Why the traffic does not obey our security rule, if it is almost at the beginning of the rulebase?
We are testing the traffic, doing a Telnet to the destination on port 11443.
I would appreciate any comments that can help me to understand the problem.
Regards.
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you confirmed 100% the relevant traffic is actually being encrypted (going through the VPN)?
That means:
- Is the source IP of this traffic (before NAT) in the local encryption domain?
- Is the destination IP of this traffic (before NAT) in the remote encryption domain?
- Would that traffic be routed across the VPN community stated in the rule per the configuration?
The log entry you supplied is a simple "Accept" log, which suggests the traffic isn't encrypted (and thus not matching Rule 12).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
In my VPN DOMAIN, on my side.
I have added, both the REAL IP and the NAT IP.
Currently the VPN is up in phase 1 and 2, but the traffic does not go through the rule that it really should.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The traffic should travel through the VPN, but as I showed in the previous images, the traffic originating from IP 10.7.53.200, to IP 172.27.0.66, "simply" does not pay attention to the explicit rule created (Rule #12).
Traffic from IP 10.7.53.200 is routed to IP 172.26.15.151.
The NAT rule is working fine.
What is not working well is the security rule.
The rule created is almost at the beginning of the rulebase, and I find it strange that the traffic does not match this rule.
Thanks for your comments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A curiosity.
It is mandatory to have the Real IP, and the NAT IP, inside my "VPN DOMAIN"????
Currently I have both IPs inside my domain.
I am working with Manual NAT.
Greetings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't believe the NAT IP needs to be there.
However, the fact the rule is not matching suggests you have a misconfiguration with the VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is the 172.27.0.66 configured as part of the remote encryption domain on YOUR gateway?
Is the relevant peer gateway included in the relevant VPN Community?
When you say the NAT rule is "working" how precisely did you confirm this outside of looking at the logs?
Can you see the actual traffic with a tcpdump or fw monitor?
Unless it's solved by the above, I suspect you're going to need assistance from the TAC: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
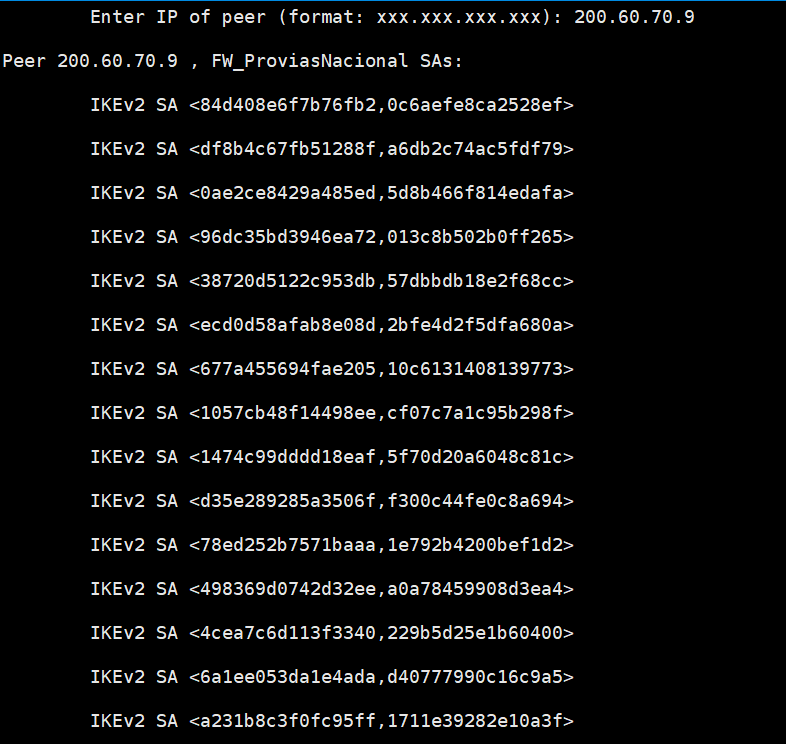
Are you able to try ike v1 ? Anyway an output with more than one IKE SA is not good, i would purge the tunnel
Ps please obscure sensitive data like peer ip
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter