- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Most traffic taking PXL (medium) path, resulting i...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Most traffic taking PXL (medium) path, resulting in high CPU
OK, I'm giving up as I can't understand why would most traffic be pushed via medium path in one of our perimeter GWs.
Setup: GW running R80.40 T139, blades enabled: fw urlf appi ips identityServer.
The only TP blade we have is IPS. Yet running ips off command makes no difference at all. Whilst fw amw unload restores expected state with most traffic being accelerated.
This does not really make sense as AMW unload should only affect TP blades except IPS. But they are not even enabled!
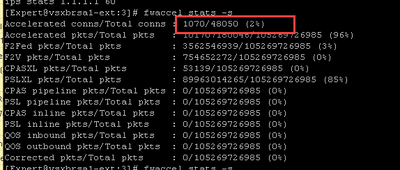
Here are two screenshots: before and after AMW unload:
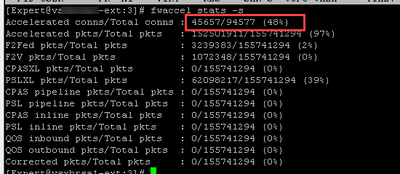
When I look at actual connections - it's pretty much everything, even internal network to DNS is being sent to PXL.
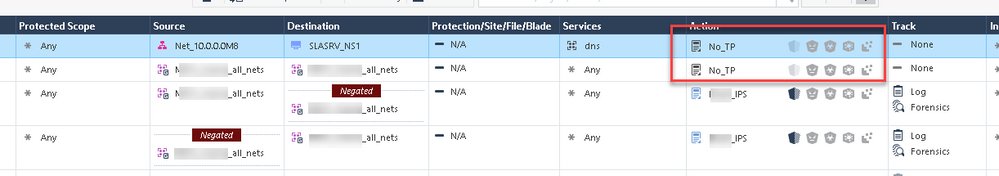
I tried adding explicit TP policy to exclude all internal networks:
But still no joy.
What am I missing?? 🙂
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Throughput acceleration (pkts) is unaffected by the state of AMW, for you it is the Accept templating rate that is being impacted (conns) as well as causing some traffic to go Medium Path. Keep in mind that connections can migrate between different paths and be counted more than once, which is why Accelerated pkts/PXL/CPAS/F2F add up to more than 100%. Let's focus on the templating rate.
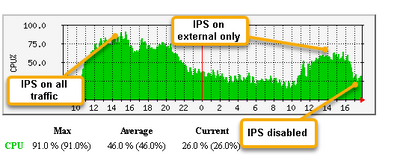
ips off only affects new connections, so you can't expect the acceleration percentage to dramatically change immediately. Try actually unchecking the IPS blade (and ensuring all other TP blades are unchecked) then reinstall the Threat Prevention policy, then reinstall the Access Control policy in a separate operation. Wait about 30 minutes for most existing connections to decay, how does it look then?
Usually Anti-bot is responsible for dramatically reducing connection templating rates (I even call this blade the "slayer" of templates in one of my books) and I'm wondering if there are still some Anti-bot hooks involved even when only IPS is enabled.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Throughput acceleration (pkts) is unaffected by the state of AMW, for you it is the Accept templating rate that is being impacted (conns) as well as causing some traffic to go Medium Path. Keep in mind that connections can migrate between different paths and be counted more than once, which is why Accelerated pkts/PXL/CPAS/F2F add up to more than 100%. Let's focus on the templating rate.
ips off only affects new connections, so you can't expect the acceleration percentage to dramatically change immediately. Try actually unchecking the IPS blade (and ensuring all other TP blades are unchecked) then reinstall the Threat Prevention policy, then reinstall the Access Control policy in a separate operation. Wait about 30 minutes for most existing connections to decay, how does it look then?
Usually Anti-bot is responsible for dramatically reducing connection templating rates (I even call this blade the "slayer" of templates in one of my books) and I'm wondering if there are still some Anti-bot hooks involved even when only IPS is enabled.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i actually run ips off -n which deletes templates, my understanding was that it would help to see effects faster. But lets try with IPS unchecked!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great! Inactivating IPS indeed fixed it too! Ok, job in hand to tweak IPS and maybe get more cores to this VS! Thanks heaps @Timothy_Hall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah it is surprising how often IPS is the culprit in cases like this, but 90% of effective troubleshooting is knowing the right place to look...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter