- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Layer 2 Bridging before Internet Gateway?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Layer 2 Bridging before Internet Gateway?
My Company has a number of Small Business customers who are relying on basic internet connections from Comcast, Fios, Charter, etc... for their primary internet. Most of these Customers already have a primary Internet Gateway/Router that they purchased or rent. My company provides Managed Security Services and these Customers are interested in Firewall solutions but aren't willing to change their existing setups. They want something dropped inline that doesn't change their setup.
We're wondering if there is an Architecture with Layer 2 Transparent bridging on some ports that will work in this setup. This would require a device to Bridge Traffic to the Gateway (pass the DHCP request) then have some capability to also communicate outbound for updates/management with only one DHCP lease. One port would need to be Layer 3 to get a routable IP and point to a Gateway for internet updates.
Use Case would be:
INTERNET-->CHECKPOINT FW-->INTERNET ROUTER --> LAN
Does anyone know if this is possible with any Checkpoint UTM devices?
Based on this article: Bridge Mode it sounds like this could be possible, but I'm not clear.
The article section that is interesting:
Routing and Bridges
Security Gateways with a bridge interface can support Layer 3 routing over non-bridged interfaces. If you configure a bridge interface with an IP address for one Security Gateway (not a cluster), the bridge functions as a regular Layer 3 interface. It participates in IP routing decisions on the gateway and supports Layer 3 routing.
- Cluster deployments do not support this configuration.
- You cannot configure the bridge to be the route gateway.
- One Security Gateway can support multiple bridge interfaces, but only one bridge can have an IP address.
- The Security Gateway cannot filter or transmit packets on a bridge interface that it inspected before (double-inspection).
Management over Bridge
The following diagram shows a sample topology:
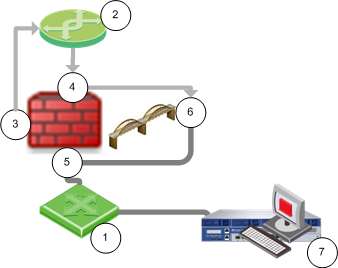
Item | Description |
1 | Switch |
2 | Router |
| Security Gateway Firewall bridging Layer-2 traffic |
3 | Management interface (inspects first packet) |
4 | eth1 (inspects first packet again) |
5 | eth2 |
6 | Bridge interface - Management traffic drops |
7 | Security Management Server |
When a Layer-3 management interface sends traffic through the firewall, the traffic is dropped because it cannot inspect the same packet again.
- The first packet is inspected and then goes from the management interface to the router.
- The router sends the packet to the bridge interface, and the firewall inspects the first packet again. The firewall concludes that this packet is a retransmission and then drops it.
Use the procedure for the applicable Security Gateway version.
3 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you can do what you describe.
However, there is an issue that you will run into where the gateway will reject its own management traffic due to "local interface spoofing."
This can be overcome with the following SK: When configuring two interfaces in Bridge Mode, traffic is dropped due to "local interface spoofing"
However, we are working on a more turnkey solution solution called SandBlast Now.
It was presented at our recent CPX 360 events.
- Video: Threat Hunting with SandBlast NOW
- Presentation: Threat Hunting with SandBlast Now.pdf
If you're interested, I can connect you with the relevant parties.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That would be fantastic if possible. This is an extremely high priority for us so I would love to speak to anyone involved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I’ve already given your details to the relevant parties.
You should be contacted shortly if you haven’t been already. ![]()
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


