- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Issues migrating from Cisco ASA to Check Point
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Issues migrating from Cisco ASA to Check Point
Hi Mates
Just to give more information about the issue I am facing with a customer network.
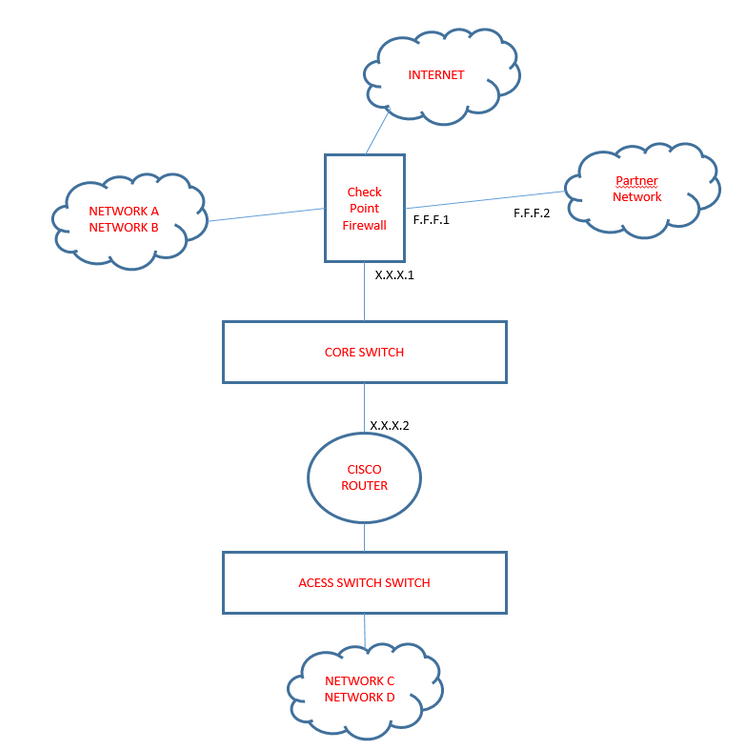
We are migrating the infrastructure from Cisco ASA to Check Point Firewall, everything seems to be working fine but we have this problem that I need help on how I can achieve the same cenario using Check Point. We are using R80.20
There is sit-to-site VPN between the Cisco Router and Check Point. the machines on Networks C and D must communicate with the machines in Networks A and B (vice-versa) using this site-to-site VPN between Check Point and Cisco Router. In addition to that, Networks C and D must also go to the internet through the site-to-site VPN with Check Point that is connected to the internet.
The site-to-site VPN tunel is closed using the Ips: X.X.X.1 from the Firewall and the Peer is X.X.X.2, in order to allow communication between the Networks A and B and Networks C and D, I am doing NAT on the Firewall. Hence, if a host on network A is trying to connect to the Host on network C, the IP of the host in the network A is NATted to the Firewalls IP (X.X.X.1) and vice-versa.
So we have this cenario:
- Networks C and D area able to communicate with Network A and B, and they are also going to the internet through the tunel.
- Network A and B are able to access the internet as well using the F.F.F.2
Problem
- Network A and B are ONLY able to ping Network C and D, and nothing else. You cannot run RDP or SSH from Network A and B to networks C and D.
- There are some services on Network C that are published on the Internet; these services are also not working.
- Another issue that I will be facing too is the fact that with Cisco ASA, they have different site-to-site VPN with their partners using point-to-point links, how can I have Check Point having multiple site-to-site VPN using different interfaces. For example, there is tunnel with Cisco router using X.X.X.1 address, and another tunel with the partner using the F.F.F.1.
Your help will be appreciated
Thanks in advance
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Di,
Regarding your questions:
1. Have you verified the crypto map on Cisco's side? Also the inspection parameters for encrypted traffic?
2. I suppose you're using Domain based VPN, where only the shared networks would bring up the tunnel. You should use an universal tunnel (a tunnel for each pair of Gateways with Internet routing defined on Community) with proper ACL on Cisco's side (https://community.cisco.com/t5/vpn-and-anyconnect/default-route-inside-site-to-site-vpn-tunnel/td-p/...) or switch to Route based VPN instead; both options in order to allow required internet access for networks C and D. NAT also plays an important role, all rules probably must be set manually on Check Point GW.
3. As long you have a route through the right interface, you can create VPN tunnels on point to point links without issues. You can use the Link Selection's option "Calculate IP based on network topology". Obviously all your peers should point to the Check Point gateway instead Cisco router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kenny
1. Have you verified the crypto map on Cisco's side? Also the inspection parameters for encrypted traffic?
On Cisco S«side the crypto map we have only the Network C and D subnets. And on Check Point I have "All IP addresses behind the clusyter....."
Where can I check the inspection parameters for encrypted traffic?
2. I suppose you're using Domain based VPN, where only the shared networks would bring up the tunnel. You should use an universal tunnel (a tunnel for each pair of Gateways with Internet routing defined on Community) with proper ACL on Cisco's side (https://community.cisco.com/t5/vpn-and-anyconnect/default-route-inside-site-to-site-vpn-tunnel/td-p/...) or switch to Route based VPN instead; both options in order to allow required internet access for networks C and D. NAT also plays an important role, all rules probably must be set manually on Check Point GW.
Yes I am using Domain based VPN. I am thinking about switching to Route based VPN, any special recommendations about route-based VPN.
3. As long you have a route through the right interface, you can create VPN tunnels on point to point links without issues. You can use the Link Selection's option "Calculate IP based on network topology". Obviously all your peers should point to the Check Point gateway instead Cisco router.
So in this case create VPN tunnels using route based VPN right?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In this environment I would for sure check out VTI's and run dynamic routing across them.
On top of that why are you using hide NAT between the to area's when you have routing setup already? It just does not make sense and it makes troubleshooting more difficult.
On top of that why are you using hide NAT between the to area's when you have routing setup already? It just does not make sense and it makes troubleshooting more difficult.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Maarten
The customer does not use dynamic routing protocols, it only uses static routing.
The hide NAT was configured to give the Network C and D access to the internet. Any other sugestion?
Thanks
The customer does not use dynamic routing protocols, it only uses static routing.
The hide NAT was configured to give the Network C and D access to the internet. Any other sugestion?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I said you CAN use dynamic routing, in this case static routing will also work.
The hide NAT in this case is best done on the CP, not on the Cisco.
The hide NAT in this case is best done on the CP, not on the Cisco.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Maarten
NAT is being done by Check Point.
NAT is being done by Check Point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So again when using the IPSEC why use NAT inside that tunnel?
And on another point there why use a tunnel at all?
And on another point there why use a tunnel at all?
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Maarten
For some reason the customer used to have tunel internally because the Core Switch and the firewall is housed in a Datacenter outside their control.
You are correct about doing NAT inside the tunel, i will check the possibility of stopping doing NAT.
Just a random question:
I am trying to figured out of VTI works, and there is something that I wish to understand. in Check Point documentation they say VPN Tunel ID must be the same on both ends. I am trying to implement VTI with Cisco, how can I achieve this?
Thanks in advance
For some reason the customer used to have tunel internally because the Core Switch and the firewall is housed in a Datacenter outside their control.
You are correct about doing NAT inside the tunel, i will check the possibility of stopping doing NAT.
Just a random question:
I am trying to figured out of VTI works, and there is something that I wish to understand. in Check Point documentation they say VPN Tunel ID must be the same on both ends. I am trying to implement VTI with Cisco, how can I achieve this?
Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
have a look at this thread:
https://community.checkpoint.com/t5/Access-Control-Products/Domain-based-VPN-to-ANY-0-0-0-0-0-R80-20...
https://community.checkpoint.com/t5/Access-Control-Products/Domain-based-VPN-to-ANY-0-0-0-0-0-R80-20...
Regards, Maarten
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter