- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Identity Awareness using Azure AD
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Identity Awareness using Azure AD
Hi,
Possibly a daft question, but can anyone confirm if IA works against Azure AD as opposed to 'normal' AD? This is for an org that won't have any on prem AD at the end of the implementation.
I've had a look through the deployment guide for the version we would be implementing but it doesn't specifically mention Azure as being OK and I understand from our cloud architects that it's a bit different to AD as I know it.
Thanks in advance.
A.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @adamhi ,
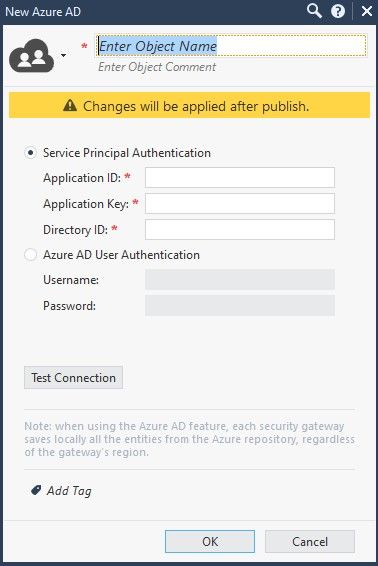
In R80.40, you can use SAML integration with AzureAD for authentication and autorization.
However, in the IDA picker (when you create access roles), you will need to represent the AzureAD objects (users/machines/groups) manually as "Identity Tag" objects.
In R81, the integration of AzureAD in IDA picker will be available, where you can create your AzureAD object and select the objects from AAD same way as you do it on regular AD.
It will be available for EA via R81 EA program. Please contact your local SE for more details.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
43 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Royi_Priov this is still in EA, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @adamhi ,
In R80.40, you can use SAML integration with AzureAD for authentication and autorization.
However, in the IDA picker (when you create access roles), you will need to represent the AzureAD objects (users/machines/groups) manually as "Identity Tag" objects.
In R81, the integration of AzureAD in IDA picker will be available, where you can create your AzureAD object and select the objects from AAD same way as you do it on regular AD.
It will be available for EA via R81 EA program. Please contact your local SE for more details.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks gents, much appreciated.
This isn't going to be needed until Q2 2021, so I'm not sure we need to look into EA. I'll let the hierarchy know that it is feasible given current tech stack.
A
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @adamhi , by that time you will be able to use the GA of this feature (as part of R81).
Good luck 🙂
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, just the manager needs to use the R80.40 to work with SAML? Or the gateways too?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This requires R80.40+ gateways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Martins
I will clarify:
- In R80.40 we have added SAML support to IDA captive portal. it means we can use AAD as SAML Identity Provider.
- in R81 we have added AzureAD as user directory, which means you can configure entities (users/group/machines) from AAD in Identity Awareness Access Roles objects.
Both features requires both SmartCenter and GW to be in this version.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Royi_Priov ,
Thank you for clarify.
Can I use SAML with 3rd party (MFA) as a Identity provider to autenticate the VPN ?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN clients currently do not support SAML authentication.
This is planned for a later release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81 IDA admin guide has two videos regarding SAML and Azure AD configuration. (The SAML video was available in R80.40 admin guide.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Royi_Priov - I went through the R81 Identity Awareness admin guide and watched the videos. It shows that it SAML is supported for Captive Portal. Will this also work for the Endpoint Security VPN clients?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just answered this in a different thread where you asked the same question: coming soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello !
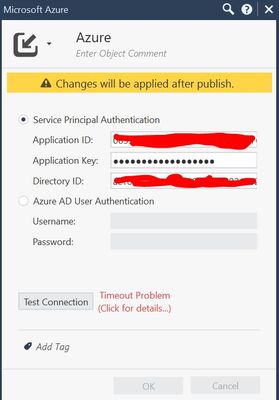
I am trying to add my azure datacenter to checkpoint but the below message occurs:
Seems that checkpoint cannot establish a connection to azure. Yes i have create a custom app to azure.
Please help. I want to have IDA from Checkpoint to Azure AD.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So…what does it say when you click for details?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In which way checkpoint contacts azure?
Do i have to set a policy for this communication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would assume so, yes.
It would be coming from your management in this case, I assume on port 443, to the relevant API endpoint in Azure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You mean the secure management server as a source and destination port 443 to where? can u make an example please?
I have already a rule from sms to everywhere.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The traffic for specific node to azure is allowed and from the management server to internet. I don't understand why this connection fails.
Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Recommend a TAC case here unless @Royi_Priov has other suggestions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fyi Vsec is on. I delete the application from the azure and reinstall it many times. The Azure application id, tenant and secret is 100% percent right. The node has access to azure services, the sms has access everywhere. I am on 80.40 with the latest hotfix. I ve spent many hours on this with no result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the connection is not establishing either with spn or azure ad user authentication.
I am 100% sure something blocking the connection from chekpoint side. Node and SMS are totally allowed for internet access.
Any ideas? how can i debug this connection?
thanx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Usually such messages indicate on a connectivity issue from the Management to Azure AD. Are you working with a Proxy server? If so please verify it is configured also on the Management (GAIA Web UI > Proxy). In case of FQDN or no proxy configuration make sure DNS is configured. If you are positive there is no connectivity issue and there is a connectivity from the MGMT to the proxy/DNS server, please open a ticket in Support to collect debugs and further investigation.
Thanks,
Adi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just found the solution. Thank you all.
As I Said i am on 80.40 and need help how to pick users and groups from azure active directory? Identity Tags? can you give me an example...?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have to manually define Identity Tags in R80.40 that match the existing Azure AD groups.
In R81, we can fetch the groups from Azure AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
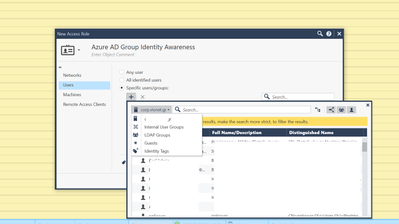
You mean I have to create an access role and instead of group i ll add an identity tag that has object identifier of an azure ad group?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Netadmin2020 ,
I'm a bit confused. You have pasted a print screen from AzureAD object which was added to R81, but you are now stating you are using R80.40. Can you please explain?
The AzureAD object is used for users and groups auto fetch from the AzureAD directory and placing them in the Access Role object.
The Identity Provider object is used for SAML authentication flows (in R80.40 - IDA captive portal and Mobile Access portal, in the near future also RA VPN client and IDA agents).
If you are running R80.40, only the Identity provider object is needed, and the groups should be created manually as Identity Tag objects.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanx for the reply. The version is 80.40 with the latest hotfixes. The Azure AD object (i mean the connector) exists, i have fill my azure application info and the connection is ok.That part is for authorization right? Ok I tried to create a new access role but in the 80.40 it cant "See" the azure ad.
a) So a non ldap user with a device and user from AZURE Active Directory will be identified?
b) With identity tags? how can i create an access role that it will identity an Azure ad object? With object identifier of the specific (for example) Azure AD user?
c) A Policy needed here with source group the non lap access role and the azure identity tag inside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand the problem. There are 2 almost identical objects in SmartConsole: "Microsoft Azure" - used for CloudGuard (aka vsec) and "AzureAD" for Identity Awraeness, which was added in R81.
See that my headline is different:
So, there are 2 options using AzureAD:
1. Stay in R80.40, configure Identity Provider object for AzureAD and authenticate users with SAML in IDA captive portal. In Access Role, you will need to use Identity Tag.
2. Upgrade both SmartCenter and GW to R81 and in addition to the Identity Provider object, configure AzureAD object for Access Role usage
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For some reason the first picture isn't shown, so I'm posting it again.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 26 | |
| 11 | |
| 10 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter