- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: IPsec Enhanced Mode - tunnel redundancy
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IPsec Enhanced Mode - tunnel redundancy
Hi CheckMates,
Because I've not found answers to my questions in documentation and community ... I decided to just ask if anyone from you already have any experience with the new enhanced mode for IPSec that was introduced in R82.
What I want to achieve is IPsec redundancy.
With legacy mode I can do it for example that way:
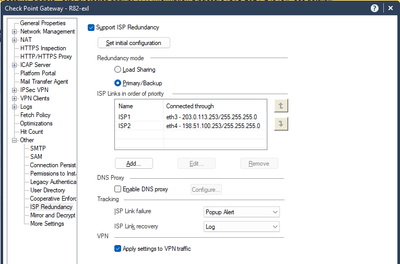
1) configure ISP Redundancy ... here provide Primary and Backup interfaces and check "Apply settings to VPN traffic" - it will automatically change Link Selection as probing:
2) then I can create two Interoperable Devices in case peer also has two ISPs (1st = Peer's ISP1, 2nd = Peer's ISP2)
3) and VPN Community object with 3 gateways (Check Point + 2x Interoperable Devices with the same VPN Domain)
With the above configuration everything works as expected - once my Primary ISP will fail new IPSec tunnel is instantly established via Backup ISP.
Then when Primary ISP will be back online ... I will have two IPSec tunnels unless I will shutdown this one that is already establised via Backup ISP.... and with this Check Point will send traffic via Primary ISP, and will receive response via Backup ISP (a little strange ... but also expected if peer will not switch to this "repaired" Check Point's primary ISP).
So everything is fine... except one minor issue.
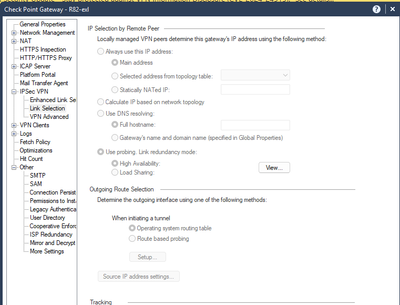
For some reason Check Point is using Main IP for "local ID" in IPsec and not the one from Link Selection.
So if my Main IP is for example from my management network tunnel will not be established unless I will provide this Main IP in peer's configuration for IPsec. Without ISP Redundancy "local ID" is the same that is selected in "Link selection".
Probably it can be changed in GuiDbEdit ... but yeah ... it's weak.
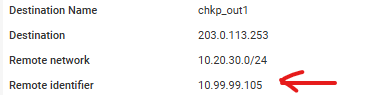
If you don't understood what I meant ... this screenshot should explain it:
Above screenshot shows information from peer's log ... as you can see it receives from Check Point 10.99.99.105 instead of 203.0.113.253.
I decided to check this new enhanced mode.
I expected that it should work like that:
1) for Check Point I'm selecting Primary and Backup interface
2) then I have one Interoperable Device with two IPs (external) and here also one will be Primary, another Backup
And if everything will be fine they should connect via Primary<->Primary.
In case any of ISPs should fail it will be Primary<->Backup or Backup<->Primary, or Backup<->Backup.
But ... it doesn't work like that...
First issue:
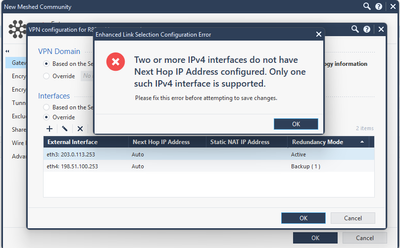
I can't have "Auto" for both interfaces ... so I need to select "Next Hop IP Address".
So ... I selected Next Hop IP Address for one of them ... and it didn't work at all - no IPsec tunnel was established with peer.
Then after some strugling and troubleshooting I've found that Next Hop IP Address was wrong one.
For me ... Next Hop in this case = my gateway .... but I had to change it to Peer's IP ! ... so it should be named "Peer's IP"... really strange.
With that tunnel was established via Primary<->Primary.
Then I decided to break connection for this Primary interface.
I expected that new tunnel sbould be established via Backup interface ... it took like one minute and then it was established between Backup<->Backup.
It's not what I expected...
Do you have some experience with this ?
Can you show me what I'm doing wrong, what I could do better ?
How it should be done to achieve the best results ?
Best
m.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like my previous tests with Enhanced Mode gave wrong results ... I was testing this on HyperV.
Another test but this time on Proxmox gave expected results... in both cases that I wanted to test:
Option 1:
Two ISPs on Check Point, one ISP on peer:
Option 2:
Two ISPs on Check Point and peer:
In both cases it worked as expected:
1) when everything works we have tunnel between ISP1->ISP1
2) once ISP1 on Check Point site died tunnel was between ISP2<->ISP1
3) once ISP1 on Check Point returned tunnel was back between ISP1<->ISP1
4) once ISP1 on peer site died tunnel was between ISP1<->ISP2
etc,
**bleep** HyperV...
Best
m.
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like my previous tests with Enhanced Mode gave wrong results ... I was testing this on HyperV.
Another test but this time on Proxmox gave expected results... in both cases that I wanted to test:
Option 1:
Two ISPs on Check Point, one ISP on peer:
Option 2:
Two ISPs on Check Point and peer:
In both cases it worked as expected:
1) when everything works we have tunnel between ISP1->ISP1
2) once ISP1 on Check Point site died tunnel was between ISP2<->ISP1
3) once ISP1 on Check Point returned tunnel was back between ISP1<->ISP1
4) once ISP1 on peer site died tunnel was between ISP1<->ISP2
etc,
**bleep** HyperV...
Best
m.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for that @marcyn . I tested this in my R82 lab a little bit last week and I really like the enhanced mode, great addition.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
At first I also thought that I will love it ... but because I had this ackward results I lost hope...
... luckily I got it back now 🙂
Best
m.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice to know the new ISP Redundancy options in R82 worked for you.
Curious why it wasn't working so well in HyperV...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter