- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- How to configure identity collecto to parse syslog...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to configure identity collecto to parse syslog message from Pulse Secure VPN
Hi Expert!
I would like to know if anyone here has ever configure identity collector to parse syslog message from Pulse Secure VPN.
If yes, Could you please kindly share some Syslog Parser Information, like screenshot below?
I had ever test integration with AD, this is very simple to collect identity information. But recieving syslog message is different.
Thank you in advace.
Regards,
Sarm
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you read this already ? https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_IdentityAwareness_AdminGuide/Topic...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albercht,
Sorry for late response.
Yes, I read it but I don't understand totally, I'm not sure which message subject that I supposed to put it and other attribute to field box.
Could you please give me some clue to complete this? Below is syslog messages that I received from Pulse Secure VPN
In my case, I want to get user01 with IP 192.168.100.2 (In this example here), to create a policy with Access Role on Firewall.
05-17-2021 10:46:37 Local0.Info 10.4.117.179 1 2021-05-16T20:44:44-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:44 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - Key Exchange number 1 occurred for user with NCIP 192.168.100.2
05-17-2021 10:46:37 Local0.Info 10.4.117.179 1 2021-05-16T20:44:44-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:44 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: User with IP 192.168.100.2 connected with ESP transport mode.
05-17-2021 10:46:31 Local0.Critical 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [127.0.0.1] System()[] - Number of concurrent users (2) exceeded the system limit (2).
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: User with IP 192.168.100.2 connected with SSL transport mode.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: Session started for user with IPv4 address 192.168.100.2, hostname BAY-CLIENT
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [127.0.0.1] System()[] - VPN Tunneling: Optimized ACL count = 2.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [127.0.0.1] System()[] - VPN Tunneling: ACL count = 2.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - Agent login succeeded for user01/Realm-NC (session:00000000) from 10.4.117.189 with Pulse-Secure/9.1.11.8575 (Windows 10) Pulse/9.1.11.8575.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[] - Primary authentication successful for user01/System Local from 10.4.117.189
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have the same problem. If you have a solution, please send it here.
Best regards,
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Markus,
I'm still finding the solution, below is the syslog messages from Pulse Secure that I monitor on syslog server.
I'm not sure if this message is the same as your environment.
05-17-2021 10:46:37 Local0.Info 10.4.117.179 1 2021-05-16T20:44:44-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:44 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - Key Exchange number 1 occurred for user with NCIP 192.168.100.2
05-17-2021 10:46:37 Local0.Info 10.4.117.179 1 2021-05-16T20:44:44-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:44 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: User with IP 192.168.100.2 connected with ESP transport mode.
05-17-2021 10:46:31 Local0.Critical 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [127.0.0.1] System()[] - Number of concurrent users (2) exceeded the system limit (2).
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: User with IP 192.168.100.2 connected with SSL transport mode.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: Session started for user with IPv4 address 192.168.100.2, hostname BAY-CLIENT
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [127.0.0.1] System()[] - VPN Tunneling: Optimized ACL count = 2.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [127.0.0.1] System()[] - VPN Tunneling: ACL count = 2.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[RoleNC] - Agent login succeeded for user01/Realm-NC (session:00000000) from 10.4.117.189 with Pulse-Secure/9.1.11.8575 (Windows 10) Pulse/9.1.11.8575.
05-17-2021 10:46:31 Local0.Info 10.4.117.179 1 2021-05-16T20:44:38-07:00 10.4.117.179 PulseSecure: - - - 2021-05-16 20:44:38 - ive - [10.4.117.189] user01(Realm-NC)[] - Primary authentication successful for user01/System Local from 10.4.117.189
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did anyone ever come up with a solution for this? We have a requirement to parse some logs from a PulseSecure appliance. We can parse a sample of logs in the tool, but when we install the parse file it breaks something.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Scott_Paisley
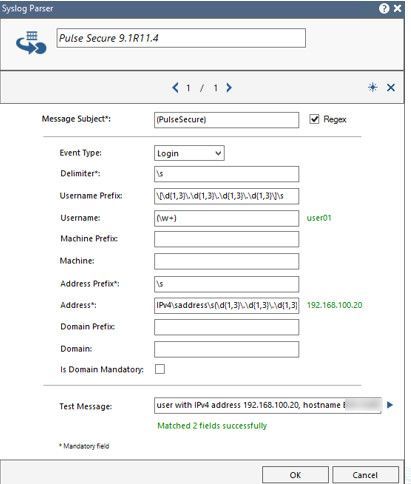
I already resolved the problem by parsing syslog from PulseSecure VPN as below screenshot and it worked fine on my lab.
10.x.x.189 PulseSecure: - - - 2021-06-15 00:39:31 - ive - [10.x.x.189] user01(Realm-NC)[RoleNC] - VPN Tunneling: Session started for user with IPv4 address 192.168.100.20, hostname xxx-xxx"
I also copy and paste each of the attributes here for your test purpose in your lab.
Message Subject*: (PulseSecure) with ticking RegEx checkbox
Event Type: Login
Delimeter*: \s
Username Prefix: \[\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\]\s
Username: (\w+)
Address Prefix: \s
Address*: IPv4\saddress\s(\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter