- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Hide NAT of the FW external IP in VSX configuratio...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hide NAT of the FW external IP in VSX configuration
Hello,
is auto hide NAT possible for the FW IP (external interface of course) in VSX configuration?
Specifically, we have an Edge Firewall (Virtual System) with two interfaces (internal and external). Both interfaces are directly connected to a border router (Cisco 6800).
[Expert@lntfw-pgtw2:4]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.196.0 0.0.0.0 255.255.255.240 U 0 0 0 bond2.997
192.168.196.16 0.0.0.0 255.255.255.240 U 0 0 0 bond2.998
10.100.98.0 0.0.0.0 255.255.255.0 UD 0 0 0 bond2.998
10.100.97.0 0.0.0.0 255.255.255.0 UD 0 0 0 bond2.997
x.x.0.0 10.100.97.1 255.255.0.0 UGD 0 0 0 bond2.997
0.0.0.0 10.100.98.1 0.0.0.0 UGD 0 0 0 bond2.998
Since the external interface has a private IP (10.100.98.101), the VS can't go to the Internet. So, I'd like to add a hide NAT (with one of our public IPs) to the 10.100.98.101 IP address. I already tried these two methods:
- Created an object with IP 10.100.98.101 and set the option "NAT --> Add automatic address translation rules --> Hide behind IP address" (with public IP).
- Created an object with IP 10.100.98.101 (let's call it Priv) and another object with public IP (let's call Pub). Then I added the object Priv in "Original Source" and the object Pub in "Translated Source".
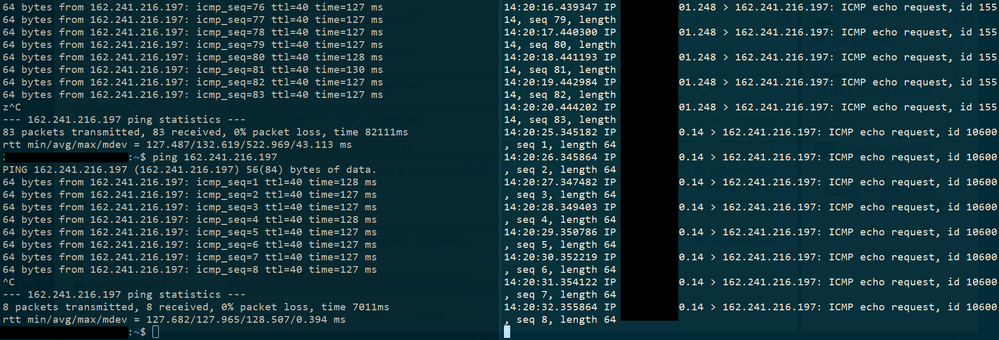
Unfortunately, I didn't have success... both methods didn't work. Tcpdump shows always 10.100.98.101 as source if I try to ping or telnet some destination. So, since I read here this mechanism is feasible, I'm worndering if that is the same in VSX environments...
Thanks,
Francesco
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would just create a NAT rule that has a group with all the addresses/nets you want to hide-nat as original source. Original destination would be any. Translated source would then be an object with your selected public address with method Hide. Place it at below all you other more specific NAT-rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
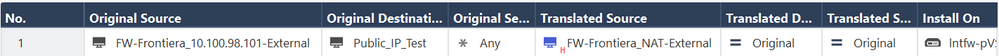
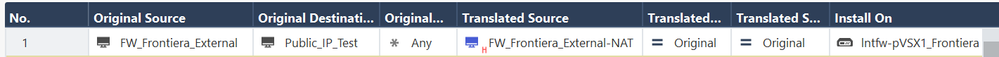
That was exactly the second method I tried. Please see the following images (tried again towards a single Public IP as destination for a test):
- The object FW-Frontiera_10.100.98.101-External is a host containing the private IP 10.100.98.101 of the external interface.
- The object Public_IP_Test is just a public IP to test the NAT (162.241.216.197)
- The object FW-Frontiera_NAT-External is a host containing one of our enterprise Public IPs
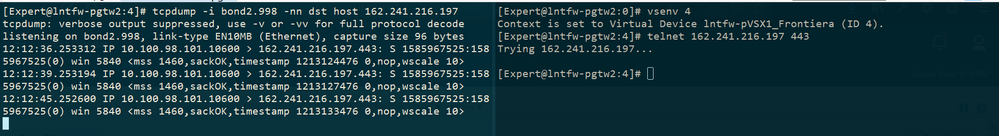
As you can see, the source IP remains 10.100.98.101...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
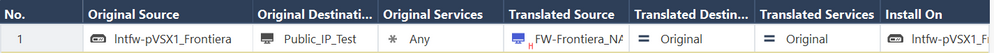
What if you tried with the VS-object for Original Source, instead of an object containing just the external ip?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
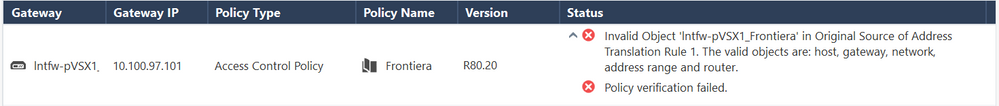
Already tried:
but...
Gateway: lntfw-pVSX1_Frontiera
Policy: Frontiera
Status: Failed
- Invalid Object 'lntfw-pVSX1_Frontiera' in Original Source of Address Translation Rule 1. The valid objects are: host, gateway, network, address range and router.
- Policy verification failed.
--------------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hmm.. never had to do NAT for traffic from the firewall itself, so I have not run into this before. Is this how it is supposed to be in production?
Don't you have a host behind the firewall you can test from?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, a test host works well. Please see the example below (before and after the NAT )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any other ideas?
Thanks,
Francesco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
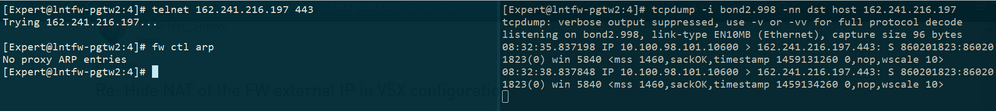
What I'm missing here is the version you are running. Your second methos should work just fine, should not matter if it is VSX or not. What you should check though, after installing the policy, is if the NAT is showing a proxy arp for the IP by issueing in the VS context: fw ctl arp
Another small thingy, double check the Install on column, it shows a name there...
Another small thingy, double check the Install on column, it shows a name there...
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
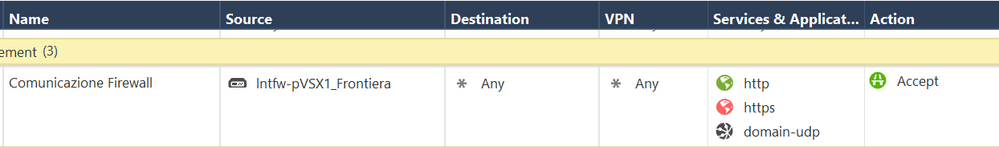
Just a dumb question but, is there an ACL for the traffic to be permitted ? I mean the 443 traffic and not the ICMP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Maarten_Sjouw: the VSX/Gateway version is 80.20, while the Server Management is running version 80.30.
After the installation, the command outputs "No Proxy ARP entries"
The "Install On" is set to the correct VS.
@funkylicious: I've just added an explicit rule as you suggested, but that traffic, I think, should be ensured by Implied Rules... anyway, nothing changed; please see the telnet/tcpdump screenshot above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a other question, why do you need the NAT from the VS itself? Normally all updates etc are done from VS0, so if you need anything to be able to go to the internet it would be VS0 not the VS itself.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since I'd like to enable advanced functionalities, for instance:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then I would suggest opening a case with TAC
Regards, Maarten
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter