- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E5:
Powering Prevention: The AI Driving Check Point’s ThreatCloud
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata, Securing the Agentic AI Era
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- Re: HTTPS Inspection issue
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
HTTPS Inspection issue
Hi All,
I have opened a case with checkpoint on Friday last week, still haven't got the issue resolved, so maybe somebody here can give me some ideas of where to look.
The client has a 3100 Appliance with Checkpoint management server and HTTPS inspection enabled. Management Server and Device both running version R81.10 and up to date.
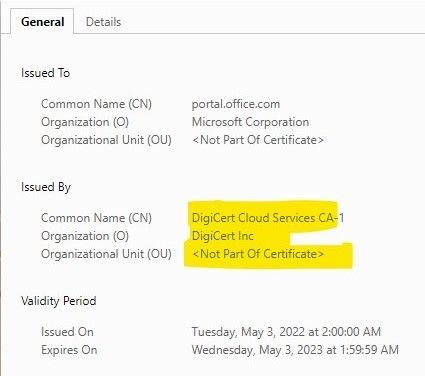
Users have been experiencing issues logging into Teams, and in my testing I have had issues connecting to certain websites like office.com and even checkpoint.com. The https inspection certificate is deployed via GPO and it is installed on under Trusted Root Certificate Authority.
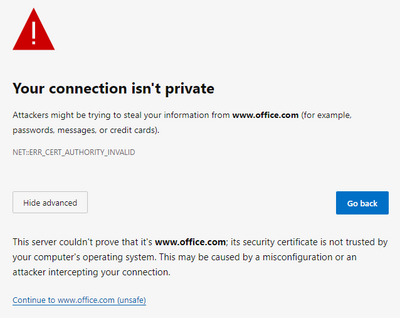
Testing with Chrome I get an error your connection is not private. You cannot visit www.checkpoint.com right now because the website uses HSTS. Network errors and attacks are usually temporary, so this page will probably work later.
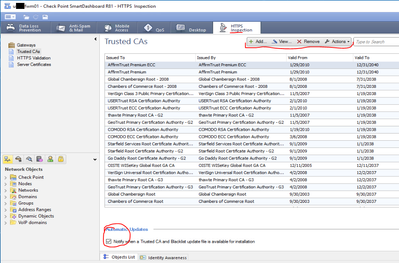
I updated the Trusted Ca list and added the Https Inspection Certificate to the list under SmartDashboard and installed policy but that has not helped.
I have resorted to bypassing all traffic in the HTTPS Inspection policy which is not ideal and then I can connect to checkpoint.com or office.com without any issues.
Labels
- Labels:
-
HTTPS Inspection
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
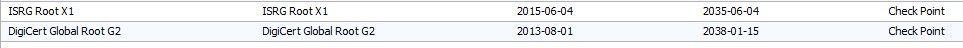
Thank you to everybody who took the time to respond to the issue I was experiencing. I did a remote session with checkpoint, the issue was resolved adding two Certificate Authorities that where missing to the Https Inspection Trusted CA.
ISRG Root X1
DigiCert Global Root G2
Once these where added I was able to connect to the office.com and checkpoint site without any issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
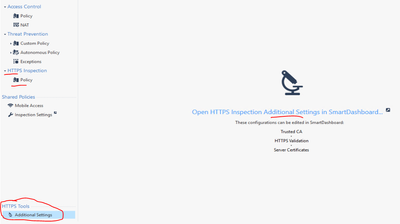
Hello @casgrain ,
Certificates can be imported into Checkpoint HTTPS Tools (you should have bumped into that if you were doing HTTPS Inspection) .
Thank you,
27 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a StandAlone SMS / GW with https inspection enabled ? This is HW from 2016, so it might well be that R81.10 SMS & GW & https inspection is too much work - have a look in cpview to see the load history !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your reply. Yes it is StandAlone SMS / GW with HTTPS inspection enabled. Cpview looked okay from what I could tell.
Browsing office.com as my testing I noticed the bellow observations, the left image is with HTTPS inspection, the right is without.
The custom HTTPS bypass rule does not appear to be working, I have added portal.office.com and office.com and it still inspects them. The financial services rule is working in that I could connect to banking sites with no issue.
I tried a local news website, and it connects fine, the certificate shows issued by and the name of the HTTPS inspection certificate "client.com"
I observe the following log in the Man Server:
I have had a look at sk159872, which doesn't seem to give me any help, I updated the Trusted CA list on the smartdashboard with Checkpoint support yesterday. I have added the https inspection certificate to this list and it has not helped. I have observed a fair number of Microsoft URL's failing with Untrusted Certificate.
I am waiting for more feedback from Checkpoint as to what to check next.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I worked with customer who had very similar issue and it turned out to be certificate related, will have to see what exactly. Question...does same problem happen in EVERY browser, or just chrome?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
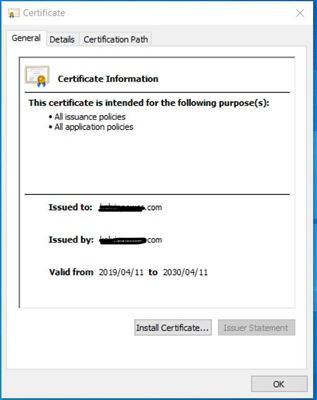
I have tried it in edge and does a similar thing, the certificate has been in use since 2019. Issued to is the "domain.com" of the client. I wander if the name is causing issues, if I recall it was generated on the firewall when we setup HTTPS inspection.
.
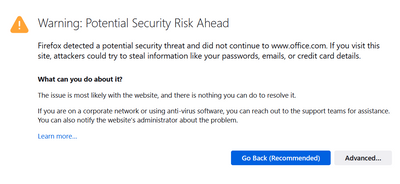
In edge I get the following warning but can choose to to still visit the site.
I upgraded the firewall to R81.10 on the 18 August, and 2 weeks later (2 September) I was notified of issues with staff connecting to teams. If it broke with the upgrade to R81.10 I would have expected to be notified much earlier as they have weekly Teams meetings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firefox showed the following information first on office.com
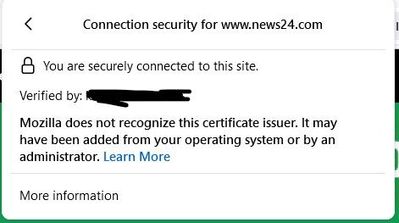
When I go to a local news site I saw this warning checking the certificate and shows the verified by certificate name.
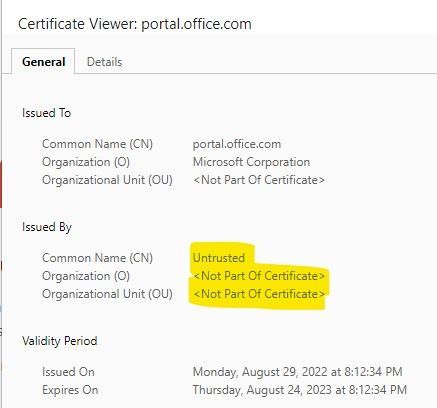
The certificate issued is self issued from the firewall and was added by the administrator via GPO. I understand the basic concepts of how HTTPS inspection works, but I can't figure out which part of the process is failing causing the your connection is not secure warning.
Could certain websites like office.com or checkpoint.com have extra security and warning the browser it is not getting a known certificate so this connection is insecure. The local news website doesn't have these added security features which is why it connects to the site and gives the warning as above when viewing the certificate details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I saw with my customer it was the issue where SAN (subject alternative name) was missing in the cert, but may had not been exact same problem like what you are having. Question...when you compare the cert you see for one that works and one that does not, what is the difference?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rockthank you for coming back to me. I will have a look at the certificates in more detail. Its weird that I can connect to some sites and the browser shows me the https certificate and it works but refuses to connect to Microsoft or Checkpoint websites.
Maybe I need to create a new certificate on the firewall and see if that solves the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get what @Wolfgang is saying, but I find it odd that it worked fine for some time and then stopped all of a sudden. I have a really nice lab with https inspection that it works using self signed cert from the firewall if you wish to have a look, happy to show you. I have windows 10 PC behind the fw and we can test any site you have issue with.
Let me know.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
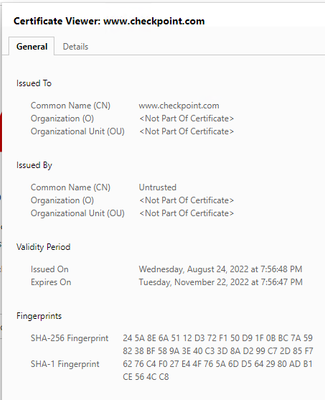
Thank you for your reply. I would be interested to see what the certificate info is in your lab with https inspection if you visit https://www.checkpoint.com/
When I go to checkpoint using Edge I get the bellow on the certificate info. The issued by part is what is causing my issues I suspect. On other websites that work it shows the name of the certificate the firewall created.
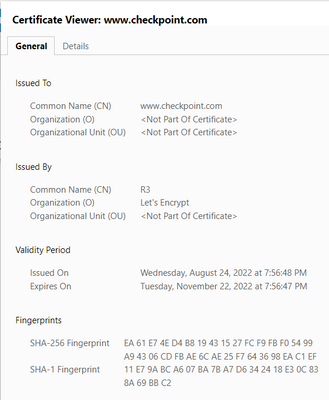
How it looks on my machine bypassing HTTPS inspection as I am not domain joined.
Today I resorted to adding all the users who need to use Teams meetings to a bypass group we have as temporary fix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get exact same message for cert as your 2nd screenshot, but thats most likely because I am NOT inspecting the website, otherwise, if I were, I would get firewall cert.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this Andy. I have a HTTPS Custom Bypass list under No SSL inspection, which includes Health and Financial Services category. The groups appear to work as I can reach bank sites, the custom list is not working 100%. I added https://www.checkpoint.com/ but still can't get to the site with out a warning. Going to do some troubleshooting with this area.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Lets do remote, I would need to see why that happens.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the reply Andy. Checkpoint had booked a support call for today and they resolved the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What was the solution if you dont mind sharing? We always like to share the positive outcome, so it helps everyone else.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@rmasprey you wrote certificate from the firewall is self signed…
Does this mean you are using CheckPoints firewall management internal CA for HTTPS inspection?
If yes, you have to deploy this root CA certificate to your clients. If you have a look at the trusted chain on the client you should see the newly created certificate for the inspected website and all CAs up to the root CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the reply @Wolfgang, yes it is a self signed certificate from the firewall and it is deployed to the workstations via a group policy. This has been working up until recently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you to everybody who took the time to respond to the issue I was experiencing. I did a remote session with checkpoint, the issue was resolved adding two Certificate Authorities that where missing to the Https Inspection Trusted CA.
ISRG Root X1
DigiCert Global Root G2
Once these where added I was able to connect to the office.com and checkpoint site without any issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, makes sense. We had case with escalation about this in the past and were give some sort of script from R&D, but then were told not to run it as it could cause more issues, so client just added them manually. Glad it worked out!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How did you add those CAs to the list?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @casgrain ,
Certificates can be imported into Checkpoint HTTPS Tools (you should have bumped into that if you were doing HTTPS Inspection) .
Thank you,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jumping on the thread - I've recently enabled https inspection on a test firewall and run into a number of challenges, most of them resolved.
The part I've finding suprising is the fact I'm having to import public CA certs in the custom trust store on R82 even though Checkpoint should really be keeping these updated.
I'm mean major sites not working such as cisco.com, citrix.com, azure.com, even Israel own news site.
I've had to test what I can, downloaded the certs and install them, then it works.
I do have a TAC case open and I am providing every certificate link to Checkpoint, requesting either these are maintained by Checkpoint in terms of importing into Checkpoint via the feed, or explain why I have to do this (to be fair most of the root CAs are in the auto feed trusted store).
Here a list of the certs I had to import (its not the complete list but most of them):
http://cacerts.digicert.com/DigiCertGlobalG3TLSECCSHA3842020CA1-2.crt
http://cacerts.digicert.com/DigiCertEVRSACAG2.crt
http://cacerts.geotrust.com/GeoTrustTLSRSACAG1.crt
http://cacerts.geotrust.com/GeoTrustTLSECCCAG1.crt
http://cacerts.thawte.com/ThawteTLSRSACAG1.crt
http://cacerts.rapidssl.com/RapidSSLTLSRSACAG1.crt
http://cacerts.rapidssl.com/RapidSSLTLSECCCAG1.crt
http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20ECC%20TLS%20Issuing%20CA%2007%20-%20xsign....
http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20ECC%20TLS%20Issuing%20CA%2004%20-%20xsign....
http://www.microsoft.com/pkiops/certs/Microsoft%20TLS%20G2%20RSA%20CA%20OCSP%2016.crt
http://caissuers.microsoft.com/pkiops/certs/Microsoft%20TLS%20G2%20RSA%20CA%20OCSP%2016.crt
http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20RSA%20TLS%20Issuing%20CA%2003%20-%20xsign....
http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20RSA%20TLS%20Issuing%20CA%2004%20-%20xsign....
http://www.microsoft.com/pkiops/certs/Microsoft%20TLS%20G2%20RSA%20CA%20OCSP%2004.crt
http://www.microsoft.com/pkiops/certs/Microsoft%20TLS%20G2%20ECC%20CA%20OCSP%2006.crt
http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20RSA%20TLS%20Issuing%20CA%2007%20-%20xsign....
http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20RSA%20TLS%20Issuing%20CA%2008%20-%20xsign....
http://www.microsoft.com/pkiops/certs/Microsoft%20TLS%20G2%20RSA%20CA%20OCSP%2010.crt
http://crt.r2m04.amazontrust.com/r2m04.cer
http://cacerts.digicert.com/GoGetSSLG2TLSRSA4096SHA2562022CA-1.crt
http://cacerts.digitalcertvalidation.com/TrustProviderBVTLSRSACAG1.crt
The one issue I have at the moment which seems to be related to HTTPs inspect is logging into citrix for downloads which uses "https://accounts.cloud.com/core/mfa"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting. I never had to do that in R82 lab.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does seem strange, I'm hoping that I'm actually doing something wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This solved it for me thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This resolved my issue, however I am unable to access www.cisco.com. I am getting the below error, please how you resolved yours.
"
Did Not Connect: Potential Security Issue
Firefox detected a potential security threat and did not continue to www.cisco.com because this website requires a secure connection.
What can you do about it?
www.cisco.com has a security policy called HTTP Strict Transport Security (HSTS), which means that Firefox can only connect to it securely. You can’t add an exception to visit this site.
The issue is most likely with the website, and there is nothing you can do to resolve it.
If you are on a corporate network or using antivirus software, you can reach out to the support teams for assistance. You can also notify the website’s administrator about the problem.'"
Regards,
Salom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This means FF is detecting that HTTPSi is substituting the certificate. Either double-check that FF is trusting Check Point HTTPSi root certificate or make an exception for cisco.com in HTTPSi policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, look into sk106996
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 32 | |
| 18 | |
| 12 | |
| 11 | |
| 10 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 5 |
Upcoming Events
Fri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter