- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Rule matching questions
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rule matching questions
I have a question on policy matching. From the information on ...
...I understand that :
###
for an inline layer (sub-policy), if a packet matches the parent rule, the sub-policy is applied. Meaning 2 options within that policy :
1) a match is found in the subpolicy --> do the action from that matched sub-rule (drop or accept) -->
"no more rulebase checking is done"
2) no match is found --> action from explicit Cleanup rule is executed, if there's no explicit Cleanup, the implicit Cleanup rule is executed (could also be drop or accept) -->
"no more rulebase checking is done"
###
For inspection to continue to a next ordered layer, the action must be ACCEPT.
If the action is DROP, the firewall doesn't care about possible next ordered layers.
So now the questions :
1) But what if the action from an inline layer's explicit or implicit Cleanup is ACCEPT ? What happens next ? ( when other ordered layer are configured ? ) Does inspection of lower ordered layers still happen ?
2) If you decide to use ordered layers, you better define an explicit or implicit Cleanup rule with Accept ( if not none of your next ordered layers will ever be checked ), right ?
Thanks.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. Yes, inspection will continue
2. Depends on the needs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding 1 : thanks for your confirmation Sir. So after any accept action ( meaning either from a sub-policy rule with accept, or from the sub-policy Cleanup rule with an accept ) , if there's another order layer configured. The inspection proceeds to the next ordered layer ... or only if it hit a Cleanup with Accept action?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, the action on the main rule is actually "inline layer", not accept.
Clean-up rule in the inline layer only applies to what's matched to the main rule.
Inspection for traffic that DOES NOT match the main rule always continue, regardless of the said inline layer clean rule settings.
You can take it as a sub-routine with initial conditions. Of the conditions are not matched, you go to the next sub-routine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK , so the statement from within the Checkpoint documentation mentioned in the topic start called ""no more rulebase checking is done", actually means no more checking is done within that layer ? And also implies a next ordered layer is being checked against ... , correct ?
Sorry for asking so thoroughly, but is't crucial info to understand 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The statement is correct, regardless of inline layer logic, actually. If we can match the first packet to a drop rule, no further matching effort is done.
It is different for accept action. You need to consider the logic of Unified policy, which assumes that the rule match may not be fully done based on a first packet, and might require application and/or content inspection decision, which require data flow to start.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, so to resume :
Whenever there's a hit on rule with a drop action, it's final.
Whenever there's an accept, the layers below are checked against also ( if they contain a drop, it's over and out, if they contain an accept it goes further down the next ordered layers etc... )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, it is even more interesting for accept action 🙂
Imagine you have a layer with the main rule
| Rule number | Source | Destination | Services and Applications | Content | Action |
| 1 | Internal Networks | Internet | Web Services | Any | Inline Layer |
| 1.1 | Any | Any | Gambling Category | Any | Drop |
| 1.2 | Any | Any | Any | Excel Files | Drop |
| 1.3 | Any | Any | Streaming Services | Accept | Log and Accounting |
| 1.4 | Any | Any | Any | Accept | Log |
Rule 1.4 is the cleanup for the section.
With the first package, if we cannot guess at once that it is either 1.1 or 1.3 (depends on application), all rules 1.1 to 1.4 will be conditionally matched. As at least one of them saying "Accept", we let traffic through, because we cannot make a final match on the first packet for most of it.
Now, when the data start flowing, we can make a final match. If I am trying to upload an Excel file, it will be blocked by 1.2. If it is a regular web, we will not change final match, which is 1.4. IF we suddenly detect video service, we will re-match to 1.3.
Did I confuse you yet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That inline layer example actually makes perfect sense. When I mentioned 'the layers below', I had only ordered layers in mind. As you mentioned for further analysis to be possible ( after first packet ) there has to be an accept somewhere to continue investigation. 🙂
Got it. Thx.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
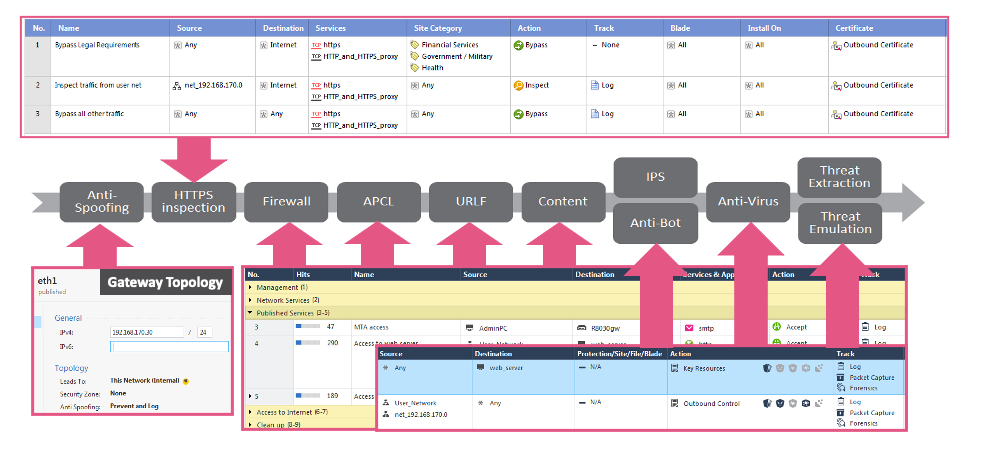
Depending on how your layered policy is built, the layered policy match may be different.
The order is:
- Anti-spoofing
- HTTPS Inspection
- Network Security, Application Control/URLF, Content Inspection (one line if they are used together, if layered, then after Network Security)
- IPS/Anti-Bot
- AVI
- Threat Extraction(Emulation
For anything below 3, action on the Network Security Rule should be Accept.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your explanation. This helped.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I fully understand the matching and "possible match" scenarios. We have a client that has an inline layer and does use Application and URL filtering in this layer. I generally works well. Now that we created a viable inline layer the client would like to change the cleanup rule to Drop from Accept. How will this impact the "possible match" scenario? My understanding is that there would be a possible match on 1.3 (example above) but the initial handshake would be 1.4 (accept). What if this is a drop; does the match drop the traffic even though there is a "possible match"? Does this type of behavior mean that you would never use Application and URL filtering in an Inline Layer if you wanted a Cleanup rule to be drop?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter