Watch Out: Antispoofing Enforcement
Antispoofing ensures that traffic is flowing the “correct” way through the firewall,
based on the packet’s source IP address upon ingress to the firewall, and the packet’s
destination IP address upon egress of the firewall. Antispoofing is a separate
enforcement mechanism that is consulted long before any policy layers. Based on the
recommendations in this chapter, you may need to make firewall topology adjustments to
ensure traffic is being inspected efficiently by the firewall. Antispoofing relies heavily
on the firewall’s topology definitions for proper enforcement. If you are not familiar
with the antispoofing feature or its ramifications, I’d strongly recommend checking out
the CheckMates post located here: A Primer on Anti-Spoofing.
Note that in R80.20 or later firewalls a new dynamic option for calculating
antispoofing topology for an interface has been introduced, called “Network defined by
routes”:
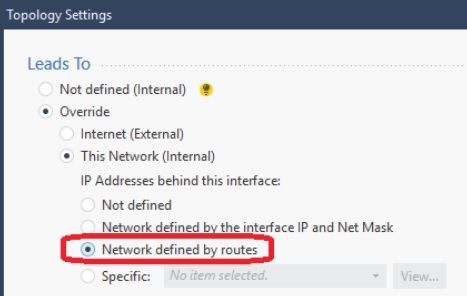
Figure 8-89: New “Network defined by routes” Setting on R80.20+ Firewalls
When selected this option will automatically define the topology for the interface
based on all directly-connected, static, and dynamic routes referencing that interface. So
therefore if any antispoofing issues are encountered, the actual problem is probably a
missing route which can be much easier to troubleshoot.
If you have inherited an existing firewall deployment, or are otherwise unfamiliar
with its network topology configuration, making sense of the firewall’s defined topology
from the SmartConsole GUI can be difficult. Nested network groups, a separate screen
for every interface, and a multitude of anti-spoofing related settings for each individual
interface can make forming a mental picture of your network and its topology a truly
daunting task. To make things even more difficult, the firewall’s topology cannot be
easily viewed from the Management CLI/API interface either.
However CheckMates user Danny Jung has created a special CLI tool called “One-
liner for Address Spoofing Troubleshooting” (which won an award for 2019 CheckMates
Code Hub Contribution of the Year) that provides a no-nonsense, text-based dump of the
firewall’s topology and associated antispoofing settings from the CLI. Not only is this
tool useful for troubleshooting antispoofing problems, but is great for figuring out the
actual working topology of your firewall. The tool is located at CheckMates here: One-
liner for Address Spoofing Troubleshooting.
WARNING: If you determine that there are missing interfaces in your
firewall’s topology definition, you might be tempted to click the “Get Interfaces” button
on the Network Management screen of the firewall object in the SmartConsole. But
before you do that, look carefully at the Get Interfaces button after clicking it. Note that
it provides two possible choices when left-clicked (“Get Interfaces With Topology” and
“Get Interfaces Without Topology”). Clicking the “Get Interfaces Without Topology”
menu choice is the appropriate one to use in this case to add any missing interfaces.
Clicking “Get Interfaces With Topology” will attempt to modify the interface topology
definition of all existing interfaces as well, which may impact anti-spoofing enforcement,
which could cause a huge outage and even disrupt your ability to manage the firewall!
Even if you choose the proper “Get Interfaces Without Topology” option, you should
ALWAYS manually verify the topology of ALL interfaces afterward prior to installing the
policy!
Should you find yourself cut off from managing or installing policy to the firewall
due to misconfigured anti-spoofing enforcement, run these expert mode commands on a
R80.30 Jumbo HFA Take 71+ firewall to disable antispoofing “on the fly”, and recover
the ability to install a corrected policy (the second line assumes that SecureXL is
currently enabled on the firewall):
fw ctl set int fw_antispoofing_enabled 0
fw ctl set int sim_anti_spoofing_enabled 0 -a



