- Products
- Learn
- Local User Groups
- Partners
- More
Call For Papers
Your Expertise, Our Stage
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
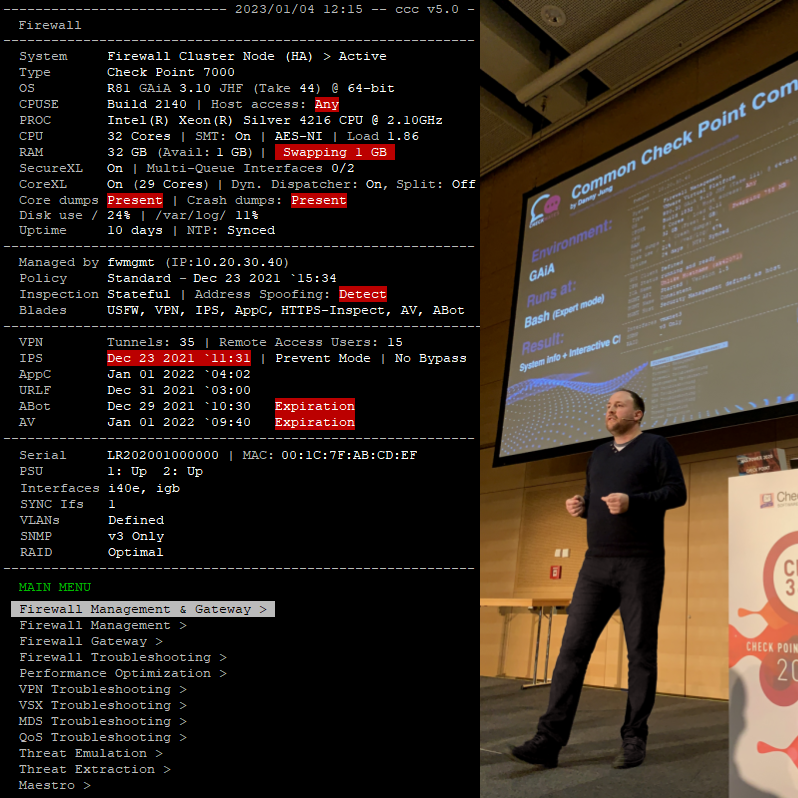
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle
Danny,
The CCC script is now pretty mature and perhaps it is possible to serve it from HTTPS with hash verification for installation from "Expert mode"?
Something along the lines of solution described here: https://stackoverflow.com/questions/2086424/creating-a-file-downloading-script-with-checksum-verific...
Regards,
Vladimir
Danny,
The CCC script is now pretty mature and perhaps it is possible to serve it from HTTPS with hash verification for installation from "Expert mode"?
Something along the lines of solution described here: https://stackoverflow.com/questions/2086424/creating-a-file-downloading-script-with-checksum-verification
Regards,
Vladimir
;@Vladimir: ccc is now served securely via HTTPS and uses SHA-512 to secure it's self-updates.
Secure Installation in expert mode :
src=`curl_cli -fsk https://dannyjung.de/ccc | zcat 2>/dev/null`; if [[ $? -eq 0 ]]; then if [[ `echo "$src" | sha512sum | cut -d " " -f 1` == `curl_cli -fsk https://dannyjung.de/ccc-sha512 | zcat` ]]; then echo "$src" > /usr/bin/ccc && chmod +x /usr/bin/ccc; else echo "SHA-512 doesn't match."; fi; else echo "No connection to dannyjung.de"; fi; unset src
@Vladimir: ccc is now served securely via HTTPS and uses SHA-512 to secure it's self-updates.
Secure Installation in expert mode :
src=`curl_cli -fsk https://dannyjung.de/ccc | zcat 2>/dev/null`; if [[ $? -eq 0 ]]; then if [[ `echo "$src" | sha512sum | cut -d " " -f 1` == `curl_cli -fsk https://dannyjung.de/ccc-sha512 | zcat` ]]; then echo "$src" > /usr/bin/ccc && chmod +x /usr/bin/ccc; else echo "SHA-512 doesn't match."; fi; else echo "No connection to dannyjung.de"; fi; unset src
This is great!
Do you intend on hosting CCC yourself or are there considerations to move it to Check Point in the future?
Hi Danny Sir,
I am gatting below error
[Expert@CP-R80.20:0]# ccc
-bash: /usr/bin/ccc: Permission denied
[Expert@CP-R80.20:0]#
@suhasbhoir make sure your permissions are set properly:
chmod +x /usr/bin/ccc
@suhasbhoir make sure your permissions are set properly:
chmod +x /usr/bin/ccc;
Hey Danny,
great tool. I recommend this to all my customers and use the tool almost every day.
Fantastic work!!!
Greetings Flo
Strange error with newest version:
MAIN < FIREWALL GATEWAY
execute first line:
fw stat; ips stat; fw stat -b AMW; cpstat -f all polsrv; cp_conf sic state Show FW + IPS/TP + Policy Server + SIC status
/usr/bin/ccc: eval: line 471: unexpected EOF while looking for matching ``'
/usr/bin/ccc: eval: line 472: syntax error: unexpected end of file
Done.
Strange error with newest version:
MAIN < FIREWALL GATEWAY
execute first line:
fw stat; ips stat; fw stat -b AMW; cpstat -f all polsrv; cp_conf sic state Show FW + IPS/TP + Policy Server + SIC status
/usr/bin/ccc: eval: line 471: unexpected EOF while looking for matching ``'
/usr/bin/ccc: eval: line 472: syntax error: unexpected end of file
Done.
;
Hi Danny,
Thank you for this great tool and keep it updated with more and more RFEs 🙂
Please consider adding the [ watch --i 1 --d 'cpstat -f fragments fw' ] to see if the GW is handling any fragmentation every sec.
Hi Bechor,
thanks for your support.
I'm working on an update that will cover all the requests regarding the watch command to be included.
Does using scripts like this or installing other 3rd parties packages (lets say Python) affect Vendor Support? Void it somehow?
The script seems to follow the normal (debug) commans you can find in SecureKnowledge.
No harm in using them. But as with every tool. You can also do some damage if you use it incorrectly.
I'm glad to announce that ccc is recommended in the book: 📕 Max Power 2020 by @Timothy_Hall .
I'm glad to announce that ccc is recommended in the book: 📕 Max Power 2020 by @Timothy_Hall .
;The PDF slides of my CPX 2020 presentation in Vienna, which features a ccc special, can be found here.
I can provide you with the PPTX version upon request.
Danny, this tool is fantastic thank you!
I know this may be an impossible task because I am not sure these commands exist but would love to see:
thanks
Danny, this tool is fantastic thank you!
I know this may be an impossible task because I am not sure these commands exist but would love to see:
thanks
;
Hi Danny,
long time no ccc install.
Today I installed ccc to a VSX R80.30 cluster and possibly I found a small bug.
The "shown blades" in the summary only shows "FW" even if there are more active blades.
More over:
ccc is showing that coreXL is off when running it on vsx.
This is correct, but somehow not the truth.
How about just showing "vsx" at corexl when ccc is detecting a vsx system?
Thanks for your efforts!
Cheers
Sven
Hi Danny,
long time no ccc install.
Today I installed ccc to a VSX R80.30 cluster and possibly I found a small bug.
The "shown blades" in the summary only shows "FW" even if there are more active blades.
More over:
ccc is showing that coreXL is off when running it on vsx.
This is correct, but somehow not the truth.
How about just showing "vsx" at corexl when ccc is detecting a vsx system?
Thanks for your efforts!
Cheers
Sven
;
Hi @Sven_Glock,
could you please tell me what enabled_blades is showing at your VSX host?
As for VSX and CoreXL, ccc is already showing that it's a VSX host, right?
Regards,
Danny
Hi @Sven_Glock,
could you please tell me what enabled_blades is showing at your VSX host?
As for VSX and CoreXL, ccc is already showing that it's a VSX host, right?
Regards,
Danny
I'm glad to announce that ccc is now officially credited in Check Point's GAiA HealthCheck script for checks courtesy of ccc. Thanks @Nathan_Davieau.
I'm glad to announce that ccc is now officially credited in Check Point's GAiA HealthCheck script for checks courtesy of ccc. Thanks @Nathan_Davieau.
;People who has to use proxy can use this command to get ccc:
curl_cli --proxy proxy:port -k https://dannyjung.de/ccc | zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc
People who has to use proxy can use this command to get ccc:
curl_cli --proxy proxy:port -k https://dannyjung.de/ccc | zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc
;New version 4.7 released!
+ Added support for Maestro
thanks to @Laszlo_Csosza , @Anatoly Masover, @Tom_Hartig & Ilia Anokhin for training
thanks to @Maarten_Sjouw for testing and his Maestro basic setup documentation
greetings to all Maestro experts, @Evgeniy_Olkov [1,2], @Lari_Luoma, @Tomas_Vobruba, @Summer_Kablawi, @Vinicius_Figuei, @AndyY, @Liran_Abir etc.
+ Integrated the One-liner for Remote Access VPN Statistics
+ Added support for upcoming Check Point release R81
New version 4.7 released!
+ Added support for Maestro
thanks to @Laszlo_Csosza , @Anatoly Masover, @Tom_Hartig & Ilia Anokhin for training
thanks to @Maarten_Sjouw for testing and his Maestro basic setup documentation
greetings to all Maestro experts, @Evgeniy_Olkov [1,2], @Lari_Luoma, @Tomas_Vobruba, @Summer_Kablawi, @Vinicius_Figuei, @AndyY, @Liran_Abir etc.
+ Integrated the One-liner for Remote Access VPN Statistics
...;ccc is typically installed on all types of Check Point Gaia based systems. This includes management servers, gateways, clusters, VSX environments and even Maestro Hyperscale solutions. Embedded Gaia (SMB) is not supported yet.
ccc is typically installed on all types of Check Point Gaia based systems. This includes management servers, gateways, clusters, VSX environments and even Maestro Hyperscale solutions. Embedded Gaia (SMB) is not supported yet.
;About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
