- Products
- Learn
- Local User Groups
- Partners
- More
Call For Papers
Your Expertise, Our Stage
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
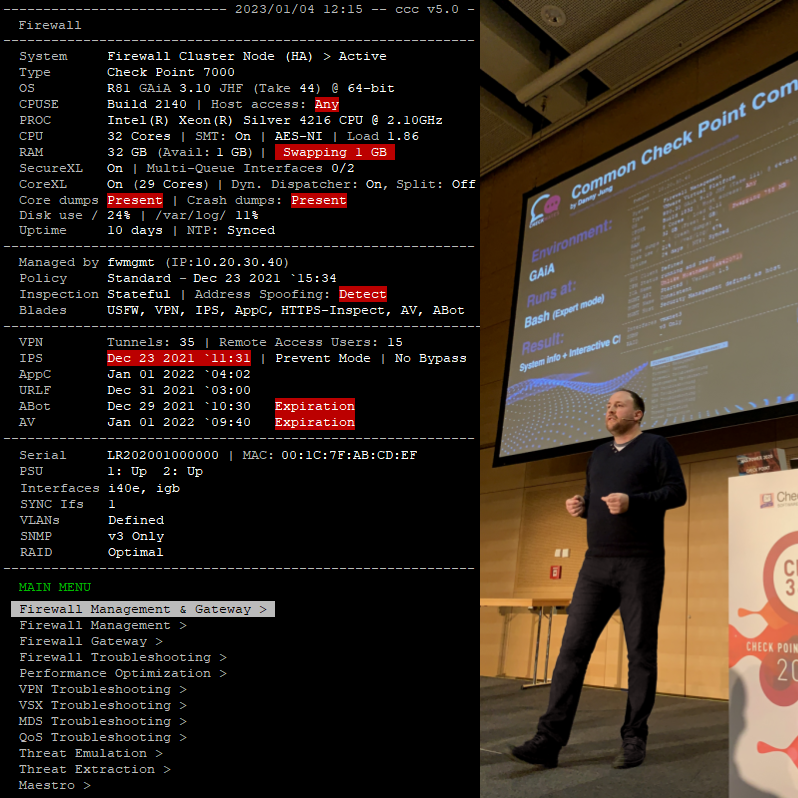
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle
Found hcp in the new version - brilliant! But the post looks like it needs to load all replies to see the newest, sort order does not matter - @PhoneBoy ?
Hi @Danny ,
thanks for the mega script. I use this on all the firewalls I use.
I am currently evaluating our firewalls for the CIS benchmark and configuring them according to best practices. --> https://www.cisecurity.org/benchmark/checkpoint_firewall
Many checks are simple config queries with show and are already built in with you.
As we talked at CPX in Vienna it would be mega helpful for me if I could automate the whole thing and query everything with one command.
If there are others who can do this and you find it helpful, I would be delighted if you could integrate it.
This is how I could imagine the integration:
Firewall Management & Gateway >
-- Gaia Health Check --------------------------------------------------------------------------
Show CIS Benchmark
Export CIS Benchmark results to CSV
The following information is checked:
1 Password Policy ......................................................................................................................................... 10
1.1 Ensure Minimum Password Length is set to 14 or higher (Automated) ........... 11
1.2 Ensure Disallow Palindromes is selected (Automated) ........................................... 13
1.3 Ensure Password Complexity is set to 3 (Automated) .............................................. 15
1.4 Ensure Check for Password Reuse is selected and History Length is set to 12 or more (Automated) ..........17
1.5 Ensure Password Expiration is set to 90 days (Automated) .................................. 19
1.6 Ensure Warn users before password expiration is set to 7 days (Automated) ............... 21
1.7 Ensure Lockout users after password expiration is set to 1 (Automated) ....... 23
1.8 Ensure Deny access to unused accounts is selected (Automated) ....................... 25
1.9 Ensure Days of non-use before lock-out is set to 30 (Automated) ...................... 27
1.10 Ensure Force users to change password at first login after password was changed from Users page is selected (Automated) ... 29
1.11 Ensure Deny access after failed login attempts is slected (Automated) ......... 31
1.12 Ensure Maximum number of failed attempts allowed is set to 5 or fewer (Automated) ..................... 33
1.13 Ensure Allow access again after time is set to 300 or more seconds (Automated) ............... 35
2 Device Setup ................................................................................................................................................ 37
2.1 General Settings ................................................................................................................................. 38
2.1.1 Ensure 'Login Banner' is set (Automated) ................................................................. 38
2.1.2 Ensure 'Message Of The Day (MOTD)' is set (Automated) .................................. 40
2.1.3 Ensure Core Dump is enabled (Automated) .............................................................. 42
2.1.4 Ensure Config-state is saved (Automated) ................................................................. 44
2.1.5 Ensure unused interfaces are disabled (Automated) ............................................ 45
2.1.6 Ensure DNS server is configured (Automated) ........................................................ 47
2.1.7 Ensure IPv6 is disabled if not used (Automated) .................................................... 49
2.1.8 Ensure Host Name is set (Automated)......................................................................... 50
2.1.9 Ensure Telnet is disabled (Automated) ....................................................................... 51
2.1.10 Ensure DHCP is disabled (Automated) ..................................................................... 53
2.2 SNMP ...................................................................................................................................................... 55
2.2.1 Ensure SNMP agent is disabled (Automated) ........................................................... 55
2.2.2 Ensure SNMP version is set to v3-Only (Automated) ............................................ 57
2.2.3 Ensure SNMP traps is enabled (Automated) ............................................................. 59
2.2.4 Ensure SNMP traps receivers is set (Automated) ................................................... 61
2.3 NTP ......................................................................................................................................................... 63
2.3.1 Ensure NTP is enabled and IP address is set for Primary and Secondary NTP server (Automated) .............. 63
2.3.2 Ensure timezone is properly configured (Automated) ......................................... 65
2.4 Backup ................................................................................................................................................... 67
2.4.1 Ensure 'System Backup' is set. (Automated) ............................................................. 67
2.4.2 Ensure 'Snapshot' is set (Automated) .......................................................................... 69
2.4.3 Configuring Scheduled Backups (Manual) ................................................................. 71
2.5 Authentication Settings................................................................................................................... 72
2.5.1 Ensure CLI session timeout is set to less than or equal to 10 minutes (Automated) ................. 72
2.5.2 Ensure Web session timeout is set to less than or equal to 10 minutes (Automated) ............ 74
2.5.3 Ensure Client Authentication is secured. (Automated) ......................................... 76
2.5.4 Ensure Radius or TACACS+ server is configured (Automated) ......................... 78
2.5.5 Ensure allowed-client is set to those necessary for device management (Automated) ............... 80
2.6 Logging .................................................................................................................................................. 82
2.6.1 Ensure mgmtauditlogs is set to on (Automated) ..................................................... 82
2.6.2 Ensure auditlog is set to permanent (Automated) ................................................. 84
2.6.3 Ensure cplogs is set to on (Automated) ...................................................................... 86
3 Firewall Secure Settings .......................................................................................................................... 87
3.1 Enable the Firewall Stealth Rule (Automated) ............................................................ 88
3.2 Configure a Default Drop/Cleanup Rule (Automated) .............................................. 89
3.3 Use Checkpoint Sections and Titles (Manual) .............................................................. 91
3.4 Ensure Hit count is Enable for the rules (Automated) .............................................. 92
3.5 Ensure no Allow Rule with Any in Destination filed present in the Firewall Rules (Automated) ......... 93
3.6 Ensure no Allow Rule with Any in Source filed present in the Firewall Rules (Automated) ............. 94
3.7 Ensure no Allow Rule with Any in Services filed present in the Firewall Rules (Automated) ............ 95
3.8 Logging should be enable for all Firewall Rules (Manual) ...................................... 96
3.9 Review and Log Implied Rules (Automated) ................................................................ 97
3.10 Ensure Drop Out of State TCP Packets is enabled (Automated) ......................... 98
3.11 Ensure Drop Out of State ICMP Packets is enabled (Automated) ...................... 99
3.12 Ensure Anti-Spoofing is enabled and action is set to Prevent for all Interfaces (Automated) .......... 100
3.13 Ensure Disk Space Alert is set (Automated) ............................................................. 102
3.14 Ensure Accept RIP is not enabled (Automated) ...................................................... 103
3.15 Ensure Accept Domain Name over TCP (Zone Transfer) is not enabled (Automated) ....... 105
3.16 Ensure Accept Domain Name over UDP (Queries) is not enabled (Automated) ......... 107
3.17 Ensure Accept ICMP Requests is not enabled (Automated) ............................... 109
3.18 Ensure Allow bi-directional NAT is enabled (Automated) ................................. 110
3.19 Ensure Automatic ARP Configuration NAT is enabled (Automated) .............. 112
3.20 Ensure Logging is enabled for Track Options of Global Properties (Automated) .......... 113
The document also describes exactly what should be queried and what is best configured.
Query some examples:
show password-controls min-password-length
show password-controls palindrome-check
show password-controls complexity
show password-controls history-checking
show password-controls password-expiration
show password-controls expiration-warning-days
show password-controls expiration-lockout-days
show password-controls deny-on-nonuse enable
show password-controls deny-on-nonuse allowed-days
show password-controls force-change-when
show password-controls deny-on-fail enable
show password-controls deny-on-fail failures-allowed
show password-controls deny-on-fail allow-after
show configuration message
show core-dump status
show config-state
show interfaces all
show dns primary
show dns secondary
show dns tertiary
show ipv6-state
show hostname
show net-access telnet
show dhcp server status
show snmp agent
show snmp agent-version
show snmp traps enabled-traps
show snmp traps receivers
show ntp active
show ntp servers
show timezone
show backup last-successful
show snapshots
show inactivity-timeout
show web session-timeout
more $FWDIR/conf/fwauthd.conf
show aaa tacacs-servers state
show aaa tacacs-servers list
show allowed-client all
show syslog mgmtauditlogs
show syslog auditlog
show syslog cplogs
feel free to contact me if you need further information
Thanks and Regards
Hi @Danny ,
thanks for the mega script. I use this on all the firewalls I use.
I am currently evaluating our firewalls for the CIS benchmark and configuring them according to best practices. --> https://www.cisecurity.org/benchmark/checkpoint_firewall
Many checks are simple config queries with show and are already built in with you.
As we talked at CPX in Vienna it would be mega helpful for me if I could automate the whole thing and query everything with one command.
If ther
...;About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
