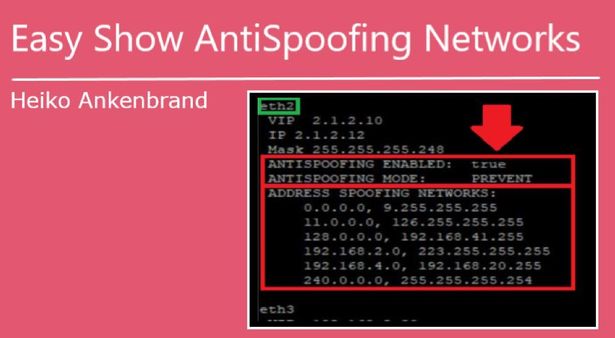
I've modified slightly to improve internal code styling (consistent use of spaces in pipelines, for example) and to improve code correctness (I have an incredibly weird firewall which hits basically every edge case ever; this version works on it). One specific correctness change I made was wrapping the "VIP" section in a test to see if we're on a cluster in the first place. That whole line should now be silently omitted when run on a non-clustered firewall.
The other big one relates to the awk nightmare in the middle. The problem I ran into is $FWDIR/state/local/FW1/local.set contains data for both members of a cluster, not just the member you're on. Rather than dumping the contents and parsing them repeatedly, I try to get just the lines for the interface we want, and just on the member we're running on. My awk-fu is weak, so I'm sure that expression's correctness can be improved. Still, it's a bit better than just deduplicating, since interfaces can have different exact configuration. This is the expression I was playing with before I had to put this down for a while:
awk "/^: \(@$/,(/^: \([^\)]+$/ && ! /^: \(@$/)" $FWDIR/state/local/FW1/local.set
It returns both instances of the interface from the local.set file, and I'm not sure yet how to filter it to just the one I want.
Here is my modified version of the whole script as a one-liner:
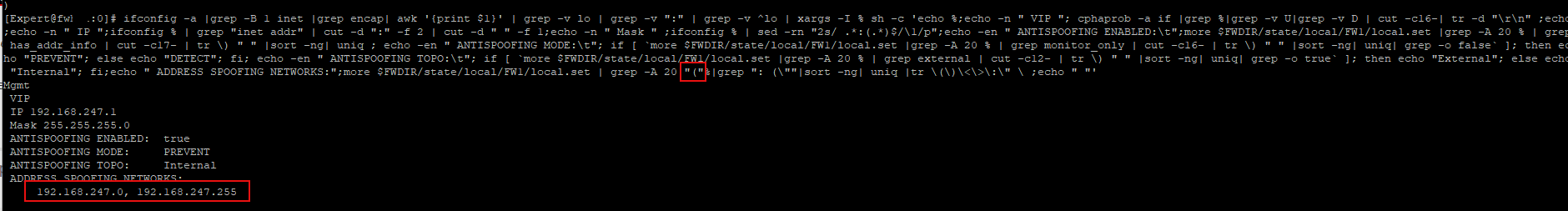
interfaceAddress="";interfaceData="";ifconfig -a | grep -B 1 inet | grep encap | awk '{print $1}' | grep -v lo | grep -v ":" | xargs -I @ sh -c 'echo @;if [ $(cpprod_util FwIsHighAvail) -ne 0 ]; then printf " VIP %s\n" $(cphaprob -a if | egrep "^@ +[0-9]" | awk "{print $2}");fi;interfaceAddress=$(ifconfig "@" | grep "inet addr" | cut -d ":" -f 2 | cut -d " " -f 1);printf " IP %s\n" $interfaceAddress;printf " Mask %s\n" $(ifconfig "@" | sed -rn "2s/ .*:(.*)$/\1/p");interfaceData=$(awk "/^:ipaddr \(${interfaceAddress}\)/,/^:mss_value \([0-9]+\)/" $FWDIR/state/local/FW1/local.set);echo -en " ANTISPOOFING ENABLED:\t";echo "${interfaceData}" | grep has_addr_info | cut -c17- | tr \) " ";echo -en " ANTISPOOFING MODE:\t";echo "${interfaceData}" | grep monitor_only | grep false > /dev/null;if [ "$?" -eq 0 ];then echo "Prevent";else echo "Detect";fi;echo -en " ANTISPOOFING TOPO:\t";echo "${interfaceData}" | grep external | grep true > /dev/null;if [ "$?" -eq 0 ];then echo "External";else echo "Internal";fi;echo " ADDRESS SPOOFING NETWORKS:";echo "${interfaceData}" | grep ": (\"" | sort -ng | uniq | tr \(\)\<\>\:\" \ ;echo ""'
The attached text file is the same script broken out into many lines to make the internal logic flow more obvious.