- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Vulnerabilities detected by VA scan
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vulnerabilities detected by VA scan
Hi All,
Recently we did a VA scan on one of our SMB device and there is one vulnerabilities listed below:
"Diffie-Hellman Ephemeral Key Exchange DoS Vulnerability (SSH, D(HE)ater) (CVSS: 7.5)"
I did not found any related fix on the SK but I went on some research, it seems like need to disable the Diffie-Hellman Key exchange method in the file name "sshd_config".
For normal appliance the path for "sshd_config" file will be /etc/ssh/sshd_config
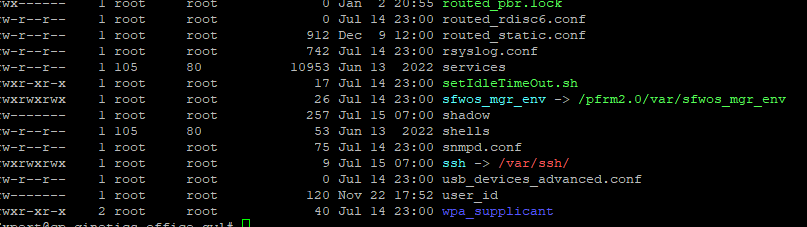
But for SMB, screenshot below is what I got when trying to find the file:
It seems like the "ssh" has a symbolic link to "/var/ssh/" but the "ssh" folder is not in the "/var".
Does anyone has any idea on this?
Appreciate for the help!
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
check this
Expert# cpwd_admin list
APP PID STAT #START START_TIME MON COMMAND
SSHD 3554 E 1 [13:26:19] 3/12/2023 N /pfrm2.0/bin/sshd -f /pfrm2.0/etc/sshd_config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
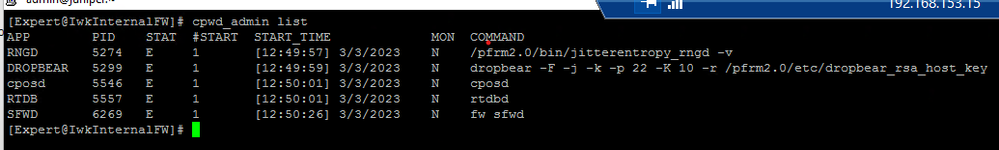
Hi Martin,
This is all I'm able to see when running cpwd_admin list command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Only in the most recent SMB firmware releases (R81.10.xx) is OpenSSH used.
In other releases, Dropbear is used as the SSH daemon, which means the procedure for remediating this would be different (assuming it's even possible to do so).
In our official SK, SMB appliances aren't mentioned at all: https://support.checkpoint.com/results/sk/sk181833
In any case, please open a TAC case: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @PhoneBoy,
We did checked the SMB firmware is installed with version R81.10.00.
I think I will proceed to open a TAC case for this
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Do anyone knows how to restart the SSHD service in a SMB device? Because I did some changes on the sshd file and I wanted to restart the service and try will the file take effect or not
Thanks alot!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a supported way to configure this for SMB since 81.10.05:
[Expert@fifteenfifty]# clish
fifteenfifty> show ssh-
ssh-cipher - OpenSSH Cipher encryption
ssh-kex - OpenSSH KEX encryption
ssh-mac - OpenSSH MAC encryption
fifteenfifty> show ssh-cipher
aes128-ctr
aes192-ctr
aes256-ctr
fifteenfifty> show ssh-mac
hmac-sha1
hmac-sha2-256
hmac-sha2-512
fifteenfifty> show ssh-kex
curve25519-sha256
curve25519-sha256@libssh.org
ecdh-sha2-nistp521
ecdh-sha2-nistp384
ecdh-sha2-nistp256
diffie-hellman-group14-sha256
diffie-hellman-group14-sha1
diffie-hellman-group16-sha512
diffie-hellman-group18-sha512
diffie-hellman-group-exchange-sha256
delete ssh-<encryption-category> algorithm <algorithm>
Example:
|
|
In lower firmware version there is no possibility to exclude a cipher, MAC or KEX as it uses dropbear created for embedded devices...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @G_W_Albrecht,
This is what I'm looking for. Thank you so much on this.
And I have another thing is that the vulnerability tools also scanned vulnerability related to the CVE-2023-48795 on port 22, which is the "chacha20-poly1305" cipher.
Is the cipher need to disable by using the "cipher_util"? Because I can't seems to find it when using the "show ssh-cipher" command when list out all the ciphers for the SMB device.
Found the sk181833 but I think it is for Enterprise appliances and it did not officially mention it is applicable for SMB device.
Any idea on this?
Appreciate for the help.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter