- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- VPN S2S between CPX 6000 and CPX 1500
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN S2S between CPX 6000 and CPX 1500
Hi experts,
Today it was imposible to setup a VPN S2S between a SG 6000 and a SMB SG 1500. The SG 6000 was managed by a SMS, and the SG 1500 was a standalone deployment. I configured the meshed VPN community on SG 6000, how do I define the SG 1500 object? As a interoperable device? Check Point Host? Gateway? Or externally managed VPN Gateway? I defined it as a interoperable device, and used a shared secret, as it was a third party VPN device, is this correct? Because I didn't find an option to use their CPX certificates. The tunnel remained in Phase 1:
A strange thing is with the "vpn tu" command, I saw an unknown peer (192.168.50.1), who is this peer?
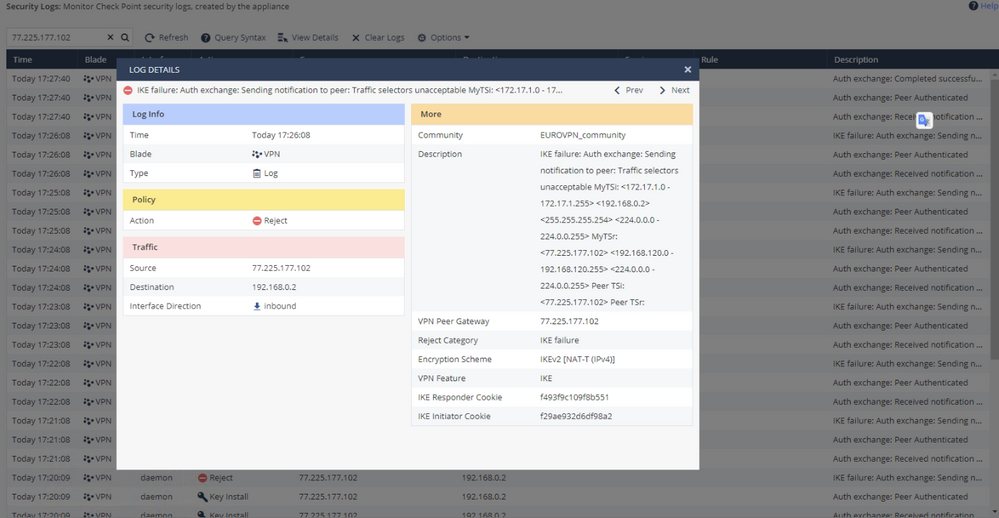
At the SMB SG 1500 I saw this log:
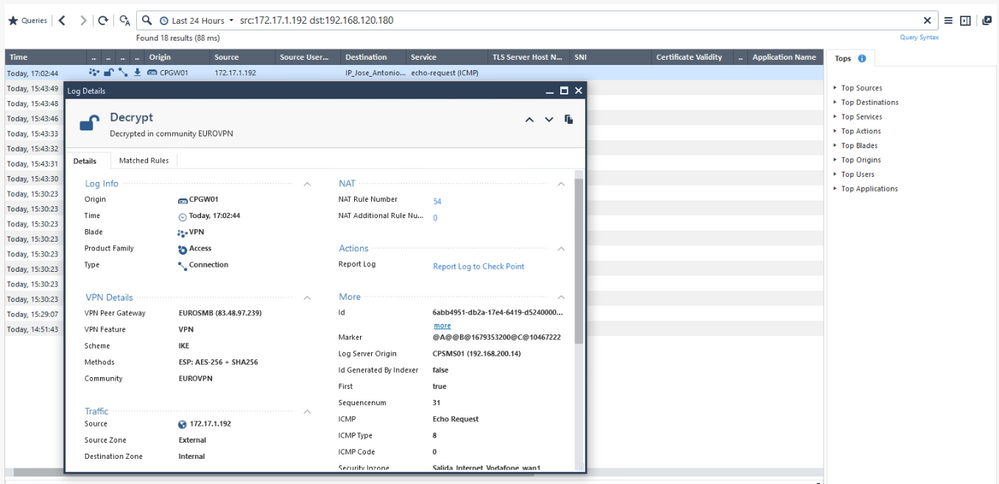
And the strange thing is in the SG 6000, I see traffic I made with ping tests going through the VPN tunnel, which is fine, but the tunnel remains in phase 1:
Maybe the SMB SG 1500 device is not properly configured, I never configured one of them and it has some VPN options I didn't understand (i. e. peer ID for IKEv2).
Can someone shed some light on this? Please your help.
Regards,
Julián
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi everyone,
Still investigating. One more question. How can I know which peer initiates the tunnel? How can I force what peer initiates the tunnel?
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The vpn is started when some traffic is generated from any of the peers. So if the vpn is down, no traffic at all, yo do a ping from a host behind SG6000, so SG6000 will initiate the tunnel, and vice versa.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
About peer 192.168.50.1, it says it is a user, so some vpn client is connected and that office mode IP address was asigned.
You should define the object as a externally managed vpn gateway.
About the log on 1500, you can check the problem are VPN domains not maching between the peers. Make sure the configuration about encryption domains are matching both sides.
About the log on SG1600. I know it should happen but it is very common that you see encrypt logs when the vpn is not fully operational yet. You should filter logs by action:"Key Install" and X.X.X.X where that is the public ip address of the remote peer.
So your problem are encryption domains, fix them and change the remote peer object to externally managed vpn gateway.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi RS_Daniel,
Many thanks for your answer. I will check and let you know.
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey mate,
You can also run vpn tu tlist -p peer_ip command to see what it shows. Did you try running ike debug at all? Is it failing on phase 1 or 2 at the moment? If its phase 2, then as @RS_Daniel , that usually indicated enc domain issue.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi guys,
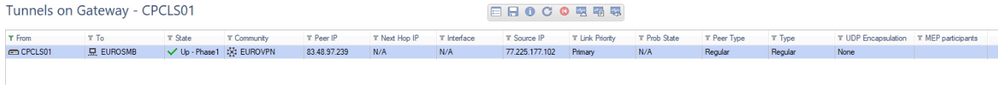
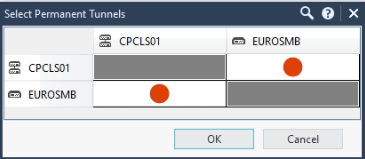
Finally I managed to set up the tunnel between the peers. It run OK for some days, but customer called me and sayed that the tunnel is not steady and had some disconnections. What I have made is to convert this tunnel in a permanent tunnel, and now I can see it in Logs & Monitor > Tunnel & User Monitoring > Permanent Tunnels. Also in SmartLog I can see UDP 4500 logs every 40 seconds between the peers, I guess this is a kind of keepalive to make it permanent. I would like to know if my configuration is OK for permanent tunnel.
This is for CPX 6000 side:
(Not sure what's the meaning of the red dots and grey rectangules...)
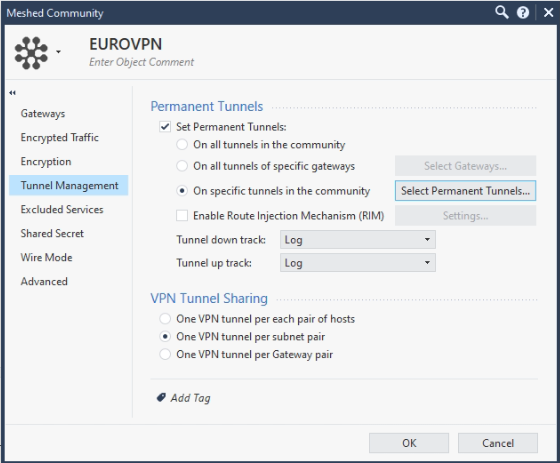
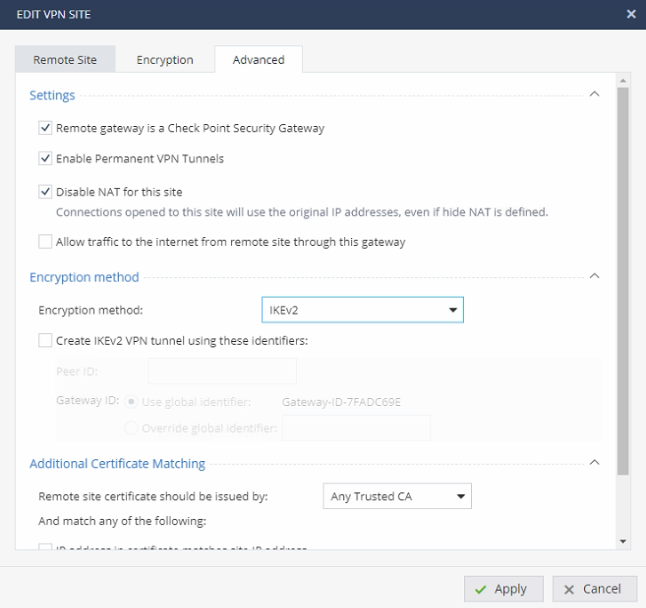
An this is for CPX 1500 side:
I don't find an option in the CPX 6000 to enable DPD... in CPX 1500 is a simple click as you see in the previous image.
Thanks in advance,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
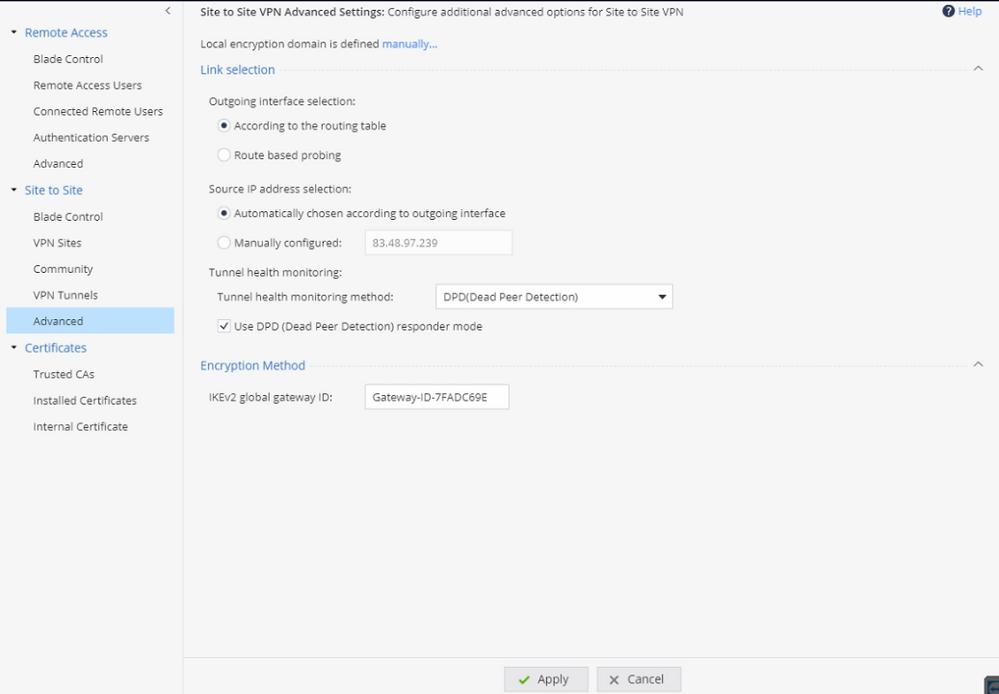
Permanent tunnel will use tunnel_test (UDP/18234), if you want to use DPD there are modifications to be done.
Since both systems are CP, you could select the Check Point proprietary method on the Spark side and not DPD.
It's all explained here: Tunnel Management (checkpoint.com)
I believe you can also keep the Permanent tunnel option active for all gateways in the community in your case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you have a chance to test the instructions in sk109139 ? How to configure Site-to-Site VPN between Locally Managed Embedded GAIA appliance and Centrally Mana... which is a option to use CAs for VPN between Maintrain Gaia and a locally managed SMB gateway.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter