- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure the Workspace)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The New Quantum DDoS Protector
Integration with Playblocks
Keep Your Networking Peers Happy
With Secure SD-WAN
Infinity Events Improvements
Help us with the Short-Term Roadmap
Secure the GenAI Revolution!
The All-New GenAI Security from Check Point
CheckMates Toolbox Contest 2024
Make Your Submission for a Chance to WIN up to $300 Gift Card!
CheckMates Go:
Harmony Endpoint -- What's New and Deployment
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- SMB Gateways (Spark)
- :
- Re: Site to Site IPsec VPN with Strongswan
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Site to Site IPsec VPN with Strongswan
Dear All,
I'm trying to create IPsec tunnel with Strong Swan with below configuration.
Left Side is Strong Swan
Right Side is Checkpoint R81.10.10(945)
--------------------------
conn ho
type=tunnel
auto=start
keyexchange=ikev2
authby=secret
left=%defaultroute
leftid=13.126.xx.xx
leftsubnet=10.90.0.0/20
right=59.94.xx.xx
rightid=%any
rightsubnet = 192.168.10.0/26
ike=aes256-sha256-modp1024!
esp=aes256-sha256!
aggressive=no
forceencaps=yes
leftauth=psk
rightauth=psk
keyingtries=%forever
ikelifetime=28800s
lifetime=3600s
dpddelay=20s
dpdtimeout=120s
dpdaction=restart
------------------------------
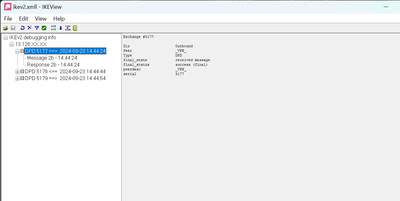
Checkpoint config screenshot attached.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We need more info. Where does it fail, phase 1, phase 2? Did you do any tcpdumps, debugs? Also, any relevant logs would help, for sure.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
will check later.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Informational exchange: Sending notification to peer: Invalid IKE SPI IKE SPIs: 0faf1db83dbbed18:f534262a58300b19, Refer to sk181787 for elaboration on this reason
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just had a quick look and I see below messages. I would make sure everything in phase 1 is matching, including pSK, because there are only so many things that could be mismatched. Also, is this supposed to be permanent tunnel or not? I ask because it shows DPD errors.
Andy
Line 707: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 13.126.XX.XX returned obj: 0x91d1ee8
Line 716: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 717: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 13.126.XX.XX returned obj: 0x91d1ee8
Line 718: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] canonize_gw: Canonized ip is the same as original ip 13.126.XX.XX
Line 721: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][tunnel] UDPConnection::UDPConnection: Enter (copy ctor) peer: 13.126.XX.XX
Line 728: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] ikeExchangeFlowHandler::createResponderExchange: entering. peer: 13.126.XX.XX, peer_ip: 13.126.XX.XX, my_ip: 59.94.XX.XX, port: 4500, local_os_ifn: 0, local_ifn: -1
Line 735: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] peer: (ext addr: 13.126.XX.XX). peer_ip: 0.0.0.0 Using port 4500
Line 741: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] doCreateOrder: enter with peer 13.126.XX.XX peer_ip 13.126.XX.XX
Line 742: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] ikev2Mediator::getIKEPeerObj: entering: ipaddr 13.126.XX.XX
Line 743: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 744: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 13.126.XX.XX returned obj: 0x91d1ee8
Line 749: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] ikeSimpOrder::createVpnDbHandle: found a common community with 13.126.XX.XX. Not using granular crypto settings.
Line 755: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] ikeSimpOrder::setIPs: Set Peer: 13.126.XX.XX, IP to use: 13.126.XX.XX
Line 756: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] ikeSimpOrder::setTunnelIPs: Peer: 13.126.XX.XX, My_ip: 0.0.0.0 Peer_ip: 0.0.0.0, local_ifn -1, local_os_ifn 0
Line 806: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] peer: (ext addr: 13.126.XX.XX). peer_ip: 0.0.0.0 Using port 4500
Line 819: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] peer: (ext addr: 13.126.XX.XX). peer_ip: 0.0.0.0 Using port 4500
Line 836: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] canonize_gw_legacy: enter 13.126.XX.XX
Line 837: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 869: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][io] [SOCKETS][IKE]: Sending 84 IKE bytes to 13.126.XX.XX
Line 870: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:44][ikev2] ikev2Mediator::sendPacket: Sent 80 bytes using NAT-T (IPv4) to 13.126.XX.XX
Line 1052: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] tnlmon_transmitter_cb: entering: key <13.126.XX.XX, 1>
Line 1054: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] canonize_gw_legacy: enter 13.126.XX.XX
Line 1055: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 1057: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] tnlmon_transmitter_cb: Gateway IP is: 13.126.XX.XX
Line 1058: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] tnlmon_transmitter_cb: try to send DPD Request to GW 13.126.XX.XX
Line 1059: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] tnlmon_transmitter_cb: pKey->gateway:13.126.XX.XX, pKey->type:1, timeout:30
Line 1060: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] send_dpd: entering: peer 13.126.XX.XX, transmitter_interval 30
Line 1061: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] get_dpd_initiator_peers_hash: search for peer 13.126.XX.XX
Line 1062: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] get_dpd_initiator_peers_hash: found peer 13.126.XX.XX in dpd_initiator_peers hash
Line 1064: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] get_dpd_initiator_peers_hash: search for peer 13.126.XX.XX
Line 1065: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] get_dpd_initiator_peers_hash: found peer 13.126.XX.XX in dpd_initiator_peers hash
Line 1066: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] update_peer_in_dpd_initiator_peers_hash: peer 13.126.XX.XX, call CB: 1
Line 1067: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 1068: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 13.126.XX.XX returned obj: 0x91d1ee8
Line 1075: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] send_dpd_notification: entering: peer 13.126.XX.XX
Line 1076: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] get_dpd_initiator_peers_hash: search for peer 13.126.XX.XX
Line 1077: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][tunnel] get_dpd_initiator_peers_hash: found peer 13.126.XX.XX in dpd_initiator_peers hash
Line 1078: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 1079: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 13.126.XX.XX returned obj: 0x91d1ee8
Line 1084: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][ikev2] invoke_send_DPD: enter with peer: 13.126.XX.XX peer_ip: inx invalid type (0) my_ip: inx invalid type (0) local_ifn: -1
Line 1085: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][ikev2] ikev2Mediator::getSPIsByPeer: looking in peer_ikesa table for: <peer=13.126.XX.XX, user_hash=0, local_ifn=-1, peer_ip=inx invalid type (0)> ip_type=1
Line 1092: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][ikev2] peer: (ext addr: 13.126.XX.XX). peer_ip: 0.0.0.0 Using port 4500
Line 1098: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][ikev2] ikeExchangeFlowHandler::SendDPD: Send DPD to peer 13.126.XX.XX and SPIs a62a8a4d6eb13b93:0cbf35aa7f2baf9f, timeout is 30
Line 1099: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][ikev2] doCreateOrder: enter with peer 13.126.XX.XX peer_ip 0.0.0.0
Line 1100: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54][ikev2] ikev2Mediator::getIKEPeerObj: entering: ipaddr 13.126.XX.XX
Line 1101: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] GetEntryXIsakmpObjectsHash: received ipaddr: 13.126.XX.XX as key, found fwobj: AWS_VPN_BSNL
Line 1102: [iked 11923 4156895088]@AMALCO-HO[23 Sep 14:44:54] fwipsechost_from_ipxaddr: calling GetEntryXIsakmpObjectsHash for 13.126.XX.XX returned obj: 0x91d1ee8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes,This is permanent tunnel.
What we can do to match or identify the exact issue with Phase 2.
Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ANANTADSULE Ping me directly if you like, we can do remote session...Im just studying for Microsoft exam I have tomorrow, but I can help, not an issue.
Let me know.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I cant sadly paste the content of the sk, as it would violate community policies, but I had a quick look at it and it pretty much alligns with what I mentioned in my last response to check settings for phase 1, that they match on both ends.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You still can post a link to that SK, or just it's ID
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the link. @ANANTADSULE , if you can access it, you can check that error mentioned, but as I mentioned, it pretty much boils down to making sure everything in phase 1 matches on both ends.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey guys,
Just to update quick, I had remote with Anant and below is what we observed.
-tunnel shows as UP on both sides
-on CP 1500 smb appliance, running vpn tu list peer_ike and peer_ipsec flags show entries, meaning both phase 1 and 2 are working
-now, through rules are there and vpn domains are 100% correct, all works from strongswan side, but NOT cp end, log shows according to policy, packet should not have been decrypted
Since there is built in gui vpn debug tool, probably good idea to give that a go. I also advised to try reset tunnel on both ends.
@ANANTADSULE , if you could, I would also reboot smb after hours.
Alternatively, I would also open TAC case and see what they say. Sorry mate, wish I was more skilled with smb appliances...
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear all,
I have opened case ID 6-0004079065 with TAC & hope for quicker resolution.
I also request you all the experts and checkpoint team to support in this issue.
Thanks Andy for your valuable time.
Your help is highly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any time man, I am always happy to do remote. Please show TAC things we checked over zoom, I believe its important.
Best,
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 08 Oct 2024 @ 03:00 PM (AEDT)
No Suits, No Ties: Vulnerabilities and workarounds, a story of compromise (APAC)Tue 08 Oct 2024 @ 10:00 AM (CEST)
No Suits, No Ties: Vulnerabilities and workarounds, a story of compromise (EMEA)Tue 08 Oct 2024 @ 11:00 AM (EDT)
No Suits, No Ties: Vulnerabilities and workarounds, a story of compromise (Americas)Wed 09 Oct 2024 @ 05:00 PM (CEST)
TechTalk: The New Quantum DDoS Protector Integration with PlayBlocksThu 10 Oct 2024 @ 10:00 AM (CEST)
Beyond Endpoint: The future of Security with EPP, EDR & XDR - EMEAThu 10 Oct 2024 @ 05:00 PM (CEST)
Beyond Endpoint: The future of Security with EPP, EDR & XDR - AmericasTue 08 Oct 2024 @ 03:00 PM (AEDT)
No Suits, No Ties: Vulnerabilities and workarounds, a story of compromise (APAC)Tue 08 Oct 2024 @ 10:00 AM (CEST)
No Suits, No Ties: Vulnerabilities and workarounds, a story of compromise (EMEA)Tue 08 Oct 2024 @ 11:00 AM (EDT)
No Suits, No Ties: Vulnerabilities and workarounds, a story of compromise (Americas)Wed 09 Oct 2024 @ 05:00 PM (CEST)
TechTalk: The New Quantum DDoS Protector Integration with PlayBlocksThu 10 Oct 2024 @ 10:00 AM (CEST)
Beyond Endpoint: The future of Security with EPP, EDR & XDR - EMEAThu 10 Oct 2024 @ 05:00 PM (CEST)
Beyond Endpoint: The future of Security with EPP, EDR & XDR - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter