- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Nintendo switch doesn't work properly
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nintendo switch doesn't work properly
I have a 600 getting its Internet connection through a Motorola SB6141 modem. Behind the 600, via wireless, is a Nintendo Switch. The Switch can get online, but the connection test says that it's NAT Type C (which is just a Nintendo ranking for below A and B, and means online gaming won't work). Nintendo support as well as many forums online give various solutions, such as port forwarding all UDP ports to the Switch. I have done that on the 600 via NAT/firewall rules and I've even hooked a wireless AP to the DMZ port on the 600 and had the Switch connect through that... still no dice. The 600 doesn't have the ability to do a packet capture where you can see packets that are passed/dropped, so I can't even tell what is happening when I initiate the network test on the Switch. Does anyone have any ideas?
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes it does, using tcpdump or fw monitor via expert mode.
For what it's worth, I also tried making this work recently and wasn't successful.
Nintendo has not made any effort in recent years to improve its support for NAT, requiring an unacceptable number of ports to be forwarded.
For what it's worth, I also tried making this work recently and wasn't successful.
Nintendo has not made any effort in recent years to improve its support for NAT, requiring an unacceptable number of ports to be forwarded.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is expert mode? I mustn't know how to get there...
As for the Switch, I've determined the actual problem: double NAT. I didn't think I had that situation because the 600 kind of lies to me, but upon digging I found that my dumb DOCSIS modem (Motorola SurfBoard 6141) creates an internal network in the 192.168.100/24 range for the single ethernet port. That means the ethernet connection between the 600 and the modem is in the 192.168.100/24 network while my network behind the 600 is 192.168.0/24. So it is, in fact, double NATting. I would have expected the 600 to show the internet address as what it sees on the other end of the wire, 192.168.100.1, but since it shows the real public IP on the other side of the modem I was confused for quite some time.
What bothers me is I haven't been able to find a way to utilize the DMZ port on the 600 to put devices on the network on the WAN side, which should be the 192.168.100/24 network.
So the ultimate fix is going to be buying a new DOCSIS modem that has "bridge mode" so it won't create that stupid middleman network between the modem and the 600.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Production documentation is here: https://sc1.checkpoint.com/documents/R77.20.80/600_700_AdminGuide/html_frameset.htm
The DMZ port on the 600 should not be confused with what the "DMZ" mode does on a typical consumer router, which is basically "forward all ports".
In this case, it's the enterprise definition of a DMZ: a different network segment that must be explicitly configured access rules in and out of.
You can define a server object that effectively gives your Switch an address on the WAN side of your gateway, but it's still ultimately NAT.
The DMZ port on the 600 should not be confused with what the "DMZ" mode does on a typical consumer router, which is basically "forward all ports".
In this case, it's the enterprise definition of a DMZ: a different network segment that must be explicitly configured access rules in and out of.
You can define a server object that effectively gives your Switch an address on the WAN side of your gateway, but it's still ultimately NAT.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy wrote:
but it's still ultimately NAT.
This is why I got confused. I'm used to working with _real_ DMZs on enterprise equipment, where the devices in the DMZ are literally in front of the firewall, no NAT, no anything. The fact that the 600 still does NAT for its DMZ means it's not a real DMZ for the way I wanted to use it. Thanks for the clarification though, and thanks for the documentation link. Is there any documentation on expert mode? The link you gave says how to login, but once I'm in bash it would be nice to know where files are, how interfaces are configured the way they are, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The saga continues. I got a new modem and that didn't solve the problem. I even turned off the firewall on the 600 and that didn't solve the problem. I'm running out of ideas to get this stupid Switch to play online.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can advise you to not expect good gaming experience on the SMB appliances.
Especially NAT as Phoneboy stated above as well as the limited performance of the 600 appliance you are using.
In the SMB models, so far as I know it doesn't include a complete security bypass feature to not let inspect "anything".. might as well better not route through them.
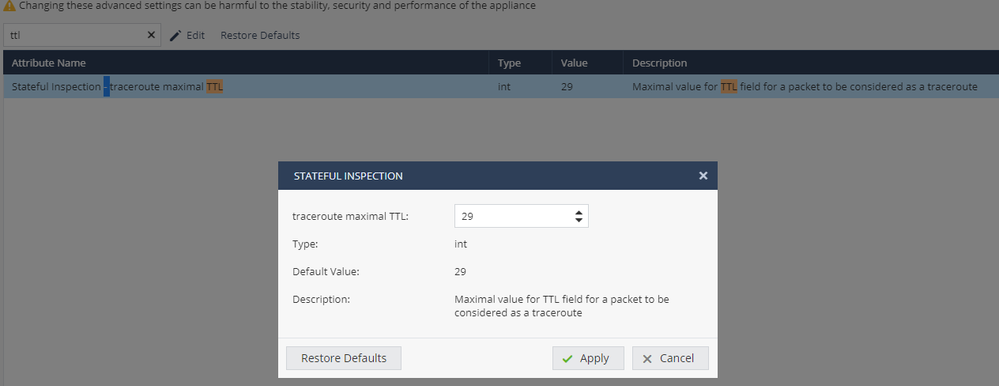
BTW, in the successor 700 Models starting R77.20.85 firmware (which is not available for 600), there is an new advanced option to avoid packet drop of applications that have a low TTL value by modifying the maximal TTL limit.
As what I've heard from our local sales rep, this option allows some online sessions working...(I believe this one was for to make "Splatoon" work).... but the option is not assured for all online activities.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hm... that's an interesting feature.
Didn't realize they had added it.
Didn't realize they had added it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally got the NAT type on the Switch to show as 'B' instead of 'C' (only A or B allow online play). I took everyone's comments from both posts I've been posting in and did the best I could on the SMB, which was making a Server for the switch and setting Static NAT to my public IP address. That made the NAT rule automatically that I couldn't make manually due to the lack of "This Gateway" in the Translated Source section. Although I now see that all it did was make a manual network object for the IP address I typed in as my public IP. So every time my ISP DHCP lease renews I'll have to modify this rule on the SMB, at least I found a way to make it work.
And because I use VoIP on my network, using Nintendo's instructions of forwarding all UDP ports to the switch doesn't work for me, so I only configured the Server in the SMB to forward UDP 65535 (since I couldn't forward zero ports). This should allow my VoIP phone to still work while the Switch works as well.
Thanks, everyone, for the input. As a side note, is there any documentation for expert mode? It seems you guys all know a lot about it and can just rattle off commands... there has to be a manual somewhere...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh you mad lad.
The "expert mode" is the wonderful CLI side of things.
It's been a many moons since I've logged into a Safe@office appliance at all let alone the CLI.
Here is the CLI guide
http://downloads.checkpoint.com/dc/download.htm?ID=61963
And here is the link the resource page:
So if you have a wee bit of Linux skills you can navigate around it pretty well.
For looking at traffic:
To see for a specific host and port:
# fw monitor -e 'accept host(x.x.x.x) and port(N);'
Kill with a ctrl-c
To see between either two host and another:
# fw monitor -e 'accept host(x.x.x.x) or host(y.y.y.y) and host(z.z.z.z);'
I can't remember if drop debugs work but if it does this can help:
fw ctl zdebug + drop
kill with a ctrl-c
You can add a grep for a specific item:
fw ctl zdebug + drop | grep "thingIwantTofind"
Kill with a ctrl-C
Standard logs are in $FWDIR/log/ and iirc you can use the "less" command to look at them as well as "cat" and "more
Good luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, I might have to try that trick at home.
Expert mode is basically a raw Linux shell.
There's a few Check Point specific things and a few things specific to the SMB appliances.
Lloyd pointed you to docs.
Expert mode is basically a raw Linux shell.
There's a few Check Point specific things and a few things specific to the SMB appliances.
Lloyd pointed you to docs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This worked for me and it actually gave me a type A.
When creating choosing the NAT option however, it lets you automatically choose hide behind gateway or static NAT.
Since I don't have a static IP I tried using the hide behind gateway option but that only gave me C.
When I choose static and put my WAN IP manually, it gave it A but this will change every 72 hours or so... still good enough for now.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter