- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: Mobile Access Blade on a Centrally managed SMB...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Mobile Access Blade on a Centrally managed SMB 1490
Hi,
Maybe somebody had already this issue, after the Upgrade from the Mgmt Server is not possible to enable the Mobile Access Blade on a SMB 1490.
Locally managed it is posible but the Idea of Central Managed is not.
Any suggestion? maybe is a Bug or maybe the incorrect way how to activate it.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You do not give details of what you try to do here - on SMB, no MAB Portal is available, so you only have SNX /SSL VPN RA clients and SSL VPN Bookmarks (links or RDP). You are unable to activate MAB in Dashboard, all you can do is activate SNX RA VPN clients in VPN Clients > Other. This is also true for R80.20.01 15x0 devices !
Check Point R77.20.xx for 600 / 700 / 1100 / 1200R / 1400 / 910 Appliance Features and Known Limitations &
Check Point R80.20 for 1500 Appliances Features and Known Limitations :
| Mobile Access Blade | Partial | Partial | All |
|
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You do not give details of what you try to do here - on SMB, no MAB Portal is available, so you only have SNX /SSL VPN RA clients and SSL VPN Bookmarks (links or RDP). You are unable to activate MAB in Dashboard, all you can do is activate SNX RA VPN clients in VPN Clients > Other. This is also true for R80.20.01 15x0 devices !
Check Point R77.20.xx for 600 / 700 / 1100 / 1200R / 1400 / 910 Appliance Features and Known Limitations &
Check Point R80.20 for 1500 Appliances Features and Known Limitations :
| Mobile Access Blade | Partial | Partial | All |
|
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @G_W_Albrecht,
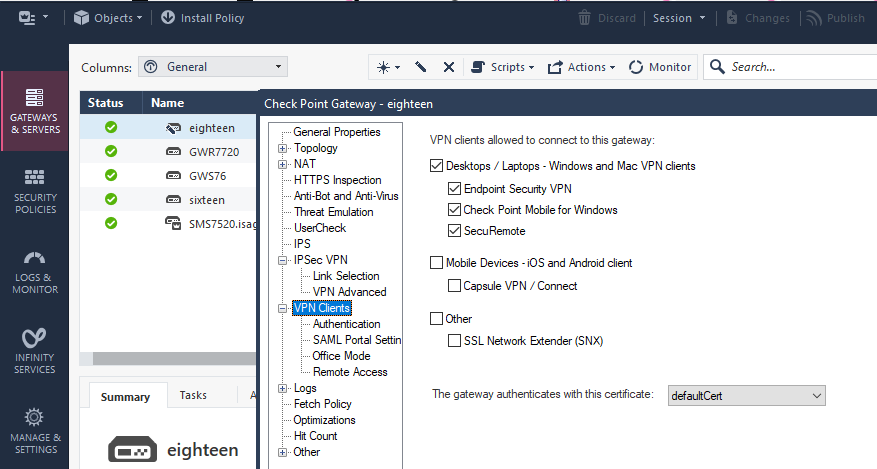
So that explains why this option on the Gateway Object in the SmatConsole is greyed out, so if we have license for MAB, that means SNX or Endpoint?
So that explains why this option on the Gateway Object in the SmatConsole is greyed out, so if we have license for MAB, that means SNX or Endpoint?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A MAB license is a blade license bound to a GAiA gateway - and Embedded GAiA 1490 appliances do neither have the MAB blade nor any MAB license at all ! So that means SNX or Endpoint, yes...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you ver much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
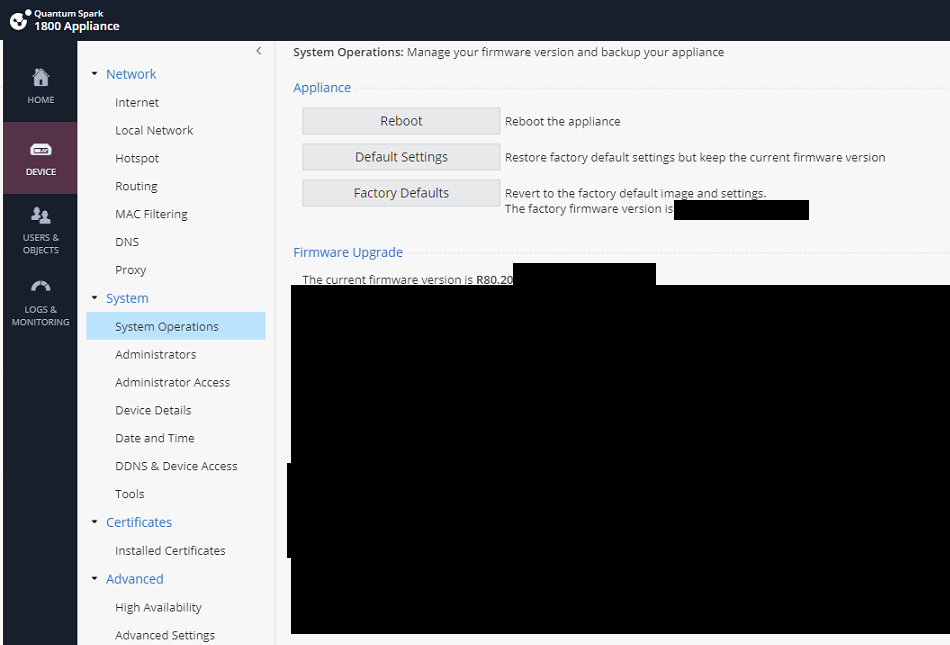
Hi,
I am trying to do the same on an 1800 quantum appliance. On the marketing material it says it has mobile access.
also, in my GW object it shows as available. however, I just can't click on it to enable as it's greyed out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same with 1800 and 1600 appliances as with 1490, all embedded GAiA appliances have no MOB blade. Only SNX and remote vpn capabilities available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you.
Can you point me in the direction of "remote vpn capabilities" please?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, how do I enable that option? I don't have it.
It's centrally managed (by Smart-1 R80.40) running R80.20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
EDIT* I should enable IPSec VPN not Mobile Access. Sorry, I have enabled and I can see the options now. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
*edit* This was posted before the above posts in conversation.
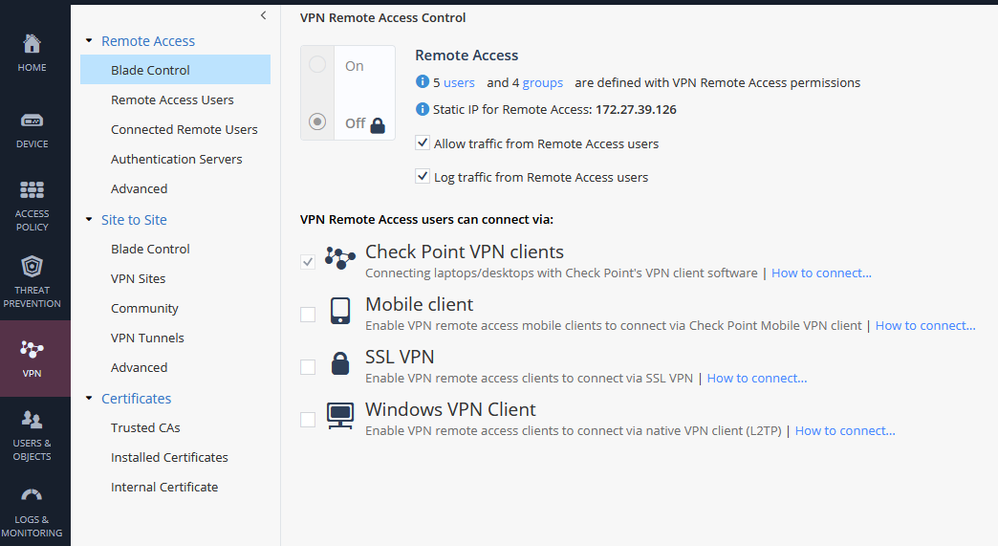
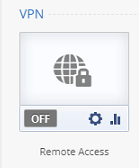
I have realised I used the wrong terminology. I am looking to enable Remote Access as below photo. Where do I go to enable this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since your SMB appliance is centrally managed, this is configured on your management.
If you've pushed a policy to your SMB gateway that includes Remote Access VPN configuration (for example a Remote Access Encryption Domain), I would expect that to be enabled.
If it's not, then it might just be a cosmetic bug and it should be taken with the TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,
Thanks, but I have it enabled now.
The "VPN OFF" post was posted before the other comment.
Thanks for the advice anyway 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello all,
unfortunately, I did not follow the logic of the solution, can you tell me - what am I missing to centrally enable "Remote Access" and IPSec for S2S on Spark 1900?
Tnank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your 1900 is centrally managed, you've already done it.
IPsec VPN also enables Remote Access via IPsec and SNX.
Mobile Access Blade (only needed for the Web Portal) is not supported on SMB appliances, thus why it appears greyed out in SmartConsole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get it now. That's probably why TAC doesn't respond to me for a long time - apparently they haven't figured out why this is happening yet... But then why are my VPN Blades gray and not activated like the same Firewall? I'll try to test RAS tomorrow, maybe it's a display bug...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you pushed a policy to the gateway that includes a VPN/Remote Access configuration?
By that I mean something outside of simply enabling IPsec VPN on the relevant gateway object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, i did, but looks like I forgot to add Security Gateway into RemoteAccess community. How Remote Acces Blade is aktive, but Site to Site VPN is still inactive:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
solution: the security gateway should be added to each Default VPN-Community:
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewWed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter