- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: Found bot activity
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
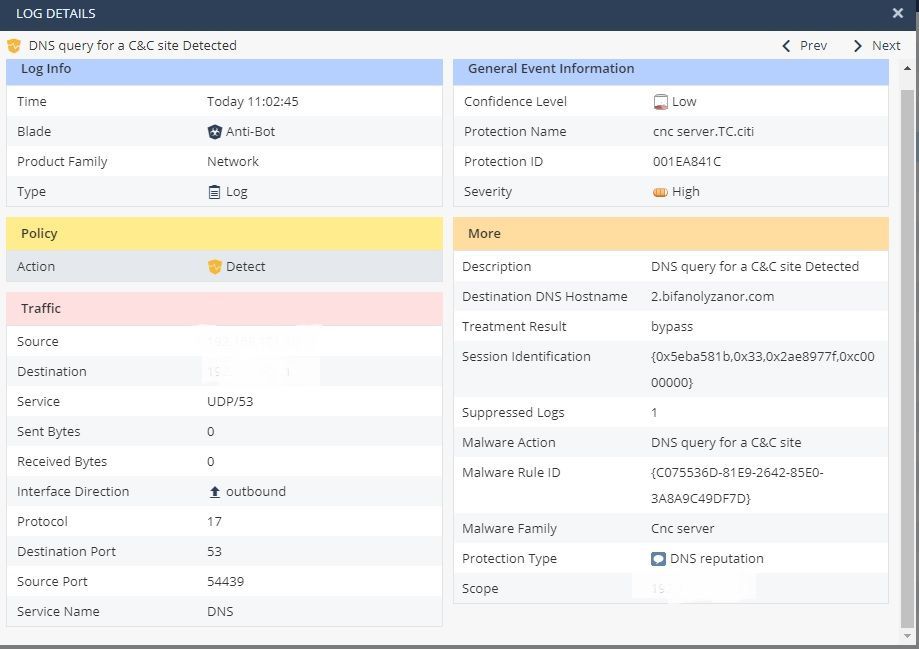
Found bot activity
My CheckPoint Firewall 730 Appliance keeps warning me about a so called infected device, always with the message "Infected device detected: .... is infected with a malware of high severity. Findings: found bot activity". This happens multiple times per day and I can't identify the problem. I have scanned the device multiple times and found nothing.
This actually happens on several devices.
Is this a false positive?
If not, how can I identify the source of the problem?
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You'll notice it's confidence of Low.
My guess is you may have visited a site that may have included something from that site.
My guess is you may have visited a site that may have included something from that site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I could see that being the case for some of the workstations, but the computer with the most frequent events is a domain server, and there is no internet surfing on it.
From my understanding (I could be wrong), this particular "malware" is related to Command & Control activities, and I frequently use Remote Desktop Connection for the server, and TeamViewer and/or AnyDesk on the workstations on the Active Directory computers.
Could this be a false positive related to that?
From my understanding (I could be wrong), this particular "malware" is related to Command & Control activities, and I frequently use Remote Desktop Connection for the server, and TeamViewer and/or AnyDesk on the workstations on the Active Directory computers.
Could this be a false positive related to that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately it is common for an internal DNS server to get tagged by Anti-bot like this, since an internal workstation with a problem sends a suspicious request to your internal DNS server for DNS service (and this traffic does not normally pass through the firewall), then the DNS server looks up the suspicious site on behalf of the internal workstation and Anti-bot sees that traffic and flags it. One way to deal with this is to enable logging of all DNS requests on the DNS server itself, to help find which internal host is initiating the suspicious lookups.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As always, you have value experience that you share it, just let me add a comment: as said Antimatt3r, most frequent events has been on DNS server, but it is not unique host, there are other workstations that trigger alerts on FW, maybe such host has other DNS, maybe it's other protection or other blade that logged those alerts, I don't know. So it's worth analyze such workstations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Forgot to mention that you can enable the "DNS trap" feature to help identify infected hosts that are having their DNS lookups handled by an internal DNS server.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the suggestions.
I enabled logging on the DNS server, and identified devices that initiate said problem. However as far as I can tell, they are not actually infected, I've scanned them multiple times.
So it might just be regular internet browsing, and the "infected" warning is just about various ads, and spam sites that launch when you visit certain sites? In other words it's just a false positive, or a warning that appears, even though the threat itself is already blocked?
About "DNS trap" feature, I'm not actually sure how to enable it from the web interface. I actually think it's already enabled, because I think I saw it listed on "protection name" on certain events, although I'm not entirely sure.
Where exactly is this setting?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm looks like DNS Trap may not be supported on embedded Gaia when it is locally managed, but I can't find any documentation confirming that one way or the other. @PhoneBoy?
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is supported and enabled by default, but it is only triggered for Medium or High confidence level, according to default profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had the same problem at a client. DHCP logs on the Windows DCs helped a bit, but did not point to the culprit.
The (Home, System) notifications section showed the events, and the Watchtower notified me, so I connected to the device and in (Logs and Monitoring) Security Logs, I entered Service:DNS. I scrolled to the approximate time and found a username associated with the event.
Once the user's Dell BIOS and Intel Management firmware were updated, the errors stopped.
In this client's case the logs seem to only go back about 8-10 hours, so I did not have the ability to go back further to aid in the search.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure why it would be linked to BIOS firmware or Intel Management Engine, but anyway since I have a 50+ workstations, this problem is starting to piss me off...
Using DNS logging I have identified the so called culprits (which keep changing, a few devices today, other ones tomorrow, some of them keep repeating etc.) and thoroughly scanned the clients on multiple occasions with no results.
It even detects IPs that belong to mobile phones and even network printers.
Like I previously said, the firewall either flags normal internet browsing, when detecting certain ads and such (some of them probably legitimately malicious, even though blocked), or it detects the activity of remote desktop software such as TeamViewer and AnyDesk, which are frequent on my network and are initiated by me. I also use RDP to connect to the Server itself.
Could be the latter since the description of the "malware" is specifically about C&C, I really don't know what to make of it...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I spoke too quickly yesterday, another instance occurred, but I cannot determine the source device.
I have not been able to reproduce this issue on demand, have you been able to reproduce on demand?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any updates on this problem? I am still bombarded with "found bot activity" events even more so than before...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Best bet is to get the TAC involved so we can understand what's going on in more detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found a PC on the network that had no AV installed other than Windows Defender. The client uses Symantec, I installed the Symantec Endpoint Protection client, no issues for last 5 days.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my case I have Kaspersky Endpoint Security on all the stations, but it doesn't seem to make a difference, those pesky events are just as frequent as ever.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter