- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: 3CX Phone System behind 1450 Appliance
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
3CX Phone System behind 1450 Appliance
Hello
Has anybody ever made 3CXPhone System work behind 1450 Appliance.
I tried probably billion of options found here or over the internet but 3CX firewall checker fails every time.
ports used by 3CX
SIP: TCP 5060-5061, UDP 5060
Tunnel: TCP 5090-5091, UDP 5090
RPT/WebRTC: UDP 9000-10999
WebUI: TCP 5000-5001
Server VoIP3CX services are added and set to manual access policy.
Outbound Policy: Traffic from Voip3CX (server) o the internet of any application is accepted
Inbound Policy: Traffic from any course to This Gateway on Voip3CX (services) is accepted
Manual NAT: Translate traffic from any source to this gateway on Voip3CX (services) as if the traffic is from original source to VoIP3CX (server) on original service
Everything I could get configured is 5000-5001 (to reach the web interface from outside)
Other things do not work.
Phone System firewall checker says (briefly) :
- bla bla
- detecting SIP ALG... not detecteda
- testing port 5060... Mapping does not match 5060. Mapping is 20112.
- testing port 5090... Mapping does not match 5090. Mapping is 20116.
- testing ports [9000..9398]... failed
- testing port 9000... Mapping does not match 9000. Mapping is 20119.
- testing port 9002... Mapping does not match 9002. Mapping is 20120.
- testing port 9004... Mapping does not match 9004. Mapping is 20121.
- testing port 9006... Mapping does not match 9006. Mapping is 20122.
and so on down to port 10999
I'm advanced with 3CX but pretty new to checkpoint. So any suggestion would be appreciated
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With manual static NAT, that should not happen. Are you sure you use SIP and not just ANY service in the rulebase?
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what is in the logs when mapping fails?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which log? check point or 3CX
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would assume: both. 8) Did you look at VoIP Issue and SMB Appliance (600/1000/1200/1400) already ? BAsic is sk113573: How to configure VoIP on Locally Managed 600 / 700 / 910 / 1100 / 1200R / 1400 appliances, this is the most important source for a working configuration of VoIP on SMB Appliances.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you send us both logs? Also, maybe on CP firewall while testing, do command fw ctl zdebug + drop | grep x.x.x.x (just make sure you test correct IP). It would be helpful to see if anything is getting dropped on kernel level.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I already checked guides and suggestions. Opened ticket and talked to supports. They also dont know.
There is nothing blocked or dropped. Logs show that at least 5060 is accepted by CP.
The problem is that original ports ie 5060-5061,5090-5091,9000-10999 are replaced by random ports.
I there any way to FORCE cp use original ports, without enabling deep inspection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With manual static NAT, that should not happen. Are you sure you use SIP and not just ANY service in the rulebase?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dude!!!
It was NOT set to ANY, but your words pushed me in right direction.
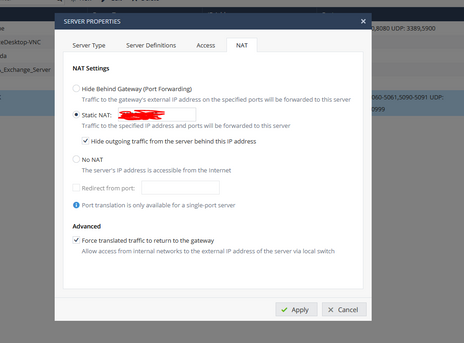
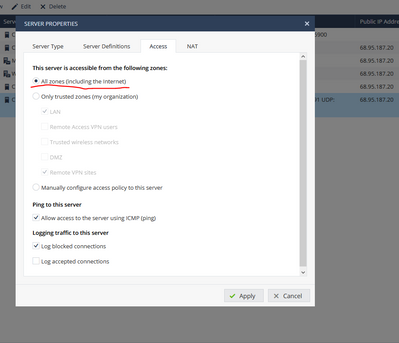
Here's config that did a magic. WAN IP in static NAT. Hide outgoing traffic and Force translate. Access from all and properly configured Policy.
All tests passed green.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am glad it works for you now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a 1550 instead of a 1450 and I am not able to find the dialogue box he showed below. Where do I prevent the firewall from changing the ports on the way back?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From your post, it looks like you have defined the Manual NAT for the Inbound portion only.
In this case, for the outbound traffic, 3CX will likely use dynamic port assignments and thus showing you the mismatched mapping.
Check if you can define Manual outbound NAT for original 3CX services.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for reply
added manual rule as
translate traffic from VoIP3CX (server) to External IP on Voip3CX (services) as if the traffic is from original source to VoIP3CX (server) on original service
nothing changed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TAC should be able to resolve that in short RAS very quickly!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
eemmm what?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
He means, technical assistance should be able to help you with a short remote session. In other words, please open a support case for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ah ) Already did. Spent over 4 hours in zoom with technician. No result. The ticket is still open.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have all 3CX services used in a single NAT rule as a composite group, please try following:
Create individual NAT rules each containing a single defined service and test again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't know if this could be related, but I had trouble getting a VoIP phone provided by a third party working on our network, connecting out through our firewall.
They asked for TCP/5061, which I added the service "sip_tls_authentication".
It never worked.
I found there was also a service "sip_tls_not_inspected", once I added that it worked, both are port 5061.
Not sure what the differences are other than one has a protocol associated with it the other didn't.
Jason
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is your key word "NOT INSPECTED"...that would totally explained why it worked. Technically, any service where protocol is set to "none" would not be inspected by anything or for anything. So, thats the main difference...NOT inspected. Think hard if thats what you want to use...
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter