- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: 1800 SMB devices and site to site VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1800 SMB devices and site to site VPN
I have a customer that has 4 1800 SMB appliances which is integrated with their existing Enterprise management software. They have 4 gws with site to site VPN configured.Recently,they have been facing alot of issues with their VPN connection after they migrated to the new appliances. I had raised several cases with checkpoint support and they have not been able to pin point the issue as well. It just works sometimes and then it stops working(Usually after policy installation). Checkpoint TAC support has not been able to solve the issue after countless escalation of the cases aswell. After hours of troubleshooting it just starts to work again and then we dont make changes to the gws anymore. We have done a VPN debug aswell but it has not proved fruitful.
When the gws first started to show errors with VPN i did the following to solve it:
1.Followed sk102712 to make the change about firewalls
2. on the firewall side, changed $FWDIR/conf/masters
with management IP address
The two steps above solved my VPN issue for awhile. After a few months, although the symptoms of the VPN issue was the same, the above steps didnt help me at all. So the only immediate solution for me was to make one of the gws(downtime cannot be tolerated during office hours) in standalone mode.
The customer has been complaining that he wants the standalone gw to be integrated to the management aswell so last night when i tried to install the policy, it fails midway. Funny thing is that, policy is installed(Access policy only)VPN is up,i can ping the management server's ip address from the gw and all the internal services but in the smart console it shows "connection is lost"for that specific gw, although i can ping,etc to the management server from that gw. I cant make further changes to the gw.
Note that the policy is any any accept.
So i read an SK on r81.10.x and SMB devices are supposed to work like a enterprise gateway as it inherits the code base from r81.10 GA version from enterprise appliances. So, will upgrading my management software and the gws to R81.10 help me solve this issue? Because all the configuration on the management server was working fine with the 4000 series appliances.
Would highly appreciate it if a SMB specialist could advice me on this.
- Tags:
- smb
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many things are different with SMB, so it could well be that the same config had worked well with 4000.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
My name is Dafna, I'm a team leader in the SMB area.
R81.10 is now available for EA. You can join our EA and upgrade your GW to R81.10.
R81.10 contains many fixes which are relevant for VPN.
Please contact me via mail to continue the process.
Thanks,
Dafna dafnam@checkpoint,com
Thanks,
Dafna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You speak of R81.10.05 for centrally managed appliances ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.10.00
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dafna,
I will send you an email to join the EA program. Thank you very much.
regards,
Nima
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Without some more details i am not sure what can be wrong exactly, some captures, logs, drops would be needed. Just guessing, try to the fw ctl zdebug drop filtering by the peer public ip address, check if you have drops like these:
dropped by fw_ipsec_encrypt_on_tunnel_instance Reason: No error - tunnel is not yet established;
If you see that try excluding IPsec, Ike and NAT-T services from encryption in your vpn community object. In a past case for a 1800 centrally managed (like yours) vpn had outages from time to time, during the problem the firewall tried to encrypt the negotiation traffic, TAC could not explain why but the exclusion solved the problem. HTH.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Daniel,
Once i push the policy to the gws, all the gws lose connection to the management server and i cant make any more changes to it. I have to literally remove ike SA's from the gws and unload the policy to make it reachable. Is there a SK that i could use to exclude NAT-T and ike services from encryption?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
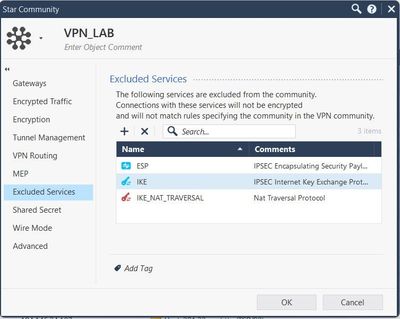
To exclude services from encryption configure the vpn community as per the image below:
I think you lose connection between the management and the gateways because of the vpn problem. I usually exclude the public IP address of all the gateways from encryption so management does not need the vpn to be up. To do this, edit the crypt.def file adding all the public ip address from gateways as dst, you can check sk108600 scenario 3 for reference, it would see something like this:
#ifndef IPV6_FLAVOR #define NON_VPN_TRAFFIC_RULES (
dst=Destination_IPv4_address_1 or \
dst=Destination_IPv4_address_2 or \
dst=Destination_IPv4_address_3 or \
dst=Destination_IPv4_address_4 \
) #else #define NON_VPN_TRAFFIC_RULES 0 #endif
The correct crypt.def file depends on the version of management an gateways, for example for a R81.10 management and 1800 gateways, the file is /opt/CPSFWR80CMP-R81.10/lib/crypt.def, you can check the admin guide of management for reference.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter