- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Re: route office mode through Ipsec tunnel (site ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
route office mode through Ipsec tunnel (site to site)
How do I route my office mode network through my site to site Ipsec tunnel to access resources in our remote offices?
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By adding these networks to your RA VPN Encryption Domain !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The target networks !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have users who are connecting to our network with SecureClient VPN 82.20.
The GW are on R77.
I am using Office Mode, the users are getting IP from the Office Mode pool and everything works fine when they are pointing to targets within our networks and all LAN resources are accessible.
Now, what I want to do is to also route them to another remote network thru site-to-site VPN that I've configured. The remote network is accessible from LAN.
How should I do that? What do I need to configure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
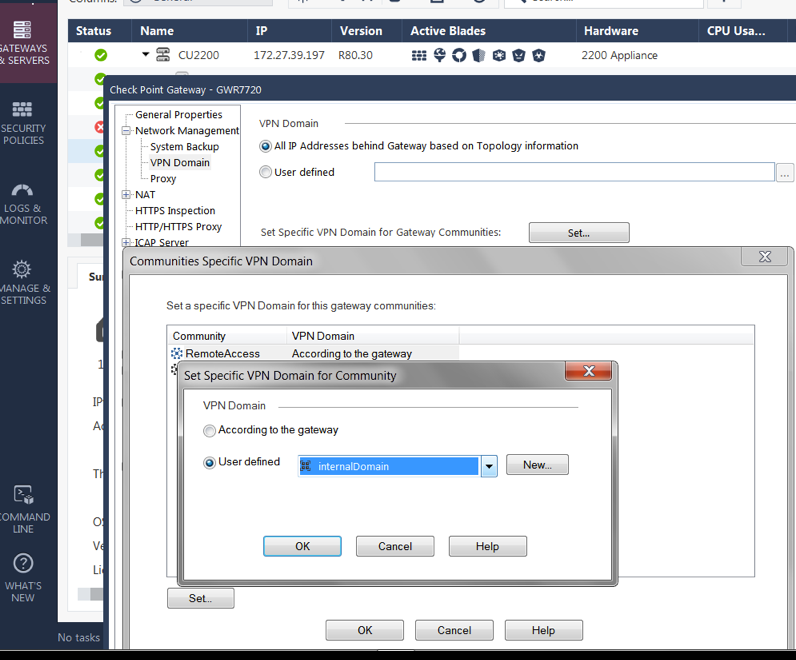
A VPN client Encryption Domain, containing all nets that should be accessible. Go into Gateway > Network Management > VPN Domain > Set specific VPN Domain for GW Communities > Select the RA Community > Set > User Defined select a Network group created for this purpose.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi, please help - i cant find the right place where i have to configure the RA vpn domain. daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Addition to the screenshot: This is R80.40, so you can select between different RA VPN communities. Up to R80.30, there was only one RA VPN community where the Domain could be set...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht,
I have done that you propose, but it does not work.
As RA VPN domain, I have created a group including internal networks and also internal networks from some remote peers, and it does not work.
We can reach, trough RA internal resources but no IPSEC site to site resources on remote peers.
From internal LAN, we can access them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht,
We have tried that you proposed (including internal networks from remote peers, with a S2S VPN with our cluster, on RA VPN domain) but we cannot reach them.
We can reach them from internal LAN only.
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Juan,
It is normal that it doesn't work. I tested in my lab by creating a group with the the local and remote subnets of the VPN tunnel; and adding the group to the VPN domain of the "RemoteAccess "community. It was OK but it wasn't enough.
In order to make it work, I had to add the Office Mode subnet (CP_default_Office ...) to the local VPN domain because I was getting the following log :
'Encryption Failure: according to the policy the packet should not have been decrypted'
So I created a group with the local subnet and the Office Mode subnet to be added to the VPN domain of the local site:

Then, I had to authorize the Office Mode subnet, on the remote gateway because the packets finished in the cleanup rule of the remote gateway.
This way from the remote client (on remote access), I was able to access to a PC on the remote site through the VPN tunnel
I hope this will help