- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: route office mode through Ipsec tunnel (site ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
route office mode through Ipsec tunnel (site to site)
How do I route my office mode network through my site to site Ipsec tunnel to access resources in our remote offices?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By adding these networks to your RA VPN Encryption Domain !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. Which network? office mode or the remote office one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The target networks !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me rephrase my question:
I have users who are connecting to our network with SecureClient VPN 82.20.
The GW are on R77.
I am using Office Mode, the users are getting IP from the Office Mode pool and everything works fine when they are pointing to targets within our networks and all LAN resources are accessible.
Now, what I want to do is to also route them to another remote network thru site-to-site VPN that I've configured. The remote network is accessible from LAN.
How should I do that? What do I need to configure?
I have users who are connecting to our network with SecureClient VPN 82.20.
The GW are on R77.
I am using Office Mode, the users are getting IP from the Office Mode pool and everything works fine when they are pointing to targets within our networks and all LAN resources are accessible.
Now, what I want to do is to also route them to another remote network thru site-to-site VPN that I've configured. The remote network is accessible from LAN.
How should I do that? What do I need to configure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
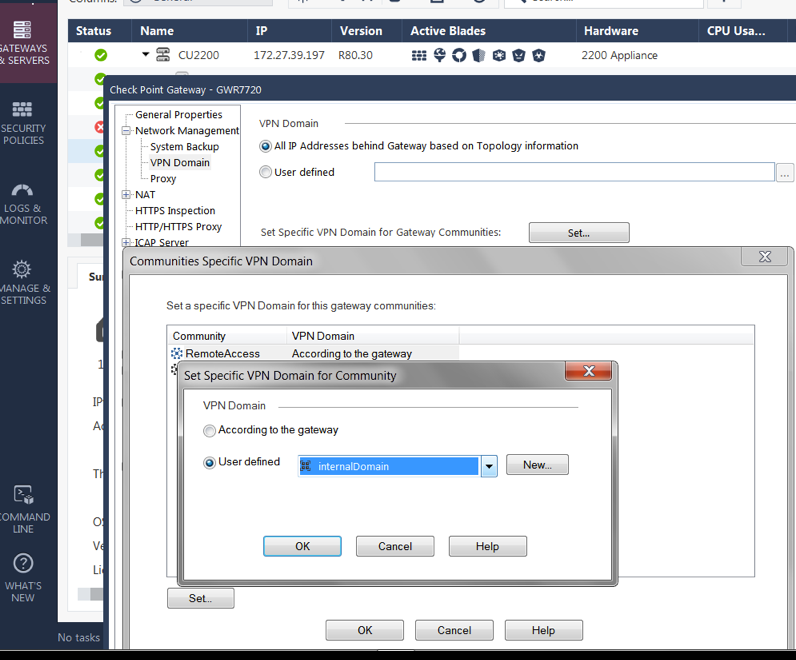
A VPN client Encryption Domain, containing all nets that should be accessible. Go into Gateway > Network Management > VPN Domain > Set specific VPN Domain for GW Communities > Select the RA Community > Set > User Defined select a Network group created for this purpose.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi, please help - i cant find the right place where i have to configure the RA vpn domain. daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Addition to the screenshot: This is R80.40, so you can select between different RA VPN communities. Up to R80.30, there was only one RA VPN community where the Domain could be set...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht,
I have done that you propose, but it does not work.
As RA VPN domain, I have created a group including internal networks and also internal networks from some remote peers, and it does not work.
We can reach, trough RA internal resources but no IPSEC site to site resources on remote peers.
From internal LAN, we can access them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht,
We have tried that you proposed (including internal networks from remote peers, with a S2S VPN with our cluster, on RA VPN domain) but we cannot reach them.
We can reach them from internal LAN only.
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Juan,
It is normal that it doesn't work. I tested in my lab by creating a group with the the local and remote subnets of the VPN tunnel; and adding the group to the VPN domain of the "RemoteAccess "community. It was OK but it wasn't enough.
In order to make it work, I had to add the Office Mode subnet (CP_default_Office ...) to the local VPN domain because I was getting the following log :
'Encryption Failure: according to the policy the packet should not have been decrypted'
So I created a group with the local subnet and the Office Mode subnet to be added to the VPN domain of the local site:

Then, I had to authorize the Office Mode subnet, on the remote gateway because the packets finished in the cleanup rule of the remote gateway.
This way from the remote client (on remote access), I was able to access to a PC on the remote site through the VPN tunnel
I hope this will help
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter