- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Problem with VPN from internal local network
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Problem with VPN from internal local network
Hi,
I am using the Quantum Spark1800 Appliance Version: R81.10 and have issues using VPN from within the local network. Any help is very much appreciated.
Everything works when I try to connect to RA VPN from outside the network, rules in firewall work as they should. When I try to connect from local internal network (LAN or WLAN), VPN client accepts login data and connects me, but every few seconds it disconnects me and reconnects again. This happens 5-10 times and then it finally disconnects me and closes the connection.
In Checkpoint VPN>Connected Remote Users: Connected Remote Users I see the user as connected, so the connection was ok but it dropped for some reason.
I don't think the problem is in the firewall because when I connect from the outside it works correctly and from the internal network the communication is established, it just drops.
The reason why I need this to work is to provide access to a separate part of the internal network via VPN (accessible for users connected via VPN and not accessible for users without the VPN).
Similar articles what I found are:
https://community.checkpoint.com/t5/Remote-Access-VPN/Using-VPN-from-within-local-network/td-p/32828...
https://community.checkpoint.com/t5/Remote-Access-VPN/VPN-client-from-inside-network/td-p/146591
https://community.checkpoint.com/t5/Remote-Access-VPN/Endpoint-disconnects-after-few-seconds-quot-re...
Am I missing something?
If you need any aditional information please let me know. Thank you
Labels
- Labels:
-
Capsule VPN (Windows)
-
Linux
-
macOS
-
SNX
-
Windows
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
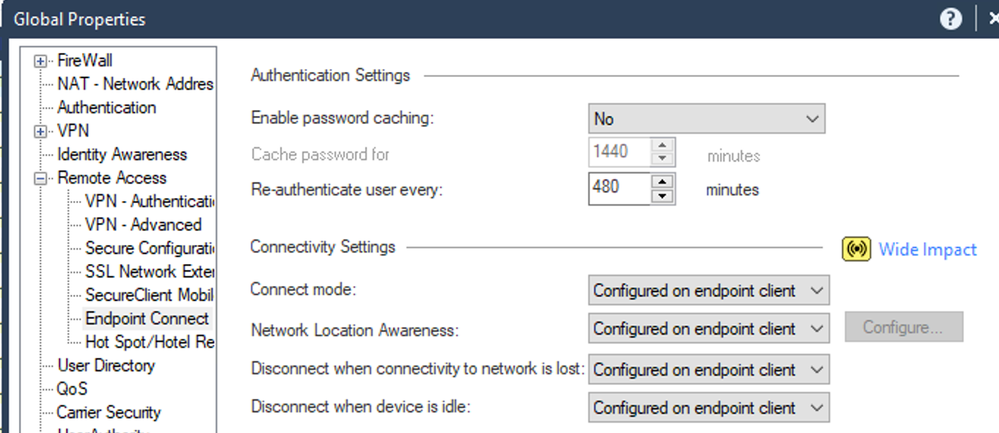
Are the hosts connecting via VPN actually in the Remote Access encryption domain?
Also, what is the Network Location Awareness setting here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi thank you for quick response.
Our internal network is set like this and I want to access VPN to admin pool and private network from LAN/WLAN
Example:
LAN
192.168.1.0/24
WLAN
192.168.2.0/24
pool for VPN (office mode)
172.16.10.0/24
admin pool which shall be accessible only via VPN
192.168.4.0/24
my private network which shall be accesible only via VPN
192.168.5.0/24
VPN>Advanced>Remote Access Advanced Settings: Configure additional advanced options for VPN remote access users
Remote Access encryption domain
I tried to set it up manually like this:
Define local network topology manually:
include
192.168.4.0/24,192.168.5.0/24
exclude
192.168.1.0/24,192.168.2.0/24
Is this the correct aproach? I tried more variants and none of them worked.
User awareness is turned off.
Reaction to the picture you sent:
Where I can find this settings screen? I only use SSH and web configuration.
In attachment I am sending logs from checkpoint VPN client.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Global Properties can only be set via the SmartConsole app or by using generic-object API calls.
However, the log from your client tells the tale:
No reply from the gw ip="publicIP" for tunnel test packet. Office Mode IP=172.16.10.2, source port=18001.
Have you done any tcpdump to verify the client is reaching out to the gateway?
Tunnel test occurs over UDP 18234.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I currently use only one Quantum spark, and I tried use smart console which I found (here). It didn't work R81.
error message:
Unable connect to server
I found "SmartConsole - Check Point Graphical User Interface for connection to and management of Security Management Servers."
We have Home>Security Management: set LOCAL
I believe that this is causing the problem as to my understanding, SmartConsole won't work for our checkpoint as we do not use managing server but one router only which we have configured trought WebUI.
Through LOGS&MONITORIN>Dieagnostics>Tools>TCPdump
pic
I was able to get this kind of output.(fake IP)
I didn't find anything with port 18234 for neither of scenarios; connecting to VPN from outside (working connection) or locally (non working connection)
@the_rock Thank you for your suggestion. Unfortunately as mentioned above, I cannot check that as I am unable to start SmartConsole.
Thak you both for your help and patient
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Never mind my suggestion then, sounds like this is locally managed smb appliance, NOT central.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that's exactly our situation, thank you for your effort @the_rock .
@PhoneBoy Could you please help me set up the Remote Access encryption domain as you recommended? Could you check that situation(here), if I understood it correctly and this setting is correct?
I have no clue where the problem could be.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
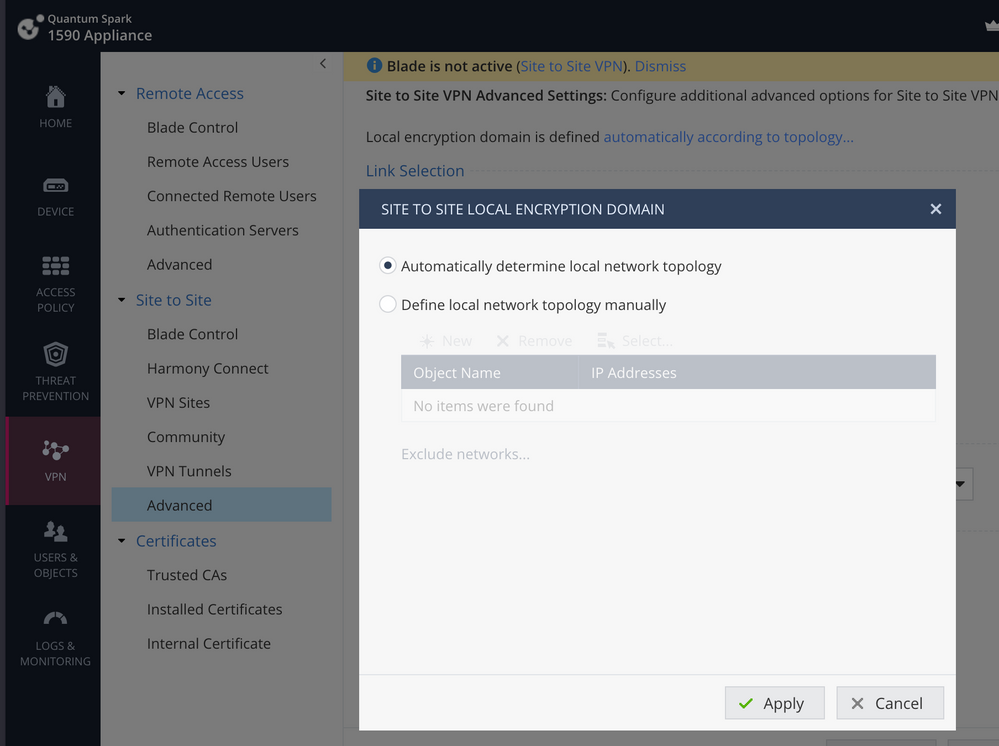
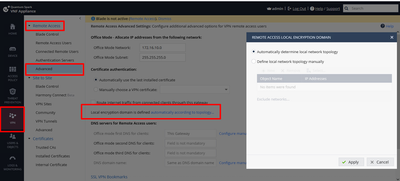
On a locally managed gateway, the default is to include all the internal IPs as part of the encryption domain.
This is probably why your client is failing to connect.
You will need to change the setting here so that the subnets you are using Remote Access from are excluded:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for response @the_rock and @PhoneBoy
To ensure that I understand correctly, there are two types of VPN: Site-to-Site (S2S) and remote access(RA).
The difference between them is that S2S connects two networks, (An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN.(here)).
On the other hand, remote access (RA) is used to access the device itself and connect to the internal network.
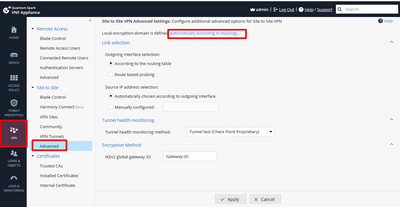
In my case, i require the second type, which is remote access (RA). In the pictures you provided, the encryption domain is set up for S2S, but since i have the S2S blade turned off, i need to configure it for RA instead?(do i understand correctly?)
In the attached picture, showing how you set up the encryption domain for RA. Could you confirm if it is correct or if there is anything what i missing?
i included the private network (that i want to access only when connected to the VPN), and i have excluded the WLAN wifi local network (the network from which i connect to the VPN).
However, even in this state, it is still not working.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
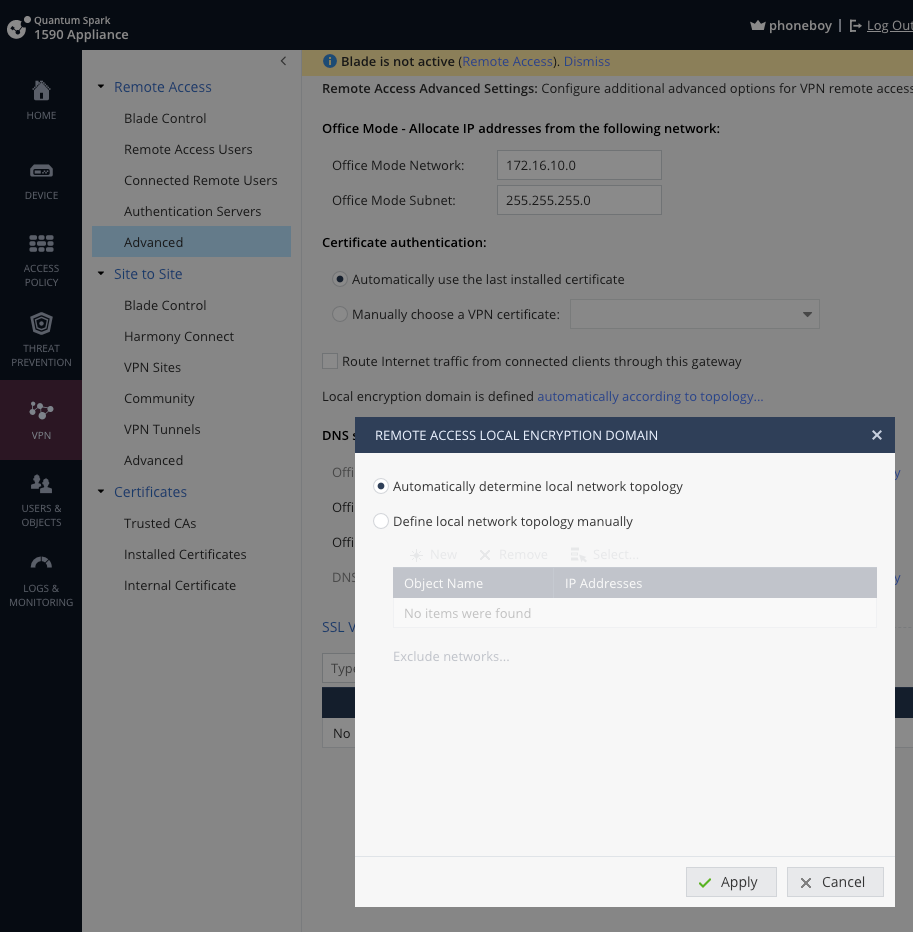
I forgot you can set the S2S and Remote Access VPN encryption domain separately.
There is a similar setting under Remote Access > Advanced that will need to be configured as previously described.
You may also need to delete and re-add the site on the client after making this change.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
S&*(, sorry mate, I keep forgetting you are using SMB locally managed appliance, my bad. Yes, that sounds right, what you attached, as far how as how you would configure it.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just spun up a demo online and here is what I found as far as remote access (Im fairly sure this is where you change it) Anyway, never mind, was working late last night, I see its same thing you attached, so yes, thats 100% right.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response @the_rock and @PhoneBoy . I apologize for later response.
I followed your instructions and attempted various combinations, but unfortunately, I'm still encountering issues. Whenever I connect from the internal network, it disconnects me after a few seconds and then attempts to reconnect. However, when connecting from an external network, the manual encryption domain setting works correctly (please refer to the attached photo).
I'm unsure about the root cause of this problem or what might be going wrong. Is it possible that this issue could be attributed to a bug in the device's/firmware version (R81.10.07)? If not, I would greatly appreciate your guidance on any alternative solutions to try or specific checks to perform in order to identify the source of the problem.
Also i found this he have same logs from VPN client.
Thank you for your assistance in troubleshooting this matter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe worth checking with TAC on this.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your best bet at this point is to consult with the TAC: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just verify what @PhoneBoy gave for global properties setting, specially network location awareness.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter