- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Mobile VPN for Windows Multiple Authentication opt...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mobile VPN for Windows Multiple Authentication options
Currently we have the Checkpoint Mobile for windows deployed, utilizing username+password with LDAP for login.
I'm wanting to implement 2FA, but with a staggered approach (start out with a small set of users).
I know that multiple authentication options are possible as per sk111583, however i'm a bit confused on the implementation.
Based on AD memberships I want one set of users to be on LDAP, and another set to be utilizing RADIUS (which will accept ldap credential, then go off to our 2FA server and do a push notification/PIN to cell, likely using DUO). I'm not sure if I can force the users into certain authentication types based off of LDAP roles, or if the options are presented on the client.
Any information on implementing this will be helpful
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What 2FA means in the context of sk111583 is that a user requires two different authentication mechanisms called directly by the Check Point gateway (e.g. Certificate + Password).
What you're describing is still effectively single factor from our perspective.
I believe you can create two different LDAP groups with the appropriate query to separate the LDAP only authentication versus the RADIUS authentication.
What you're describing is still effectively single factor from our perspective.
I believe you can create two different LDAP groups with the appropriate query to separate the LDAP only authentication versus the RADIUS authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see your point on how the gateway would still see this as single auth.
I've created the additonal LDAP group already, however i'm not able to get those users to authenticate against radius instead of AD. As they are signing in wouldn't the checkpoint need to do its first authentication to determine what memberships the account has?
I'm finally getting the resources to set up a virtual lab, so I can trial a few setups without breaking prod.
If i enable multiple login options, as per sk111583, can I enable RADIUS and LDAP for the endpoint client so that the users can choose which authentication method is used?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you enable multiple login options, it means two authentication methods can be used in serial (one after the other), not in parallel (either X or Y).
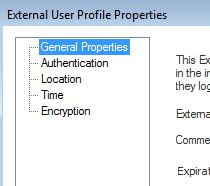
However, I think you can do what you need with an External User Profile, as described here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
These objects cannot be created in R80.x SmartConsole, but can be created via the legacy SmartDashboard as described here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
This should allow RADIUS users to specify they are using RADIUS to authenticate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for clearing the order up, I had thought it would be in parallel.
I was following the SKs you linked, however i'm not able to see the group tab, where I could add the user to a radius group.
My understanding from the articles is that once I have this configured, I can log in with the name 'example@domain', and it will go against its defined authentication. Where would I put this new object, in the source of a policy rule?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This object is basically like a group and is used in the Access Policy similar to that.
You specify the authentication as RADIUS in the Authentication tab.
You specify the authentication as RADIUS in the Authentication tab.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It doesn't look like I can use the external user profile in the unified access policy, I can't find it as a valid source.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Royi_Priov are we missing something here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David,
Rolling back a bit.
We do not have an option to configure an authentication realms for users based on their LDAP membership.
What @PhoneBoy meant regarding the serial part of the authentication is for the authentication factors within the authentication realms.
However, the realms themselves are independent, the user can choose which realm he would like to use in order to authenticate.
Does that satisfy your requirement?
Thanks,
Netanel Cohen
Software Developer, Checkpoint
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Netanel,
Sorry for the late reply, I was away for a long Canada Day weekend.
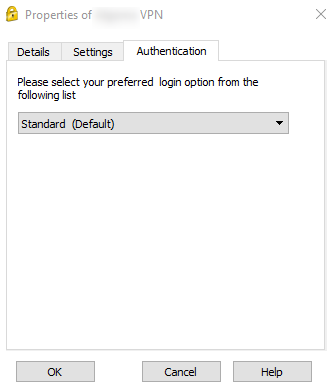
I think I understand. It looks like I can choose which authentication option here:
would I just add additional login options here? How would I define which is the default?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, and I think it's done by order.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That ended up working for me, however there was one small problem.
I found that when I added two authentication options, all my clients on their next connections received a prompt to select an authentication option. If you close the prompt, you will not connect. If you select the 'choose authentication method' link in the prompt, Default is already selected, and they can close the window and connect. I don't get why they have to open and close the authentication methods for the default to be used. It's a minor problem, but when it impacts hundreds of users you get complaints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David,
I had same problem. How we can choose which is default authentication method. Is there any option in smart console or client?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Netanel,
Could you help me about this.
For RA vpn can I use in multiple authentication 2 mandatory option LDAP user name and pass and at the same time certificate that will be generated on ldap local radius server and what are steps to implement this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
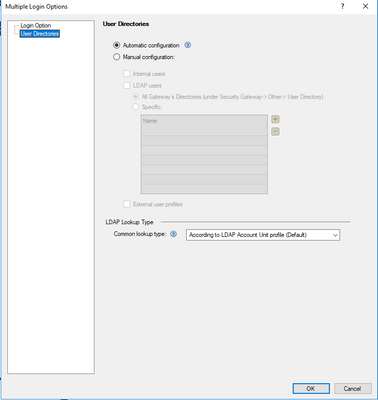
Hi,
If I understood your request right your are willing to have an authentication realm which has 1 factor as user\pass and the other as certificate and you would like that only LDAP user will be able to connect using this realm.
Yes this is possible, we have a limitation which Certificate needs always to be the 1st factor.
You need to configure the CA which issued the certificate as a trusted CA in your environment(as always when working with external CA) and limit the user directory to the relevant LDAP object:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Cohen
That is what I asked.
Also because we have R80.40 I found new option for machine authentication so I think its better solution.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter