- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- Re: L2TP over IPSec Linux VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
L2TP over IPSec Linux VPN
Hi,
we are trying to establish a L2TP over IPSec connection with Linux clients. I've already read a few entries about Linux client vpn in the forum, but they didn't really help me.
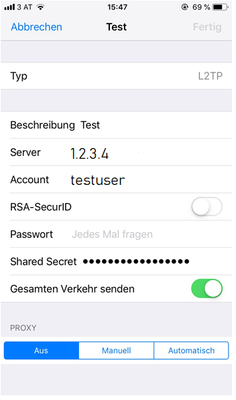
We tested it with an IOS and Android device where it worked without any problems. On the IOS device you only have to enter the Gateway IP address, the shared key and the username /password (see screen). We get an Office Mode IP address at the connection.
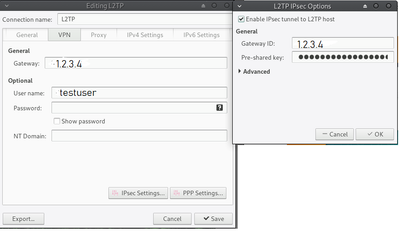
Unfortunately the connection with Linux does not work although we use the same settings (see screen).
We always get the following entries/errors in the connection log. We have tried it with Strongswan as well as with Libreswan:
Strongswan:
Mar 26 21:46:30 I-00000342U NetworkManager[996]: <info> [1553633190.0399] audit: op="connection-activate" uuid="60aa7e6b-c31f-4ce1-abe5-5b7695c44209" name="VPN_GW" pid=2365 uid=591804607 result="success" Mar 26 21:46:30 I-00000342U NetworkManager[996]: <info> [1553633190.0436] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: Started the VPN service, PID 8568 Mar 26 21:46:30 I-00000342U NetworkManager[996]: <info> [1553633190.0502] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: Saw the service appear; activating connection Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891. Mar 26 21:46:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891. Mar 26 21:46:35 I-00000342U NetworkManager[996]: <info> [1553633195.1799] settings-connection[0x556d60ecf440,60aa7e6b-c31f-4ce1-abe5-5b7695c44209]: write: successfully updated (keyfile: update /etc/NetworkManager/system-connections/VPN_GW (60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW")), connection was modified in the process Mar 26 21:46:35 I-00000342U NetworkManager[996]: <info> [1553633195.1878] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN connection: (ConnectInteractive) reply received Mar 26 21:46:35 I-00000342U nm-l2tp-service[8568]: Check port 1701 Mar 26 21:46:35 I-00000342U NetworkManager[996]: Stopping strongSwan IPsec failed: starter is not running Mar 26 21:46:37 I-00000342U NetworkManager[996]: Starting strongSwan 5.6.2 IPsec [starter]... Mar 26 21:46:37 I-00000342U NetworkManager[996]: Loading config setup Mar 26 21:46:37 I-00000342U NetworkManager[996]: Loading conn '60aa7e6b-c31f-4ce1-abe5-5b7695c44209' Mar 26 21:46:37 I-00000342U NetworkManager[996]: found netkey IPsec stack Mar 26 21:46:37 I-00000342U charon: 00[DMN] Starting IKE charon daemon (strongSwan 5.6.2, Linux 4.15.0-45-generic, x86_64) Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading ca certificates from '/etc/ipsec.d/cacerts' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading aa certificates from '/etc/ipsec.d/aacerts' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading ocsp signer certificates from '/etc/ipsec.d/ocspcerts' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading attribute certificates from '/etc/ipsec.d/acerts' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading crls from '/etc/ipsec.d/crls' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading secrets from '/etc/ipsec.secrets' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading secrets from '/etc/ipsec.d/nm-l2tp-ipsec-60aa7e6b-c31f-4ce1-abe5-5b7695c44209.secrets' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loaded IKE secret for 1.2.3.4 Mar 26 21:46:37 I-00000342U charon: 00[CFG] loading secrets from '/etc/ipsec.d/nm-l2tp-ipsec-68fc3d21-166a-4f56-a302-edd559574ff3.secrets' Mar 26 21:46:37 I-00000342U charon: 00[CFG] loaded IKE secret for %any Mar 26 21:46:37 I-00000342U charon: 00[LIB] loaded plugins: charon aesni aes rc2 sha2 sha1 md4 md5 mgf1 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl fips-prf gmp agent xcbc hmac gcm attr kernel-netlink resolve socket-default connmark stroke updown eap-mschapv2 xauth-generic counters Mar 26 21:46:37 I-00000342U charon: 00[LIB] dropped capabilities, running as uid 0, gid 0 Mar 26 21:46:37 I-00000342U charon: 00[JOB] spawning 16 worker threads Mar 26 21:46:37 I-00000342U charon: 05[CFG] received stroke: add connection '60aa7e6b-c31f-4ce1-abe5-5b7695c44209' Mar 26 21:46:37 I-00000342U charon: 05[CFG] added configuration '60aa7e6b-c31f-4ce1-abe5-5b7695c44209' Mar 26 21:46:38 I-00000342U charon: 07[CFG] rereading secrets Mar 26 21:46:38 I-00000342U charon: 07[CFG] loading secrets from '/etc/ipsec.secrets' Mar 26 21:46:38 I-00000342U charon: 07[CFG] loading secrets from '/etc/ipsec.d/nm-l2tp-ipsec-60aa7e6b-c31f-4ce1-abe5-5b7695c44209.secrets' Mar 26 21:46:38 I-00000342U charon: 07[CFG] loaded IKE secret for 1.2.3.4 Mar 26 21:46:38 I-00000342U charon: 07[CFG] loading secrets from '/etc/ipsec.d/nm-l2tp-ipsec-68fc3d21-166a-4f56-a302-edd559574ff3.secrets' Mar 26 21:46:38 I-00000342U charon: 07[CFG] loaded IKE secret for %any Mar 26 21:46:38 I-00000342U charon: 08[CFG] received stroke: initiate '60aa7e6b-c31f-4ce1-abe5-5b7695c44209' Mar 26 21:46:38 I-00000342U charon: 10[IKE] initiating Main Mode IKE_SA 60aa7e6b-c31f-4ce1-abe5-5b7695c44209[1] to 1.2.3.4 Mar 26 21:46:38 I-00000342U charon: 10[ENC] generating ID_PROT request 0 [ SA V V V V V ] Mar 26 21:46:38 I-00000342U charon: 10[NET] sending packet: from 192.168.133.24[500] to 1.2.3.4[500] (204 bytes) Mar 26 21:46:38 I-00000342U charon: 12[NET] received packet: from 1.2.3.4[500] to 192.168.133.24[500] (40 bytes) Mar 26 21:46:38 I-00000342U charon: 12[ENC] parsed INFORMATIONAL_V1 request 604563902 [ N(NO_PROP) ] Mar 26 21:46:38 I-00000342U charon: 12[IKE] received NO_PROPOSAL_CHOSEN error notify Mar 26 21:46:38 I-00000342U NetworkManager[996]: initiating Main Mode IKE_SA 60aa7e6b-c31f-4ce1-abe5-5b7695c44209[1] to 1.2.3.4 Mar 26 21:46:38 I-00000342U NetworkManager[996]: generating ID_PROT request 0 [ SA V V V V V ] Mar 26 21:46:38 I-00000342U NetworkManager[996]: sending packet: from 192.168.133.24[500] to 1.2.3.4[500] (204 bytes) Mar 26 21:46:38 I-00000342U NetworkManager[996]: received packet: from 1.2.3.4[500] to 192.168.133.24[500] (40 bytes) Mar 26 21:46:38 I-00000342U NetworkManager[996]: parsed INFORMATIONAL_V1 request 604563902 [ N(NO_PROP) ] Mar 26 21:46:38 I-00000342U NetworkManager[996]: received NO_PROPOSAL_CHOSEN error notify Mar 26 21:46:38 I-00000342U NetworkManager[996]: establishing connection '60aa7e6b-c31f-4ce1-abe5-5b7695c44209' failed Mar 26 21:46:38 I-00000342U NetworkManager[996]: Stopping strongSwan IPsec... Mar 26 21:46:38 I-00000342U charon: 00[DMN] signal of type SIGINT received. Shutting down Mar 26 21:46:38 I-00000342U nm-l2tp-service[8568]: g_dbus_method_invocation_take_error: assertion 'error != NULL' failed Mar 26 21:46:38 I-00000342U NetworkManager[996]: <info> [1553633198.6915] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN plugin: state changed: stopped (6) Mar 26 21:46:38 I-00000342U dbus-daemon[2028]: [session uid=591804607 pid=2028] Activating service name='org.freedesktop.Notifications' requested by ':1.33' (uid=591804607 pid=2365 comm="nm-applet " label="unconfined") Mar 26 21:46:38 I-00000342U NetworkManager[996]: <info> [1553633198.7007] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN service disappeared Mar 26 21:46:38 I-00000342U NetworkManager[996]: <warn> [1553633198.7050] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN connection: failed to connect: 'Message recipient disconnected from message bus without replying' Mar 26 21:46:38 I-00000342U dbus-daemon[2028]: [session uid=591804607 pid=2028] Successfully activated service 'org.freedesktop.Notifications' Mar 26 21:46:40 I-00000342U ntpd[1131]: error resolving pool windows.ad.loc: No address associated with hostname (-5)
Libreswan:
Mar 26 21:48:06 I-00000342U systemd[1]: message repeated 4 times: [ Reloading.]
Mar 26 21:48:25 I-00000342U NetworkManager[996]: <info> [1553633305.9419] audit: op="connection-activate" uuid="60aa7e6b-c31f-4ce1-abe5-5b7695c44209" name="VPN_GW" pid=2365 uid=591804607 result="success"
Mar 26 21:48:25 I-00000342U NetworkManager[996]: <info> [1553633305.9480] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: Started the VPN service, PID 9153
Mar 26 21:48:25 I-00000342U NetworkManager[996]: <info> [1553633305.9572] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: Saw the service appear; activating connection
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891.
Mar 26 21:48:26 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: gdk_pixbuf_from_pixdata() called on: at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Encoding raw at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Dimensions: 16 x 16 at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Rowstride: 64, Length: 1048 at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U org.mate.panel.applet.BriskMenuFactory[2028]: GdkPixbuf-LOG **: #011Copy pixels == false at /usr/bin/shutter line 2891.
Mar 26 21:48:30 I-00000342U NetworkManager[996]: <info> [1553633310.2738] settings-connection[0x556d60ecf440,60aa7e6b-c31f-4ce1-abe5-5b7695c44209]: write: successfully updated (keyfile: update /etc/NetworkManager/system-connections/VPN_GW (60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW")), connection was modified in the process
Mar 26 21:48:30 I-00000342U NetworkManager[996]: <info> [1553633310.2794] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN connection: (ConnectInteractive) reply received
Mar 26 21:48:30 I-00000342U nm-l2tp-service[9153]: Check port 1701
Mar 26 21:48:30 I-00000342U NetworkManager[996]: whack: Pluto is not running (no "/run/pluto/pluto.ctl")
Mar 26 21:48:30 I-00000342U NetworkManager[996]: Redirecting to: systemctl stop ipsec.service
Mar 26 21:48:30 I-00000342U NetworkManager[996]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9185]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U NetworkManager[996]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9190]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U NetworkManager[996]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9203]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U NetworkManager[996]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9208]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U NetworkManager[996]: Redirecting to: systemctl start ipsec.service
Mar 26 21:48:30 I-00000342U systemd[1]: Starting Internet Key Exchange (IKE) Protocol Daemon for IPsec...
Mar 26 21:48:30 I-00000342U addconn[9477]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9477]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U _stackmanager[9478]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9480]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U _stackmanager[9478]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:30 I-00000342U libipsecconf[9485]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:31 I-00000342U ipsec[9753]: Initializing NSS database
Mar 26 21:48:31 I-00000342U ipsec[9756]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:31 I-00000342U libipsecconf[9758]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:31 I-00000342U ipsec[9756]: nflog ipsec capture disabled
Mar 26 21:48:31 I-00000342U systemd[1]: Started Internet Key Exchange (IKE) Protocol Daemon for IPsec.
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 listening for IKE messages
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface vmnet8/vmnet8 172.16.7.1:500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface vmnet8/vmnet8 172.16.7.1:4500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface vmnet1/vmnet1 172.16.98.1:500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface vmnet1/vmnet1 172.16.98.1:4500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface wlp4s0/wlp4s0 192.168.133.24:500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface wlp4s0/wlp4s0 192.168.133.24:4500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface lo/lo 127.0.0.1:500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface lo/lo 127.0.0.1:4500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 adding interface lo/lo ::1:500
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 loading secrets from "/etc/ipsec.secrets"
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 loading secrets from "/etc/ipsec.d/nm-l2tp-ipsec-60aa7e6b-c31f-4ce1-abe5-5b7695c44209.secrets"
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 loading secrets from "/etc/ipsec.d/nm-l2tp-ipsec-68fc3d21-166a-4f56-a302-edd559574ff3.secrets"
Mar 26 21:48:31 I-00000342U NetworkManager[996]: debugging mode enabled
Mar 26 21:48:31 I-00000342U NetworkManager[996]: end of file /var/run/nm-l2tp-ipsec-60aa7e6b-c31f-4ce1-abe5-5b7695c44209.conf
Mar 26 21:48:31 I-00000342U NetworkManager[996]: Loading conn 60aa7e6b-c31f-4ce1-abe5-5b7695c44209
Mar 26 21:48:31 I-00000342U NetworkManager[996]: starter: left is KH_DEFAULTROUTE
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" labeled_ipsec=0
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" modecfgdns=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" modecfgdomains=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" modecfgbanner=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" mark=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" mark-in=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" mark-out=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: conn: "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" vti_iface=(null)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: opening file: /var/run/nm-l2tp-ipsec-60aa7e6b-c31f-4ce1-abe5-5b7695c44209.conf
Mar 26 21:48:31 I-00000342U NetworkManager[996]: loading named conns: 60aa7e6b-c31f-4ce1-abe5-5b7695c44209
Mar 26 21:48:31 I-00000342U NetworkManager[996]: seeking_src=1, seeking_gateway = 1, has_peer = 1
Mar 26 21:48:31 I-00000342U NetworkManager[996]: seeking_src=0, seeking_gateway = 1, has_dst = 1
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst via 192.168.133.1 dev wlp4s0 src table 254
Mar 26 21:48:31 I-00000342U NetworkManager[996]: set nexthop: 192.168.133.1
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 169.254.0.0 via dev wlp4s0 src table 254
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.7.0 via dev vmnet8 src 172.16.7.1 table 254
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.98.0 via dev vmnet1 src 172.16.98.1 table 254
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 192.168.133.0 via dev wlp4s0 src 192.168.133.24 table 254
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 127.0.0.0 via dev lo src 127.0.0.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 127.0.0.0 via dev lo src 127.0.0.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 127.0.0.1 via dev lo src 127.0.0.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 127.255.255.255 via dev lo src 127.0.0.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.7.0 via dev vmnet8 src 172.16.7.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.7.1 via dev vmnet8 src 172.16.7.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.7.255 via dev vmnet8 src 172.16.7.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.98.0 via dev vmnet1 src 172.16.98.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.98.1 via dev vmnet1 src 172.16.98.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 172.16.98.255 via dev vmnet1 src 172.16.98.1 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 192.168.133.0 via dev wlp4s0 src 192.168.133.24 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 192.168.133.24 via dev wlp4s0 src 192.168.133.24 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 192.168.133.255 via dev wlp4s0 src 192.168.133.24 table 255 (ignored)
Mar 26 21:48:31 I-00000342U NetworkManager[996]: seeking_src=1, seeking_gateway = 0, has_peer = 1
Mar 26 21:48:31 I-00000342U NetworkManager[996]: seeking_src=1, seeking_gateway = 0, has_dst = 1
Mar 26 21:48:31 I-00000342U NetworkManager[996]: dst 192.168.133.1 via dev wlp4s0 src 192.168.133.24 table 254
Mar 26 21:48:31 I-00000342U NetworkManager[996]: set addr: 192.168.133.24
Mar 26 21:48:31 I-00000342U NetworkManager[996]: seeking_src=0, seeking_gateway = 0, has_peer = 1
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #1: initiating Main Mode
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 104 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #1: STATE_MAIN_I1: initiate
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 106 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #1: STATE_MAIN_I2: sent MI2, expecting MR2
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 108 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #1: STATE_MAIN_I3: sent MI3, expecting MR3
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #1: Peer ID is ID_IPV4_ADDR: '1.2.3.4'
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 004 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #1: STATE_MAIN_I4: ISAKMP SA established {auth=PRESHARED_KEY cipher=aes_128 integ=sha group=MODP1536}
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 002 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: initiating Quick Mode PSK+ENCRYPT+UP+IKEV1_ALLOW+IKEV2_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW+ESN_NO {using isakmp#1 msgid:fa1d1722 proposal=defaults pfsgroup=no-pfs}
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 117 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: STATE_QUICK_I1: initiate
Mar 26 21:48:31 I-00000342U NetworkManager[996]: 010 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: STATE_QUICK_I1: retransmission; will wait 0.5 seconds for response
Mar 26 21:48:32 I-00000342U libipsecconf[9785]: warning: could not open include filename: '/etc/ipsec.d/*.conf'
Mar 26 21:48:32 I-00000342U NetworkManager[996]: 010 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: STATE_QUICK_I1: retransmission; will wait 1 seconds for response
Mar 26 21:48:33 I-00000342U NetworkManager[996]: 010 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: STATE_QUICK_I1: retransmission; will wait 2 seconds for response
Mar 26 21:48:35 I-00000342U NetworkManager[996]: 010 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: STATE_QUICK_I1: retransmission; will wait 4 seconds for response
Mar 26 21:48:39 I-00000342U NetworkManager[996]: 010 "60aa7e6b-c31f-4ce1-abe5-5b7695c44209" #2: STATE_QUICK_I1: retransmission; will wait 8 seconds for response
Mar 26 21:48:41 I-00000342U nm-l2tp-service[9153]: g_dbus_method_invocation_take_error: assertion 'error != NULL' failed
Mar 26 21:48:41 I-00000342U NetworkManager[996]: <info> [1553633321.2615] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN plugin: state changed: stopped (6)
Mar 26 21:48:41 I-00000342U NetworkManager[996]: <info> [1553633321.2717] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN service disappeared
Mar 26 21:48:41 I-00000342U dbus-daemon[2028]: [session uid=591804607 pid=2028] Activating service name='org.freedesktop.Notifications' requested by ':1.33' (uid=591804607 pid=2365 comm="nm-applet " label="unconfined")
Mar 26 21:48:41 I-00000342U NetworkManager[996]: <warn> [1553633321.2774] vpn-connection[0x556d610801e0,60aa7e6b-c31f-4ce1-abe5-5b7695c44209,"VPN_GW",0]: VPN connection: failed to connect: 'Message recipient disconnected from message bus without replying'
Mar 26 21:48:41 I-00000342U dbus-daemon[2028]: [session uid=591804607 pid=2028] Successfully activated service 'org.freedesktop.Notifications'Has anyone any idea why L2TP over IPSec works so easy with IOS and Adroid devices and not with a Linux client?
Hopefully someone of you has a solution for this.
BR
René
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Running setup:
R80.30 Standalone with Jumbo Take 195 (In R80.x, when the L2TP Client is behind a NAT device, the connection won't work, see sk145895. This was fixed with Jumbo Take 195.
Requirements Check Point:
- Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support Legacy Authentication for SC
- Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support L2TP with Pre-Shared Key
- Gateway Object - Properties - VPN Clients - Remote Access - Support L2TP
Step 1)
- For this test I used Mint Linux 19.2 with Libreswan 3.23 and xl2tpd 1.3.10
- Network Manager 1.10.6 with Plugin: network-manager-l2tp-gnome 1.7.2 (#sudo apt-get install network-manager-l2tp-gnome)
Step 2)
Open Network on the Linux Client
Step 3)
Create L2TP Connection
Step 4)
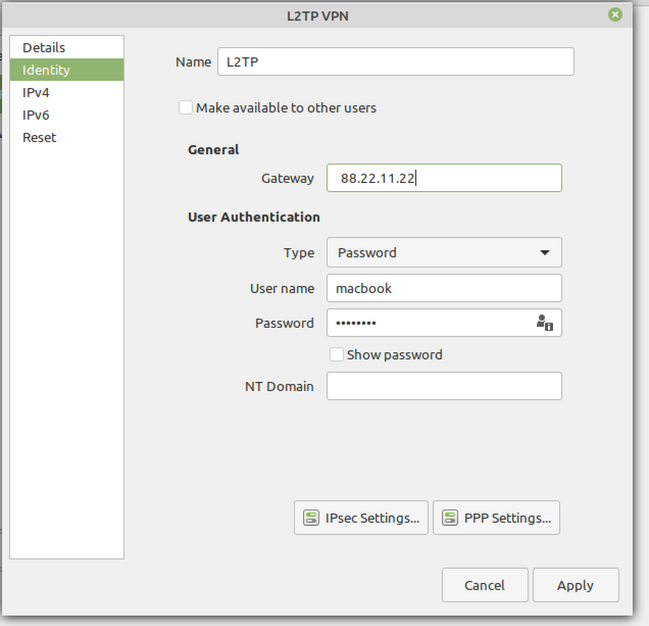
Under Gateway insert your external Firewall IP Address. Please also fill out the username who is allowed to connect to your gateway.
Step 5)
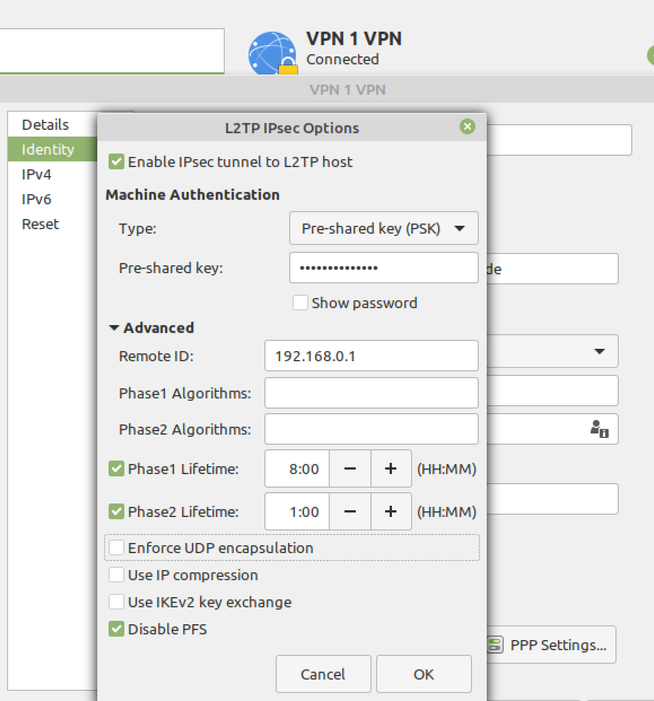
IPsec Settings - Under the Remote ID put in the IP Address of your Check Point Firewall which is the Main IP Address of the Object. In my case it is 192.168.0.1. Pre-shared-Key is the L2TP Key which was defined in the CP Dashboard.
Lifetime Phase 1 = 8h
Lifetime Phase 2 = 1h
Step 6)
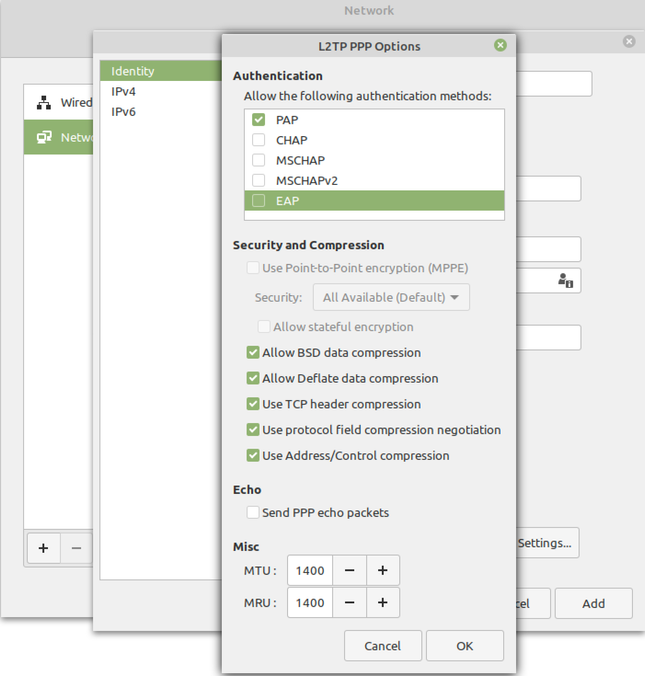
PPP Settings - Check only PAP.
Now the L2TP client should connect fine. If there are any issues, check out /var/log/pluto.log for any errors.
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Rene,
look like for Strongswan the Phase 1 proposals do not match: "NO_PROPOSAL_CHOSEN" error notify
For Libreswan the Phase 1 (Main Mode) is established: "ISAKMP SA established" but Phase 2 (Quick Mode) does not complete.
You could check the Checkpoint logs , may be a "vpn debug ..." would be helpful
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
sorry for the late reply. We have tested the connection again with libreswan and active VPN debug and found the following in the VPN logs:
This must be from Phase1:
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] chooseProposalFromList: Failed to match proposal. Transform: AES-128, SHA1, Pre-shared secret, Group 2 (1024 bit); Reason: Proposed DH group doesn't match client settings (proposed: 14).
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] CachedObject::istrue: Cache miss: isakmp_force_sr_dh: false (0)
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] chooseProposalFromList: Failed to match in strict mode. Will try matching all supported DH groups
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] transformsMatch: found group: 5
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] got life type: 1 (SEC)
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] got life duration. lifetype: (nil) (-1), ignore ((nil)) is set to: -1, putinstate: 0,
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] transformsMatch: found group: 5
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] matchTransList: Matched transform AES-128, SHA1, Pre-shared secret, Group 5 (1536 bit);The client has no dedicated settings for the encryption algorithms, just like the mobile devices. However, you can see that the GW and the client agree on AES-128, SHA1, Pre-shared secret, Group 5 (1536 bit).
This is what we see in Phase 2:
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] insert_auth_specific_groups_to_user: Already inserted
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] ike_methods_from_encaction: ESP methods=211 0, enacapsulation: TUNNEL
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] spiIsInUse: SPI: 0xff37bc5a not used by any inbound SA on any instance
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] allocateSpi: Allocated SPI: 0xff37bc5a, 0 collisions (currently 1 reserved).
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] update_saexp_in_trans: expiration 600 seconds
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] proposalListFromMethods: ESP encapsulation mode is: UDP ENCAPSULATED TRANSPORT
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] checkInternalIP: entering. external=b2738062 internal=c0a82b92
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] userHasIP: IP address c0a82b92 has not been assigned.
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] GOT LIFE DURATION P2 (lifetype: (nil), pair->type: 1)
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] GOT LIFE DURATION P2 (lifetype: (nil), pair->type: 1)
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] chooseProposalFromList: Failed to match proposal. Transform: AES-256, SHA1, UDP Encapsulation; Reason: Wrong value for: Key Length
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] QMCreate2ChooseProp: Cannot choose a proposal
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] Error has occurred, or proposal list not supported
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] fwisakmp_user_failed_with_auth: enter, reject category 3
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] create_login_log: Called
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] create_login_log: Called
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] create_login_log: expiration is invalid (0)
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] create_login_log: generate new log uid
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] vpn_need_login_log: begin
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] CFwdCommStreamLocal::Write called
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] CFwdCommStreamLocal::Write sent 328 bytes
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] vpn_need_login_log: begin
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] CFwdCommStreamLocal::Write called
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] CFwdCommStreamLocal::Write sent 72 bytes
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51][ikestate] < FWIKE_ROLE_INITIATOR > Id = 1650059
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] ike_initiator: entering with my_instance: -1
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] ike_initiator: notifyData.notifyType = 0
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] computeIV from:
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] 42 7a c0 62 82 50 bd a4 0d 14 20 db 80 97 22 21
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] d4 f1 02 bd
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] Sent Notification to Peer b2738062: no proposal chosen
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] Notification to Peer b2738062: Sent Notification: no proposal chosen
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] extended_log_info_build_reason_from_list: list is empty,
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] isakmpd_log: calling isakmpd_log with original reason=(Sent Notification: no proposal chosen)
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] GetDAGIP: ID b2738062 not in DAIP range
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] CFwdCommStreamLocal::Write called
obviously the error lies here :
hooseProposalFromList: Failed to match proposal. Transform: AES-256, SHA1, UDP Encapsulation; Reason: Wrong value for: Key Length
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] QMCreate2ChooseProp: Cannot choose a proposal
[vpnd 9342 4101552016]@gw1[2 Apr 14:23:51] Error has occurred, or proposal list not supported
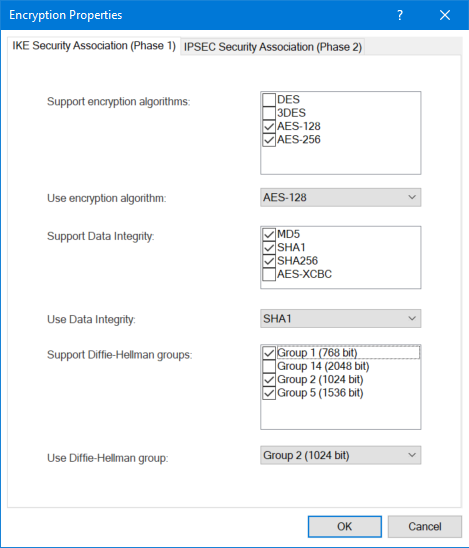
These are our supported encryption algorithms
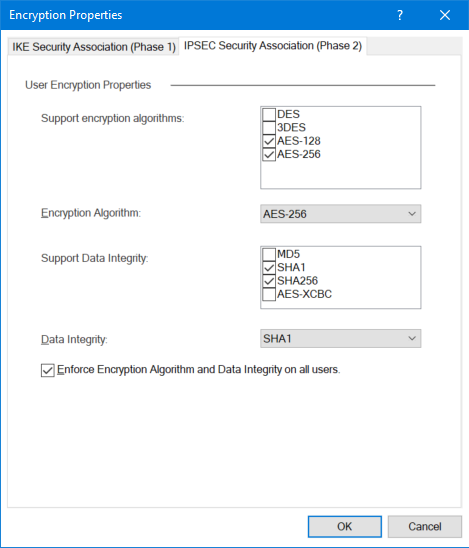
So actually the algorithms should be supported after all
I hope one of you has a solution.
BR
Rene
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tested L2TP (Mint 19.2) with Network Manager and R80.30 and it works.
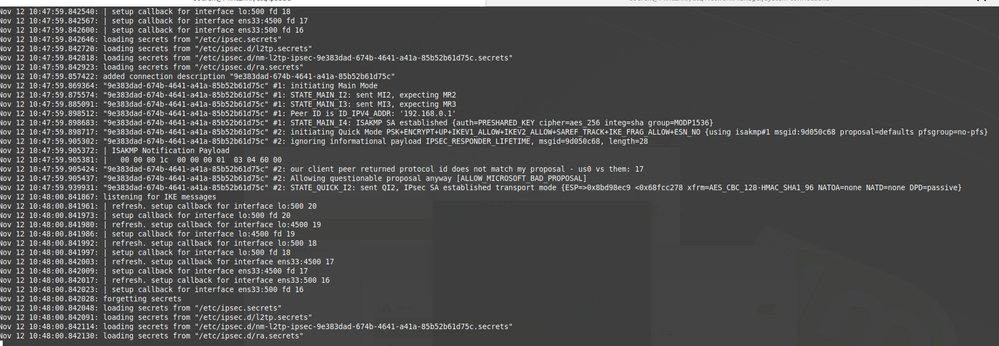 |
Make sure that you have only PAP selected in PPP options
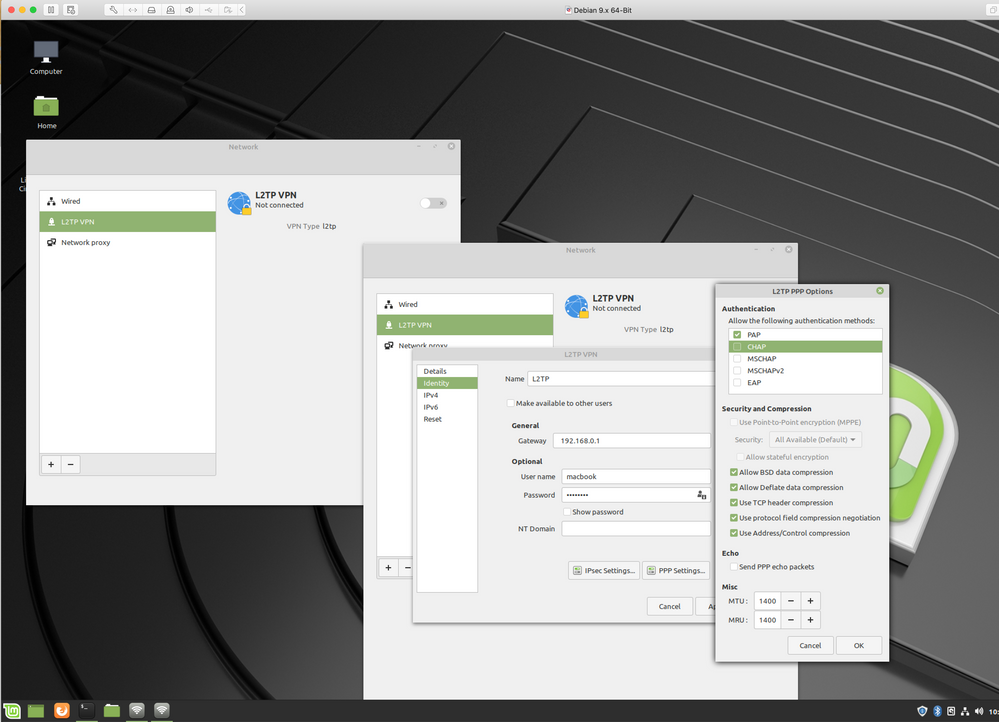 |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
thx for your reply, but you are using L2TP with PPP and not over IPSec, so this wont help us.
It's simply a huge shame that Checkpoint still ignores Linux users in 2019
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is L2TP over IPSEC.
You need PPP for the user authentication, otherwise it won't work.
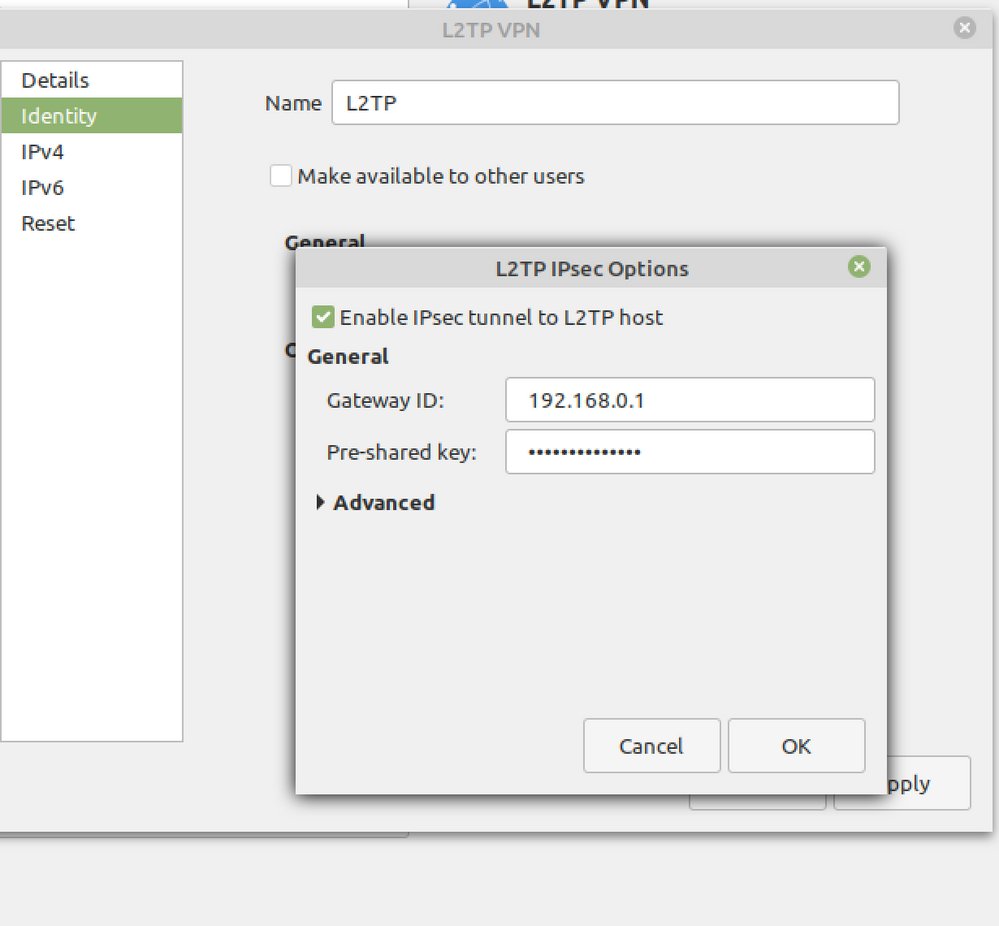 |
As you can see, the ppp0 device uses the OfficeMode IP
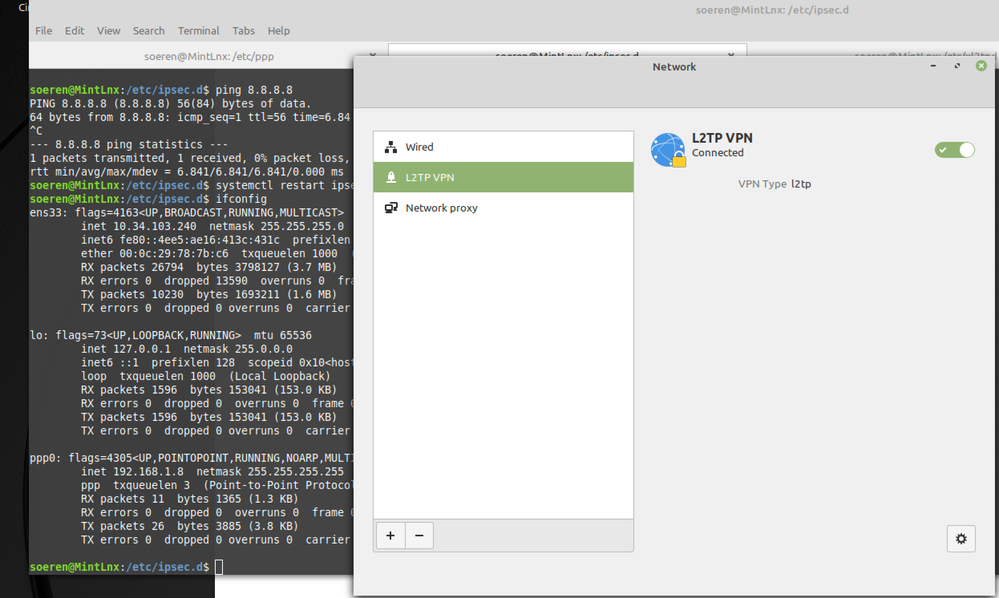 |
Currently my Linux will only connect, if I am in the same external network like my firewall. Behind a NAT device it does not connect and gives me "No Proposal Chosen" errors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Running setup:
R80.30 Standalone with Jumbo Take 195 (In R80.x, when the L2TP Client is behind a NAT device, the connection won't work, see sk145895. This was fixed with Jumbo Take 195.
Requirements Check Point:
- Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support Legacy Authentication for SC
- Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support L2TP with Pre-Shared Key
- Gateway Object - Properties - VPN Clients - Remote Access - Support L2TP
Step 1)
- For this test I used Mint Linux 19.2 with Libreswan 3.23 and xl2tpd 1.3.10
- Network Manager 1.10.6 with Plugin: network-manager-l2tp-gnome 1.7.2 (#sudo apt-get install network-manager-l2tp-gnome)
Step 2)
Open Network on the Linux Client
Step 3)
Create L2TP Connection
Step 4)
Under Gateway insert your external Firewall IP Address. Please also fill out the username who is allowed to connect to your gateway.
Step 5)
IPsec Settings - Under the Remote ID put in the IP Address of your Check Point Firewall which is the Main IP Address of the Object. In my case it is 192.168.0.1. Pre-shared-Key is the L2TP Key which was defined in the CP Dashboard.
Lifetime Phase 1 = 8h
Lifetime Phase 2 = 1h
Step 6)
PPP Settings - Check only PAP.
Now the L2TP client should connect fine. If there are any issues, check out /var/log/pluto.log for any errors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this guys, I'm wondering if this will work without the pre-shared key?
As I have not entered the pre-shared key and I see this error, I am assuming this is the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
L2TP config requires pre-shared key to work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Val. Ok, sadly my companies policy is to not share these details with us.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter