- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Is there a setting to turn off the VPN credent...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a setting to turn off the VPN credential caching
We are moving from #Cisco to Check Point and are testing out the remote access vpn. We have a setup with using an LDAP connection with Duo for 2FA. We are experiencing the gateway only authenticating fully through LDAP/Duo only on the initial connection. If we then disconnect and connect again, the mobile vpn seems like its using cached credentials and only using the user/pass but still not hitting the LDAP server.
Is there a setting we can set in the management (r77.30) or GuiDbEdit that will require the gateway to re-authenticate and not use cached credentials on the endpoint?
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the quick response and sorry for the slow reply...
I should not have said endpoint since that is a CP product. I meant in general the CP VPN client. Although we are going to be deploying Endpoint Security in the future, we are currently dealing with connecting to an embedded GAIA device via the CP mobile VPN client for Windows. Are there settings on the gateway or management, through policy or db edits, where we can disable the credential caching?
When testing, I login using my credentials which includes using Duo for 2FA. The Duo 2FA should not be an issue since it's a proxy between the CP gateway and the LDAP server. The CP gateway sends the LDAP request to the Duo proxy which then forwards that request to the LDAP server. Once the Duo proxy receives the successful LDAP response it will hold that response and reach out to the Duo service for the 2FA push. Once it receives the successful 2FA authentication for the user then it will release the successful LDAP auth response to the CP gateway.
I wanted to give a quick overview of the LDAP/2FA before because we only get the Duo 2FA on the initial connection. After that initial connection, the CP VPN authenticates without ever hitting the Duo proxy. Since we do not get that Duo 2FA prompt, I know it's using cached credentials.
2FA is a requirement, so we have to find a way to stop this CP VPN from caching the credentials with something besides an Endpoint Security setting.
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
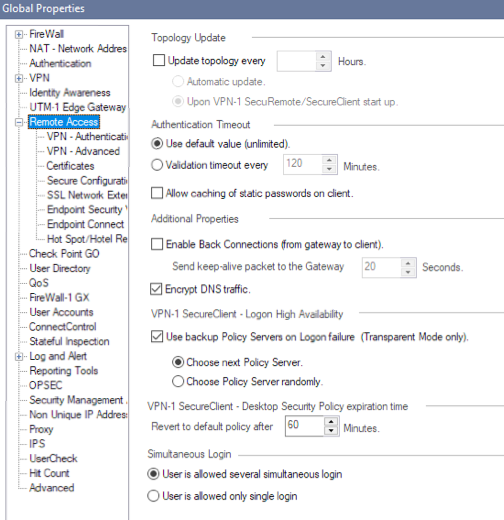
There are a couple of Global Properties that may be relevant here.
First it looks like there is an "Allow caching of static passwords on client" property here:
There also appears to be an "Enable password caching" option on this screen:
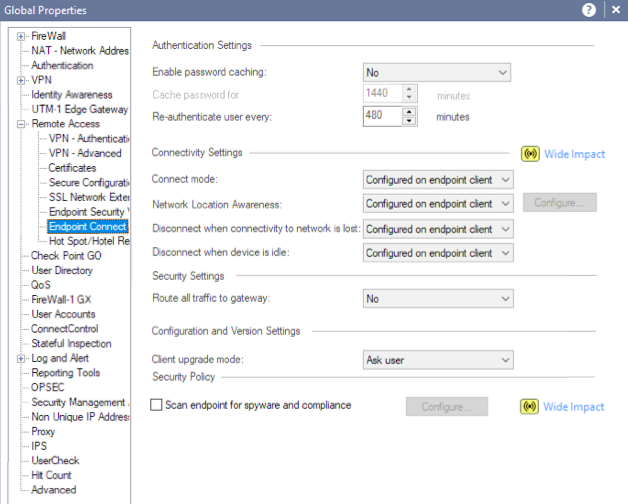
Obviously if these settings are different than what's shown, a policy push will be required for all gateways.
If you have these settings as shown and it's still not working, I recommend opening a ticket with the TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heath,
Can you confirm if this fixed the problem for you? I'm having very similar issues with trying to implement Duo via an LDAP proxy. Initial login generates 2FA challenge, subsequent logins don't. On top of it all, after some time goes by (hard to pin down exactly how long, could be minutes, could be hours), even primary authentication stops working. If I look in the logs of the Duo proxy, there aren't even attempts being logged, which makes it look like Check Point just isn't even sending the requests in. Some users (again, seemingly random) continue to work while others fail. The ones that work all show up in the Duo logs. The ones that don't, there isn't even an attempt logged in Duo. The Duo is the only server in my LDAP account unit within Check Point, so the requests shouldn't be getting forwarded anywhere else.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After hashing things out it turns out that Duo was having issues with the LDAP pass thru. We swapped to using NPS/RADIUS and Duo works. Support guy from Duo said they have multiple people have issues with LDAP and the Duo proxy. Not sure if that is fixed but we don't use LDAP with the Duo proxy anymore and it's working great.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the fast reply! I have an open case now with CP support to try and figure out getting LDAP working, but I was starting to wonder if I should just fall back to RADIUS. Sounds like that's definitely a viable option.
One of my concerns with changing to RADIUS was losing the ability to use AD group membership for defining access in the Mobile Access policy. Are you still able to do that with RADIUS authentication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not via passing back the attribute class via the NPS/RADIUS...even though it says you can do that in the documentation we've tried and it does not work. Our basic setup is that we use the RADIUS for 2FA and the NPS is setup to authenticate the user is in the appropriate AD group. This allows the VPN to connect and then we use Identity Awareness for the access via roles. We are still working out the kinks to be honest and this is still in testing. We should be moving into production at the end of this year as we are migrating off a Cisco AnyConnect solution that works like advertised. We have had many headaches with CP Mobile Access VPN but I think that is because we are so used to using the Cisco AnyConnect and there are a lot of differences in the way the two function that we are still wrapping our head around. Hopefully this helps!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


