Hi guys,
I have ainadequate behaviour in the VPN client site, when the cluster is failover, all the user with MacOS, we see the message "USERNAME tried to connect, but you have reached the number of purchased licenses", and users with windows logean correctly.
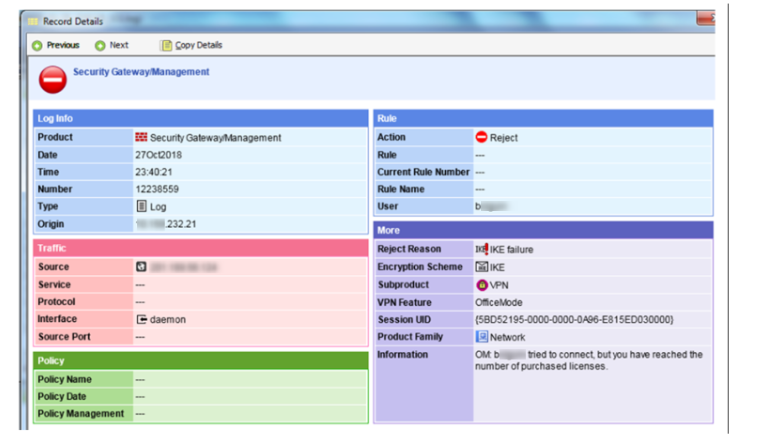
In a moment suspect that the device standby, did not have its licenses correctly loaded, but validate them and they are correct.
FW1 - Standby (Problem):
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log =~=~=~=~=~=~=~=~=~=~=~=
cplic print
Host Expiration Features
X.X.X.21 never cpap-sg1540x cpsb-fw cpsm-c-2 cpsb-vpn cpsb-npm cpsb-logs cpsb-sslvpn-200 cpsb-ia cpsb-sslvpn-5 cpsb-adnc cpsb-apcl cpsb-ips cpsb-urlf cpsb-av cpsb-abot-l cpsb-aspm XX-XX-XX-XX-XX-XX-XX
X.X.X.21 never CPAP-SG1540X CPSB-FW CPSM-C-2 CPSB-VPN CPSB-NPM CPSB-LOGS CPSB-IA CPSB-SSLVPN-5 CPSB-ADNC CPSB-APCL CPSB-IPS CPSB-URLF CPSB-AV CPSB-ABOT-L CPSB-ASPM XX-XX-XX-XX-XX-XX-XX
Contract Coverage:
# ID Expiration SKU
===+===========+============+====================
1 | XXXXXXX | 24Apr2020 | CPSB-URLF-L-2Y
+-----------+------------+--------------------
|Covers: CPAP-SG1540X CPSB-FW CPSM-C-2 CPSB-VPN CPSB-NPM CPSB-LOGS CPSB-IA CPSB-SSLVPN-5 CPSB-ADNC CPSB-APCL CPSB-IPS CPSB-URLF CPSB-AV CPSB-ABOT-L CPSB-ASPM XX-XX-XX-XX-XX-XX-XX
| cpap-sg1540x cpsb-fw cpsm-c-2 cpsb-vpn cpsb-npm cpsb-logs cpsb-sslvpn-200 cpsb-ia cpsb-sslvpn-5 cpsb-adnc cpsb-apcl cpsb-ips cpsb-urlf cpsb-av cpsb-abot-l cpsb-aspm XX-XX-XX-XX-XX-XX-XX
FW2- Active:
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log =~=~=~=~=~=~=~=~=~=~=~=
cplic print
Host Expiration Features
X.X.X.22 never cpap-sg1540x cpsb-fw cpsm-c-2 cpsb-vpn cpsb-npm cpsb-logs cpsb-sslvpn-200 cpsb-ia cpsb-sslvpn-5 cpsb-adnc cpsb-apcl cpsb-ips cpsb-urlf cpsb-av cpsb-abot-l cpsb-aspm XX-XX-XX-XX-XX-XX-XX
X.X.X.22 never CPAP-SG1540X CPSB-FW CPSM-C-2 CPSB-VPN CPSB-NPM CPSB-LOGS CPSB-IA CPSB-SSLVPN-5 CPSB-ADNC CPSB-APCL CPSB-IPS CPSB-URLF CPSB-AV CPSB-ABOT-L CPSB-ASPM XX-XX-XX-XX-XX-XX-XX
X.X.X.20 11Jul2017 CPSG-C-8-U CPSB-FW CPSB-VPN CPSB-IPSA CPSB-DLP CPSB-SSLVPN-U CPSB-IA CPSB-ADNC CPSG-VSX-25S CPSB-SWB CPSB-IPS CPSB-AV CPSB-URLF CPSB-ASPM CPSB-APCL CPSB-ABOT CPSB-CTNT CK-XX-XX-XX-XX-XX-XX-XX
Contract Coverage:
# ID Expiration SKU
===+===========+============+====================
1 | XXXXXXX | 24Apr2020 | CPSB-URLF-L-2Y
+-----------+------------+--------------------
|Covers: CPAP-SG1540X CPSB-FW CPSM-C-2 CPSB-VPN CPSB-NPM CPSB-LOGS CPSB-IA CPSB-SSLVPN-5 CPSB-ADNC CPSB-APCL CPSB-IPS CPSB-URLF CPSB-AV CPSB-ABOT-L CPSB-ASPM XX-XX-XX-XX-XX-XX-XX
| cpap-sg1540x cpsb-fw cpsm-c-2 cpsb-vpn cpsb-npm cpsb-logs cpsb-sslvpn-200 cpsb-ia cpsb-sslvpn-5 cpsb-adnc cpsb-apcl cpsb-ips cpsb-urlf cpsb-av cpsb-abot-l cpsb-aspm XX-XX-XX-XX-XX-XX-XX
In image appreciate that when rollback is executed, user can navigate again:
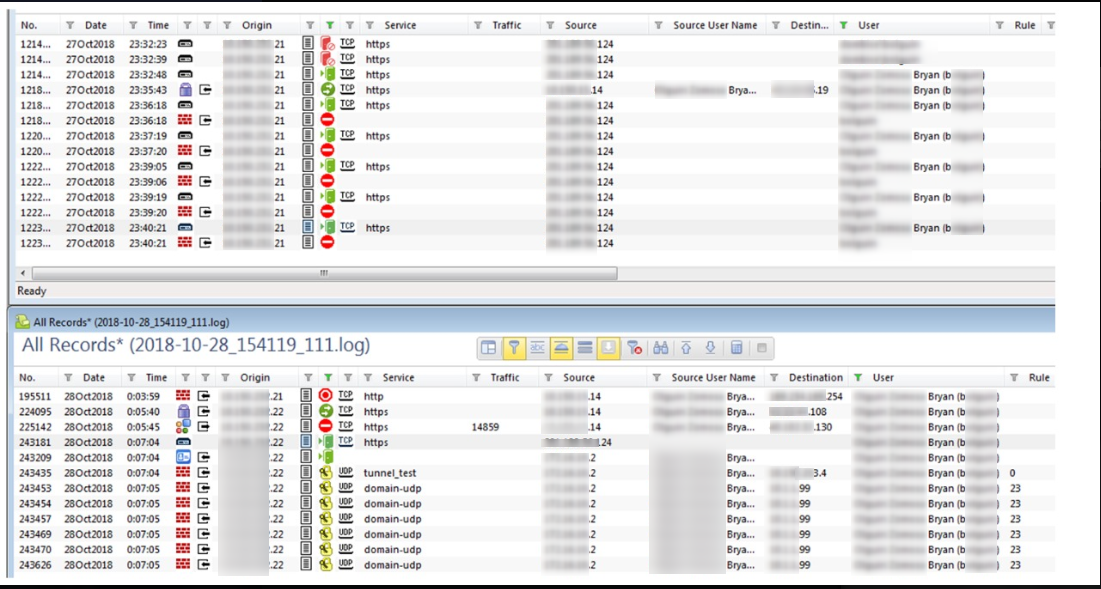
Log in, rollback:
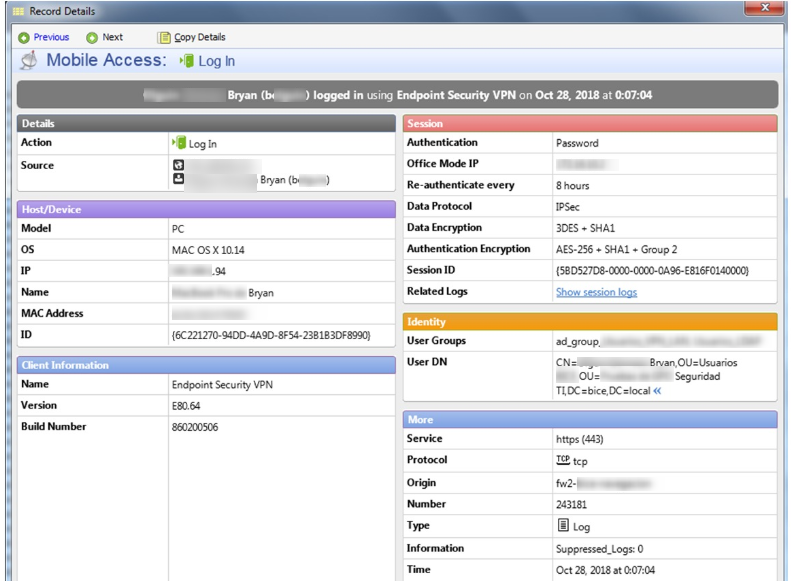
look for information about it but I did not find, have you ever been presented with this problem?
Thank you very much for your support.





