- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Checkpoint VPN with Microsoft 2-Factor Authenticat...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Checkpoint VPN with Microsoft 2-Factor Authentication
Hello everyone
I would like to share with you how I managed to get VPN users to use Microsoft Azure Multi-Factor Authentication.
I saw in some posts that this was possible by using MFA Server, but Microsoft stopped offering MFA Server on July 1, 2019.
What I needed to do:
1 - Office 365 users with MFA enabled.
2 - Dedicated NPS Server.
All Radius requests made to this server will have MFA directed to Microsoft.
3 - NPS extension for Azure MFA
This extension will direct your MFA requests to Microsoft.
You can find the installation and download instructions at the link below.
The user can define which method will be used in the Microsoft portal.
I tested the methods below on VPN Clients, Mobile Access and Capsule Workspace and they all worked perfectly.
- Notification through mobile app
- Verification code from mobile app
- Text message to phone
I hope this post helps you
Good luck
66 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks very much for taking the time to write this. Just finished a deployment for 1000 users,
Ruan
P.S. Just had one item that tripped me up for a while. A different team was handling the NPS, and we saw from the gateway that our Radius requests were not honored. Turns out that in a VSX environment the Radius request is sent by the root device (not sure what the correct terms is, VS0?) and not the virtual system. I don't have a lot of experience with VSX so maybe this is common knowledge - it wasn't for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We have set Radius and VPN to request MFA (Azure):
- we receive MFA request when authenticating on the VPN
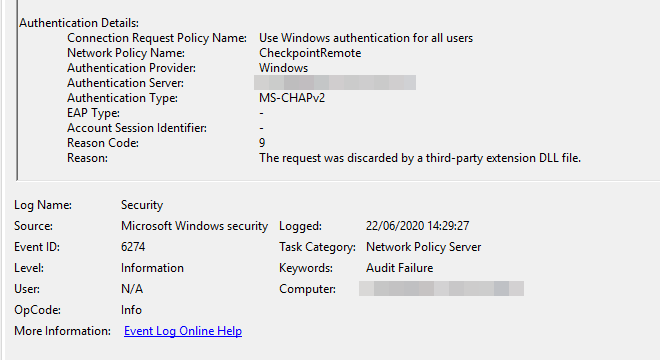
- then Radius network policy allow connection with the event 6272 (Network Policy Server granted access to a user.)
- 2 seconds later, the same network policy refuse the connection with the event 6274 Reason code 9 (Network Policy Server discarded the request for a user.)
Does anyone else have the same problem? any idea to fix this?
best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ruan!
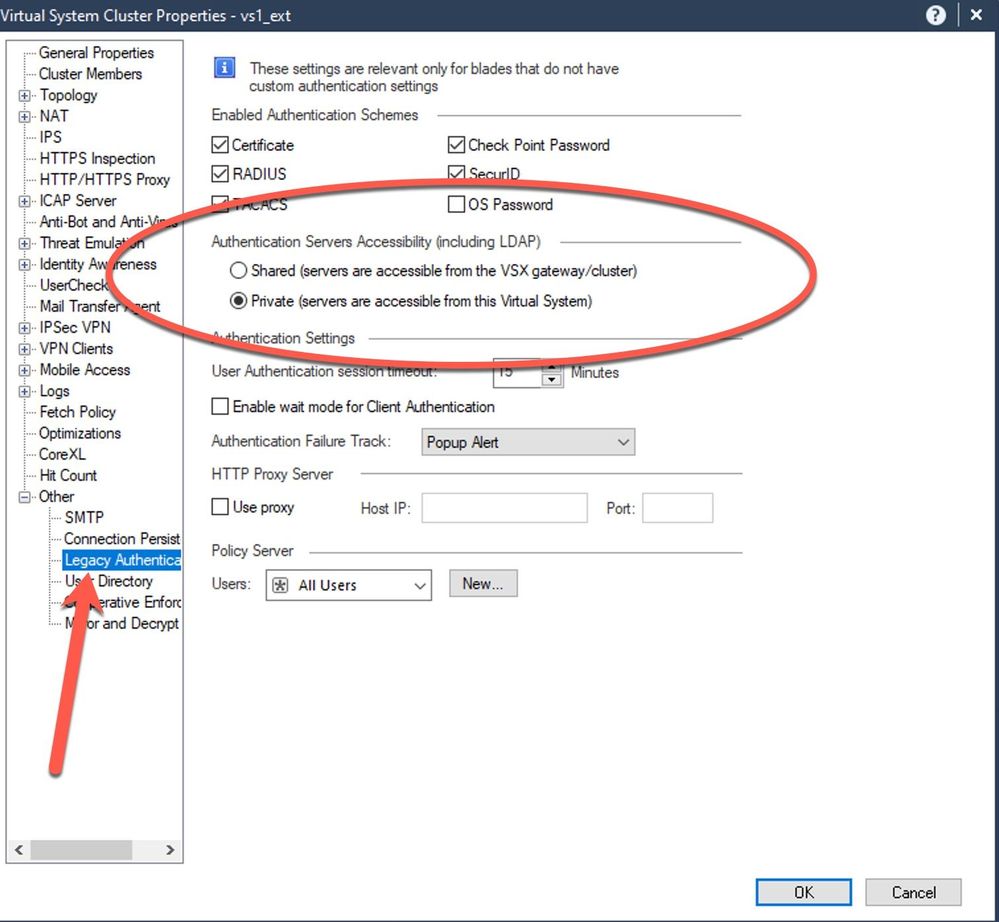
If you haven't already found out how to have the authentication request sent via the Virtual System instead of the VS0, there is a setting on the VS that you want to have send the authentication request, in the settings "tree" to the left when you open the VS configuration, under "Other" and then "Legacy Authentication".
Under the checkboxes for which Authentication methods to allow on the VS, there is a section called "Authentication Servers Accessibility (including LDAP)", where you change the Radio Button to "Private (servers are accessible from this virtual system)".
I have attached a screenshot of the setting below.
Good luck!
Kind regards,
/Jonas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jonas, thanks very much for that!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're most welcome, happy to help!
/Jonas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jonas,
Thanks for your insight. I have a similar problem. On the Checkpoint,the area for Authentication Servers Accessibility (including LDAP) doesn't show.
All other sections including 'Enabled Authentication Schemes' , 'Authentication Settings' 'Policy Server's are available.
Is there a way to make this happen (Ensure authentication servers are accessible from this virtual system) via CLI.
Please share if you know the command
Thanks for your insight. I have a similar problem. On the Checkpoint,the area for Authentication Servers Accessibility (including LDAP) doesn't show.
All other sections including 'Enabled Authentication Schemes' , 'Authentication Settings' 'Policy Server's are available.
Is there a way to make this happen (Ensure authentication servers are accessible from this virtual system) via CLI.
Please share if you know the command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I have a problem, i configured everything i think correctly (using guide i found and the posts here) when i lgoin to the vpn I enter my test user and password get the mfa asking to confirm and i get that authentication failed and i get a log in smart console that User does not belong to the Remote Access cxommunity. Any ideas what could be wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Make sure your AD/Radius group belongs to the community, as the message said
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is some error in the config. Wrong LDAP branch, or the user in not on LDAP. Check all the steps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could You please tell me more how to chec if the LDAP branch is wrong ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a very good tool for troubleshooting LDAP issued called ldapsearch that you can use either on the gateway or the management to check if the module can do LDAP queries, and if the account and DN's you use are allowed to query the LDAP server.
You can search Secure Knowledge for "ldapsearch" and you will get multiple answers detailing different troubleshooting scenarios involving LDAP.
(For example sk100163, Endpoint Security Client fails to connect to VPN Site with "Negotiation with site failed" error
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...)
Personally I also like to use the Windows tool, "Softerra LDAP Administrator" (Read/Write, costs money) or "Softerra LDAP Browser" (same tool, but Read Only and free for all usage) to troubleshoot LDAP issues as it gives you very good details about your LDAP catalog, and all the objects and attributes involved.
I also like to find the objects and DN's in "LDAP Browser" and do copy-past into my configuration, making sure that I haven't misspelled anything in the FQDN's etc.
Good luck!
Best regards,
Jonas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I tried the ldapsearch tool and it queries the server and gives good information from both the managment server and gateway, I fiddled witht he branch settings and the effect is I get an usser not know error so i reverted that but im back to squeare one, is there i way I can check the RAD_ group if it works fine? (its empty as the manual said)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
You can check the logs in the event viewer of the radius server.
If there is more than one network rule try to leave that rule at the top.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you run a tcpdump on the gateway or Wireshark capture on the RADIUS server to look at the attributes being passed back? If the server is not passing back the correct attribute the gateway cannot associate the user with a group (RAD_xyz) and therefore will say that the user is not part of the community. So you might be getting a RADIUS access accept from the RADIUS server but a group matching failure due to the wrong attribute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi anybody has this error?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, have seen the same message, something I need to investigate further but possibly just the user not responding to the Azure MFA prompt in time so the NPS Azure MFA extension times it out and reports so back to the event log.
I've raised a SR for our issues trying to get the RADIUS attributes to match the RAD_<attribute> group. tcpdump shows the correct type (26) being sent with the correct vendor code and values but the gateways appears to be failing to associate it with the group and therefore with the RA community. Initial response from TAC was that the configuration looked right.
Will schedule another test window to repeat the implementation and run a VPN debug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i also opened a support, Microsoft found radius was correctly set, this error message according to Microsoft is generic and due a Checkpoint misconfiguration.
@DeletedUser can't you share a full procedure to connect Checkpoint VPN and Azure MFA, it is obviously causing problems
and the other VPN got their own procedure 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
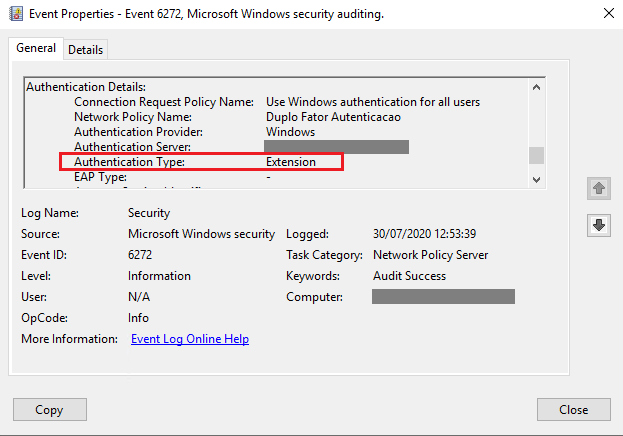
I advise you to review your settings on the radius server.
Your type of authentication is like MS-CHAPv2, and see how my log looks. Authentication type: Extension.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi we finally found the problem, it was due to the secret shared key, Checkpoint doesn't accept special characters.
thanks all for the help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how do i switch the MFA from one time passcode to mobile app method?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is set on the individual users Microsoft account. It is a user preference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i have been able to get this working great with MFA but if a user is to "change logon option" on checkpoint vpn client they can bypass the MFA and simply connect with username /password credentials. Where would i find the setting to block this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good question nflnetwork29. I have the same problem. If the users are able to change between MFA and user + password on checkpoint mobile client the security layer is compromised. Did you manage to make this work? Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can diable this by going to SmartConsole - > open the security gateway/cluster object - > under VPN cleint, select Authentication. On the right hand side panel, you would see "settings". Click on that and uncheck "Allow newer client that support multiple login options to use use auth mehod"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I have enabled MFA with Azure. Authentication is working fine. But after connecting to Mobile access VPN, Users are not able to access internal subnet which has security scan check enabled while they are able to access other internal subnet for which security scan check not enabled.
Getting error "Unauthorized SSL VPN Traffic" for subnets which are having security scan check enabled. We have configured Native application for all internal subnet and all applications are in same rule.
We are moving MFA from RSA to Azure and everything is working fine for RSA authentication
Does anyone has any idea why this is happening?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Greetings,
Once authenticated in VPN, this issue don't have link with MFA.
Unauthorized SSL VPN Traffic is a traditional error and your cause it depend on about your configuration. Below are some SKs that are helpful.
SNX traffic is dropped with "Unauthorized SSL VPN traffic" (checkpoint.com)
After authentication to Mobile Access Blade, cannot access internal resources with error "Unauthoriz...
Traffic initiated from internal host towards SSL Network Extender client is dropped with "Unauthoriz...
Alisson Lima
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are all set now. I just want to share below URL which is very helpful for troubleshooting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share with the community, what was the actual finding in your case? what was the issue, how did you fix it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
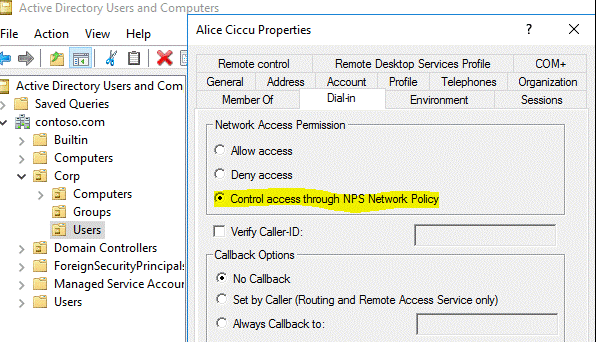
Some users are able to authenticate and access internal resources but some users are not able to authenticate. Getting message "Wrong username or password". It is saying "Unauthorized access" in smart log.
We gone through below document and there is one setting "control access through network policy" which needs to be enable in user property.
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension-vpn
Checkpoint VPN with Microsoft 2-Factor Authentication
Hello everyone
I would like to share with you how I managed to get VPN users to use Microsoft Azure Multi-Factor Authentication.
I saw in some posts that this was possible by using MFA Server, but Microsoft stopped offering MFA Server on July 1, 2019.
What I needed to do:
1 - Office 365 users with MFA enabled.
2 - Dedicated NPS Server.
All Radius requests made to this server will have MFA directed to Microsoft.
3 - NPS extension for Azure MFA
This extension will direct your MFA requests to Microsoft.
You can find the installation and download instructions at the link below.
The user can define which method will be used in the Microsoft portal.
I tested the methods below on VPN Clients, Mobile Access and Capsule Workspace and they all worked perfectly.
- Notification through mobile app
- Verification code from mobile app
- Text message to phone
I hope this post helps you
Good luck
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter