- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Certificate VPN authentication against LDAP us...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Certificate VPN authentication against LDAP using userPrincipalName (R80.10)
Has anyone tried and succeeded in this?
Since R80.10, sk61060 is no longer applicable and the relevant configuration is performed directly on the gateway object in VPN CLients -> Authentication. In the personal certificate i have
- Fetch Username From: Subject Alternative Name.UPN in the Login option
- Common lookup type: User-Principal-Name / UPN (userPrincipalName) in the User Directories
The first part seems to be working OK. I can verify in the logs that UPN is extracted from the certificate but it is not matched against an UPN in LDAP. Login fails with unknown user. If i change everything to default (DN based), it works OK.
If i change the Fetch Username From part to DN, and leave the lookup to be UPN based, authentication succeeds. Looks like the lookup is always DN based, no matter what is selected. I even tried to use custom lookup with userPrincipalName, but the behavior is the same.
I am currently testing this on R80.10 with Jumbo Hotfix Accumulator Take 91
ETA:
Tried with Hotfix Accumulator Take 103 (latest). No change.
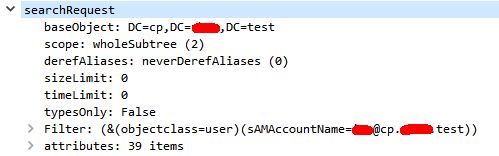
I am currently running some packet capture of the FW-DC communication an concluded that the above configuration results in LDAP search based on sAMAccountName instead on userPrincipalName
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even though the R80.10 GUI has an option for this, can you verify the settings are set as described in sk61060 with GUIdbedit?
I'm thinking alternative_subject_field, but maybe the other parameters as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally managed to make it work by using a combination of SmartConsole configuration for the username extraction part and GuiDBEdit configuration for the lookup part, but i don't think that this is the way it was intended to work. Even that took some trial and error to make it work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aaaaaaand, that is not the end of my worries. I am experiencing, a similar issue when connection with Capsule Connect on IOS. This time, even the certificate parsing is stuck to default (DN). I have modified every sk61060 related item that seemed relevant to the mobile clients, but with no success.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possibly this SK?
Otherwise it's probably worth a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ended up with a TAC case. Lets see what happens next.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have exactly same issue. Can you post the solution or SR number?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're using a 3rd Party Certificate, it might be overriding the configuration.
sk115637
The 3rd party Root CA has two parameters that define the user fetch process:
use_cn_to_fetch_user (default: false)
use_principal_name (default: false)
***If one of this two parameters are enabled (value=true) then the certificate parsing rules defined in the realm relevant for the VPN blade will not be applied after the certificate chain is completed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The certificate parsing seems to work OK, according to the GUI settings. The subsequent LDAP search is not working properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you ever get this solution working? I am experiencing the same thing thing.
I have been able to make it all work(including Capsule VPN logins using 3rd party certificate), In a test environment, using a combination of modifying VPN Client Authentication fields in Smart Dashboard, and editing the VPN realm using guidbedit.
But the the steps I had to take are not very intuitive, and took days of troubleshooting.
I was just wondering if TAC ever gave a reason, or better solution that didn't involve guidbedit, of if this was resolved in maybe R80.30?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
can you describe what fields you have changed in guidbedit. I am experiencing the same problem.
Regards,
Jan
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


