- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Automatic certificate renewal
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Automatic certificate renewal
Hello,
With the maximum validity period of certificates becoming shorter all the time it is a challenge for large deployments to renew everything. Is there a known solution to automate this for the remote access solutions of Check Point? And maybe even the Gaia interface as well? (some of our customers even have an external wildcard certificate on their Gaia webinterface).
Things like certbot don't apply for the VPN solution I guess, or maybe via the API?
Thanks in advance,
Regards,
Erik
Labels
- Labels:
-
Management
- Tags:
- certificates
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The script to do this was released a few months ago: https://support.checkpoint.com/results/sk/sk182070
26 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're using the ICA, then in theory, the certificates should renew automatically.
For an external CA, I'm not aware of an easy way to automate this stuff as there aren't really APIs or CLI commands to do this that I'm aware of.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see in API v1.8 there are certificate installation options for the platform portal and the usercheck page, but not for the mobile access portal (or I did not find it yet). Let's hope this will be added in the near future as well!
Regards,
Erik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,
I have question regarding the ICA renewal, is it any way to ICA will be automatically renewed ? eg. by installing new software/hot fix ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NO - at least if you do an upgrade, not fresh install without db import 8) After Jumbo install, GAiA WebGUI may need a new exception for the self-signed cert in browser, but that is all...
See sk158096: How to renew an Internal Certificate Authority (ICA) certificate for on-purpose renewals - sk164255: SIC Certificate fails to renew automatically for issues with that!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We now do an automatic renewal of the ICA as of R81.10 JHF 95 (PRJ-44576, PMTR-90463).
I presume this will also get rolled into other JHF streams.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There must be something for this right?
Can't believe that we still need to do this time consuming job by hand every year again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Did you find any solution on this problem.?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
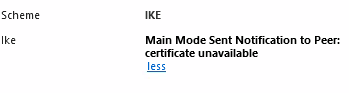
i just had the same issue now, VPN from a remote GW just stopped.
Not Valid Before: Mon Nov 15 12:55:30 2021 Local Time
Not Valid After: Wed Nov 16 12:55:30 2022 Local Time
But iam not sure if VPN certificates really get renewed automatically?
Where in a guide/SK is this written?
Anyway, i have seen this too often i will open a case and ask TAC.
i will keep u posted!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I have the same question, I talked to my certificate provider, and they told my, that I should expect that the lifetime on certificate will go to 3 month or lower, so a automated way of doing it is a must.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect we'll have a way to update this information via API in the future.
Having said that, I highly recommend approaching your Check Point SE with your precise requirements for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The future is NOW.
You are rather later with this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any planes to auto renew the internal certificates on the gateways they now only have a lifetime on 1 year, and are used with identity collector, vpn and more, and do a renew on +100 gateways takes time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Last I heard, there was a plan to provide an automated mechanism to do this in the near future...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Starting from R81.10, all IKE certificates are valid only for 1 year by default.
If customer has many FWs used for RA or S2S, where IKE certificate must be valid, it will help if there is some automated way to renew defaultCert automatically (like SIC, InternalCA).
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hopefully this will get sorted. VPN certificate expiry has caused us pain.
And for one customer who uses SAML, this needs a proper certificate and so far LetsEncrypt isn't available so that's entailed a different manual process!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I keep track of the expire dates in our systems so we get alerted before it expires. Just make a note in a calendar or internal system it is not that difficult. Also when the certificate will expire soon Check Point will give alert at the policy push.
So instead of waiting for Check Point to get it 'sorted' I would recommend to check your own procedures.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The script we are planning to make available to manage IKE certificates has an "in progress" SK for the functionality (only visible for Check Point employees).
Unfortunately, I do not know the timeline for it, though it is expected to be available as part of R82 and backported to R81.x releases via JHF.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any updates?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The script to do this was released a few months ago: https://support.checkpoint.com/results/sk/sk182070
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please can this functionality be brought to Infinity, we have a growing landscape of managed clients where it's pathetic that inter-site VPNs stop working when the certificate expires.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently, this requires a manual action (i.e. running the script), which I assume TAC can run for you if needed.
We are planning to make this process more automatic, which I assume will also be available in Smart-1 Cloud.
This is planned for early next year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This sounds rather strange - 3 months or lower ? Then we better stay with the internal CA...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://letsencrypt.org/docs/faq/
What is the lifetime for Let’s Encrypt certificates? For how long are they valid?
Our certificates are valid for 90 days. You can read about why here.
There is no way to adjust this, there are no exceptions. We recommend automatically renewing your certificates every 60 days.
https://letsencrypt.org/2015/11/09/why-90-days.html
Why ninety-day lifetimes for certificates?
Nov 9, 2015 • Josh Aas, ISRG Executive Director
We’re sometimes asked why we only offer certificates with ninety-day lifetimes. People who ask this are usually concerned that ninety days is too short and wish we would offer certificates lasting a year or more, like some other CAs do.
Ninety days is nothing new on the Web. According to Firefox Telemetry, 29% of TLS transactions use ninety-day certificates. That’s more than any other lifetime. From our perspective, there are two primary advantages to such short certificate lifetimes:
- They limit damage from key compromise and mis-issuance. Stolen keys and mis-issued certificates are valid for a shorter period of time.
- They encourage automation, which is absolutely essential for ease-of-use. If we’re going to move the entire Web to HTTPS, we can’t continue to expect system administrators to manually handle renewals. Once issuance and renewal are automated, shorter lifetimes won’t be any less convenient than longer ones.
For these reasons, we do not offer certificates with lifetimes longer than ninety days. We realize that our service is young, and that automation is new to many subscribers, so we chose a lifetime that allows plenty of time for manual renewal if necessary. We recommend that subscribers renew every sixty days. Once automated renewal tools are widely deployed and working well, we may consider even shorter lifetimes.
the future was already before 2015, almost 10 years from now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Folks,
and what about all those third party certificates for all Multiportals, HTTPS Inspection (in & outbound)
is there a documented way to have an overview of them?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You cannot use the script to renew third party certificates, but it should show them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Almost a year late and still no solution to batch renew certificates 😞 Or I'm I missing something ?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter