- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: list of different IP addresses to be blocked
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
list of different IP addresses to be blocked
hi,
i have 2000 plus list of IP addresses, how can i block them all bi directional blocking in my checkpoint firewall without typing all those individually?
31 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Method 1
How to block traffic coming from known malicious IP addresses
Method 2
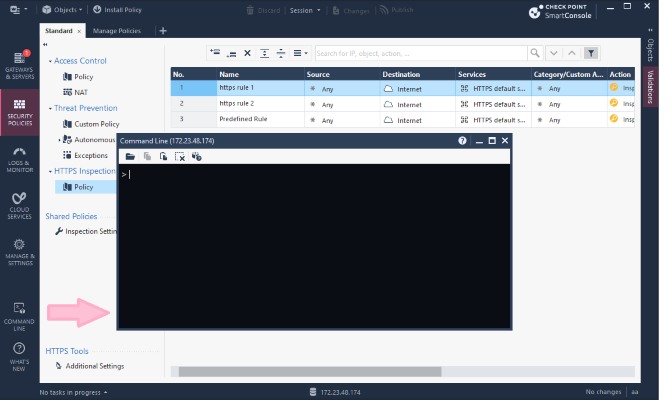
The SmartConsole CLI can be directly accessed from within SmartConsole by clicking the ![]() icon on the bottom left corner.
icon on the bottom left corner.
SmartConsole -> Management CLI:
Just add the required syntax to your IP addresses to create host objects and one host group for them. Copy & Paste this to your SmartConsole CLI in order to have a group containing all block IPs created. Then create a rule that blocks all access to this group. Done.
Method 3
fw samp is your friend.
Method 4
sim dropcfg is your friend.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great summary Danny!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is awesome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
but that one is around 2000 plus IP addresses, is there a way for me not to
manually key in all those IP addresses? may using notepad or csv file?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Using the above methods, you can write a script to read from whatever file you have the IP addresses into.
You could also use some of the scripts that are already present on CheckMates to help you with this.
This is just one example: CLI API Example for exporting, importing, and deleting different objects using CSV files (v 00.25.01...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
thank you!
lets say i already put all the 2000 plus ip addresses in a csv file, then i
type this command "cli_api_import_objects_from_csv.sh" i have a question,
where i must save my csv file in my local drive for the fw to ask me the
location of the file to be imported? and also smart console i just fire up
the CLI then type the command cli_api...?
please enlighten me
On Fri, Jan 19, 2018 at 10:34 AM, Dameon Welch Abernathy <
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where the file should be saved for this particular script is described in the lengthy post with that script, please read it carefully.
It's meant for bulk import/export of a lot of objects, so may not be the best tool for your job.
Another possible option: R80 PowerShell Module
But a simpler option is to just call the CLI directly and import the CSV.
This process isn't nearly as well documented as I thought it would be, but we're about to fix that ![]()
First of all, the CSV file should be in the correct format.
The first row refers to parameters you would pass the add host command as documented here: Check Point - Management API reference for add host
The minimum parameters needed are name and ip-address.
Since you want to put them in a group, might as well do that as they are created.
For this example, the objects will be added to a group called BlockGroup:
name,ip-address,groups.1
host1,192.0.2.1,BlockGroup
host2,192.0.2.2,BlockGroup
host3,192.0.2.3,BlockGroup
If the group doesn't already exist, you can use the following CLI command on the management server to create it first: mgmt_cli -r true add group name BlockGroup
To then import the CSV file, use the following command on the management server, which reads the file from the current directory: mgmt_cli -r true add host --batch import.csv
Note: You will probably need to break up the CSV file into smaller chunks (no more than 500 items per file).
Otherwise you may experience issues as described here: https://community.checkpoint.com/message/6809-re-creating-multiple-object-via-csv
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So every ip address will be host/object? therefore, 2000 host?
Is there any easiest way wherein we just put those list of IP addresses then automatically blocked. And if there is a false-positive, we can also easily removed that IP address in the list.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Christopher,
With this method, there will indeed be 2000 host objects created and added to a group used in directionnal blocking rule. If you do not want to create objects, you may have a look at SAM rules (here: How to create and view Suspicious Activity Monitoring (SAM) Rules).
SAM rules does not need to create an object, you can add the IP addresses directly in the blocking rules, monitore them, and remove them.
However, SAM rules are CPU intensive. So you better use a traditionnal security policy rule and a group of hosts object. Sam rules should only be used in emergency conditions (as they do not need a policy installation to be added or removed), and IP block should be move to your security policy rule as fast as you confirm there is no false positive.
I hope this helps,
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
is there a way not to manually typing all those 2000 plus different IP
addresses to be part of the host object?
On Fri, Jan 19, 2018 at 3:56 PM, Bruno LABOUR <donotreply@checkpoint.com>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For SAM rules? The KB shows there is a cli comand "fw sam_policy" that you could use with a script to parse your inject everything. However, i would not recommand you to use SAM to block 2000 IP addresses when you can easily do it also with either mgmt_api or dbedit scripts depending on the version you are running.
All the given solution are script-capable or bulk by nature, so i do not catch you very well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Bruno
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent point about CPU implications Bruno. Very important for large and/or heavily loaded environments when every CPU % counts. Maybe https://community.checkpoint.com/people/dantr917b8439-9d5c-34f0-b86a-f0e1b0a14cbd could update original article with CPU impact for each of the options. Just for clarity ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should probably use fw samp instead, which is SecureXL friendly (SAM rules are not).
And to Dirk Casomo's question, you would write a script that reads your file of IPs, executing the necessary commands.
Or use the scripts in the following SK: How to export Check Point logs to a Syslog server using CPLogToSyslog
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i try typying this command "*mgmt_cli -r true add group name BlockGroup" on
the management server CLI console, but invalid command, also in expert mode
bash command not found?..hhow to execute this? im using R77.30 smart
dashboard*
On Sat, Jan 20, 2018 at 12:19 AM, Bruno LABOUR <donotreply@checkpoint.com>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mgmt_cli command is only in R80 and later.
In R77.30 you will have to script this using dbedit or fw samp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
so for this matter i am using r77.30 can you please provide me the script
for me to import the csv file with 2500 plus hosts to do away with manual
typing of those different P addresses as network objects HOST. thank you
On Mon, Jan 22, 2018 at 11:40 PM, Dameon Welch Abernathy <
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Given that you're using R77.30, your best bet would be to use the first method suggested by Danny Jung in his original response to your message: How to block traffic coming from known malicious IP addresses
It is definitely the easiest to automate on your release and will block things fairly efficiently.
This "block list" will not show up in the rulebase at all but also does not require a policy push to modify the list, either.
As I mentioned, you could also automate with dbedit as well.
This will require you to write a specific script for your needs, however, as I'm not sure one is ready made for the purpose you describe.
It would have to be customized a bit to your environment as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Follow up question, Is there a limit with regards to object? How many object we can create in R80.10 and R77.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
example i type the command in the fw console , mgmt_cli -r true add host --batch import.csv do i still need to put the path of the csv file which is on my desktop?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The command is executed on the management station, not the firewall.
The CSV file would need to be uploaded to the management station (with scp or similar).
If you do not run the command from the same directory that contains import.csv, you will have to enter the path to it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if i have a standalone setup using 1 firewall, you mean my pc has installed
the smartdashboard on it, then the CSV is on the desktop save. is ok
already, then ill jus include the file path?
On Mon, Jan 22, 2018 at 12:18 AM, Dameon Welch Abernathy <
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your specialist comments. That is i wanted to find.
God bless you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would have been better had this question not been posted a few times in unrelated threads.
However I will also add to what Danny Jung has said that if you're not using R80+ management, you can create objects by CLI using dbedit: Using a dbedit script to create new network objects and network object groups
You would create the relevant network objects, add them to a group, and use that group in the rulebase with a "drop" rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I saw this alternative solution to list based block : https://community.checkpoint.com/docs/DOC-2002
It may provide an additional resource for learning how to approach this problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can suggest sk103154 How to block traffic coming from known malicious IP addresses, this also could help !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the very first link I provided in my initial response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, i did not see that the provided link pointed to the sk103154 😞
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can anyone tell me more about the use of the dynamic_objects command on the gateway? Looks like it is used under the covers of the https://community.checkpoint.com/docs/DOC-2002 which was mentioned above.
My specific use case is an R80.10 management server and R77.30 gateway.
I have been using SAM rules and refreshing hourly but the list is about to grow to a 1,000 (from ~350) and want to be cautious of resource utilization. Will use of dynamic object in management with dynamic_objects command on gateway increase CPU and/or Memory significantly? How does it compare to SAM rules (better on resources or worse)? This looks like a promising alternative to SAM rules and curious what others' experiences are? SAM rules have worked well so far but weary about where the tipping point is.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 14 | |
| 8 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter