Greetings everyone,
Long time lurker, first time participant here.
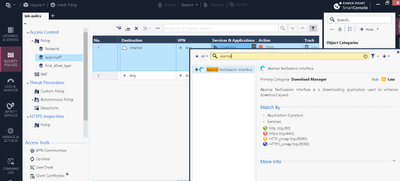
I had a recent issue in a costumer with updatable objects. Basically, a site that should not be allowed, was accessible through a UO rule.
The site in question is www.ford.pt, and was being matched by two updatable objects: Check Point Services on rule base and Office365 Worldwide Services on HTTPS Inspection (bypass rule).
www.ford.pt resolves to two akamai IPs:
Non-authoritative answer:
Name: e24220.dscx.akamaiedge.net
Addresses: 2a02:26f0:7900::172f:bd3a
2a02:26f0:7900::172f:bc78
23.47.189.145
23.47.189.160
Aliases: www.ford.pt
www.ford.pt.edgekey.net
Using domain_tools we were able to see that 23.47.189.145 matched office365 FQDNs and cws.checkpoint.com
Given IP address: 23.47.189.145 |
---------------------------------------------------------------------------------------------------
| Domain name | FQDN |
---------------------------------------------------------------------------------------------------
| office.net | no |
| office365.com | no |
| r3.res.office365.com | yes |
| r1.res.office365.com | yes |
| r4.res.office365.com | yes |
| cws.checkpoint.com | yes |
| www.bing.com | yes |
| akamaiedge.net | no |
Which we can confirm:
Name: e31055.dscd.akamaiedge.net
Addresses: ...
23.47.189.155
23.47.189.145
Aliases: cws.checkpoint.com
cws-31055.checkpoint.com.edgekey.net
Name: e40491.dscd.akamaiedge.net
Addresses: ...
23.47.189.145
23.47.189.147
...
Aliases: r1.res.office365.com
wildcard.res.office365.com.edgekey.net
In sk131852 is stated that the domains are resolved to IPs, and these are the ones used: "The updatable object can be used in Access Control policy's source and destination columns and is matched on SYN packet according to IP only (the domains are resolved to IPs)."
This ends up allowing unintended access, specially when using CDNs like Akamai. What would be the best strategies to handle this?
In this specific case we are talking about machines that should not have any internet access except to some pre-defined destinations, but have Harmony Endpoint installed and need to access the necessary services for updates and signatures. We are looking into creating a supernode to handle this problem, but we use several UO in different rules and the problem might arise in other machines.