- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: The flow time of the logs seems different. fl...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The flow time of the logs seems different
Hello all,
I have Checkpoint MGMT R80.20 Smart Console and ClusterGateway R.80.20 . I looking logs with Smart Console.
Why the time of the logs is different. The time of the mgmt time and the gateways are the same. ntp server is in use. they all appear the same time?
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
check
fw monitor -e "host(x.y.z.w) and host(a.b.c.d), accept;"
are the time-stamps in a proper time frames to the MGMT/GW ?
also check the fw log and cpview - ntp must be not entirely in SYNC with NTP servers or you've got some routing issues mate
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you might be seeing is consolidated logs and the time shown is the "start" of the the consolidated session.
You might drill into a few of those just to confirm that suspicion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually if you drill down on it it will (literally) sort itself out.
If you log both connections and sessions you will see the connection as soon as the SYN packet is received.
The session will only show in the log when it is finished.
This is something people really need to get used to with R80.
A sound understanding of Connections, Sessions and how the Acess Control is different from the Threat Prevention takes a bit of playing around with in order to full get a grasp on it.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I look log out put , I see the session logs time is creation time .so the real time seeming wrong . is this normal? how can ı see last update time in logs.. ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually. The log is correct.
The session starts at 10:58 so that information is shown in the overview.
The session can only be listed once it's done so that happens at 11:30
So you will see it among other entries around 11:30 when you follow the log in real-time.
This is exactly the point I am trying to make.
It takes getting used to the way how sessions and connections can be logged completely differently.
Each timestamp is for the start of the log event. Not the end time.
I don't see why you want to see the end times in the overview. I would say the start of events is the most relevant information.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Session Logging is new in R80+ management, while Log Suppression was around earlier than that and sometimes gets confused with Session Logging. Here is an excerpt from some content I recently developed explaining the difference with screenshots:
Module 6 – IPS Logging
Session Logging
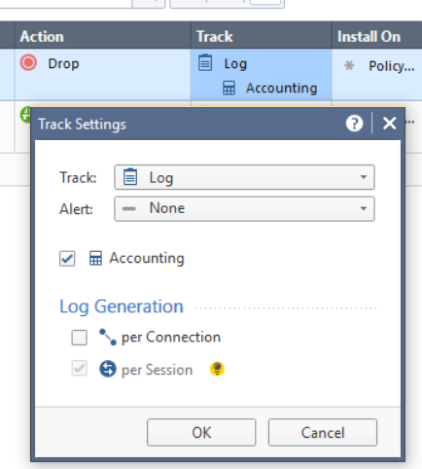
- Although not directly related to IPS logging, R80.10+ management by default will attempt to consolidate individual connection logs into a session log. This feature is commonly confused with Log Suppression which is quite relevant to IPS logging and covered next.
- A connection log typically only contains very basic information such as Layer 3 and Layer 4 information, while a session log is a collection (or superset) of individual connections.
- A session is a period that starts when a user first accesses an application or site. During a session, the gateway records one log for each application or site that a user accesses. All activity that the user performs within the session is included in the single session log.
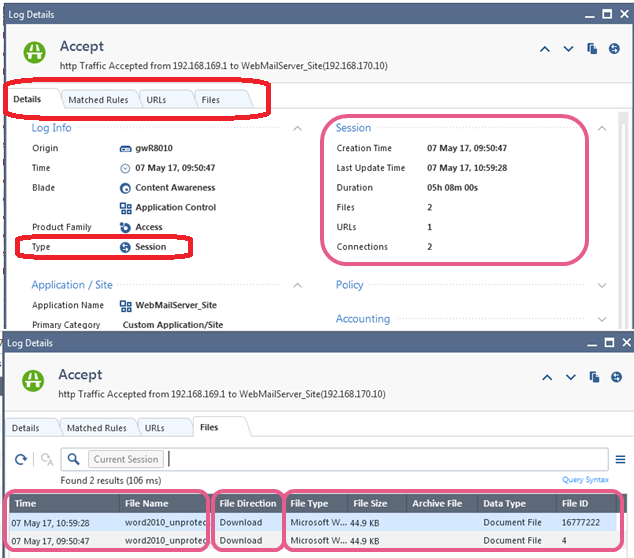
- Note the multiple tabs (such as “Matched Rules”) in this single log entry, don’t miss these as they contain valuable information!
- For more information about session logging see the CheckMates article “Infinity R80.10 "Cool Feature of the Day" – Session logging” (from which the above screenshot was taken) by Moti Sagey at: https://community.checkpoint.com/message/6279
- To determine the actual number of individual connections made during a session, see the Suppressed Logs field of the log (not shown above).
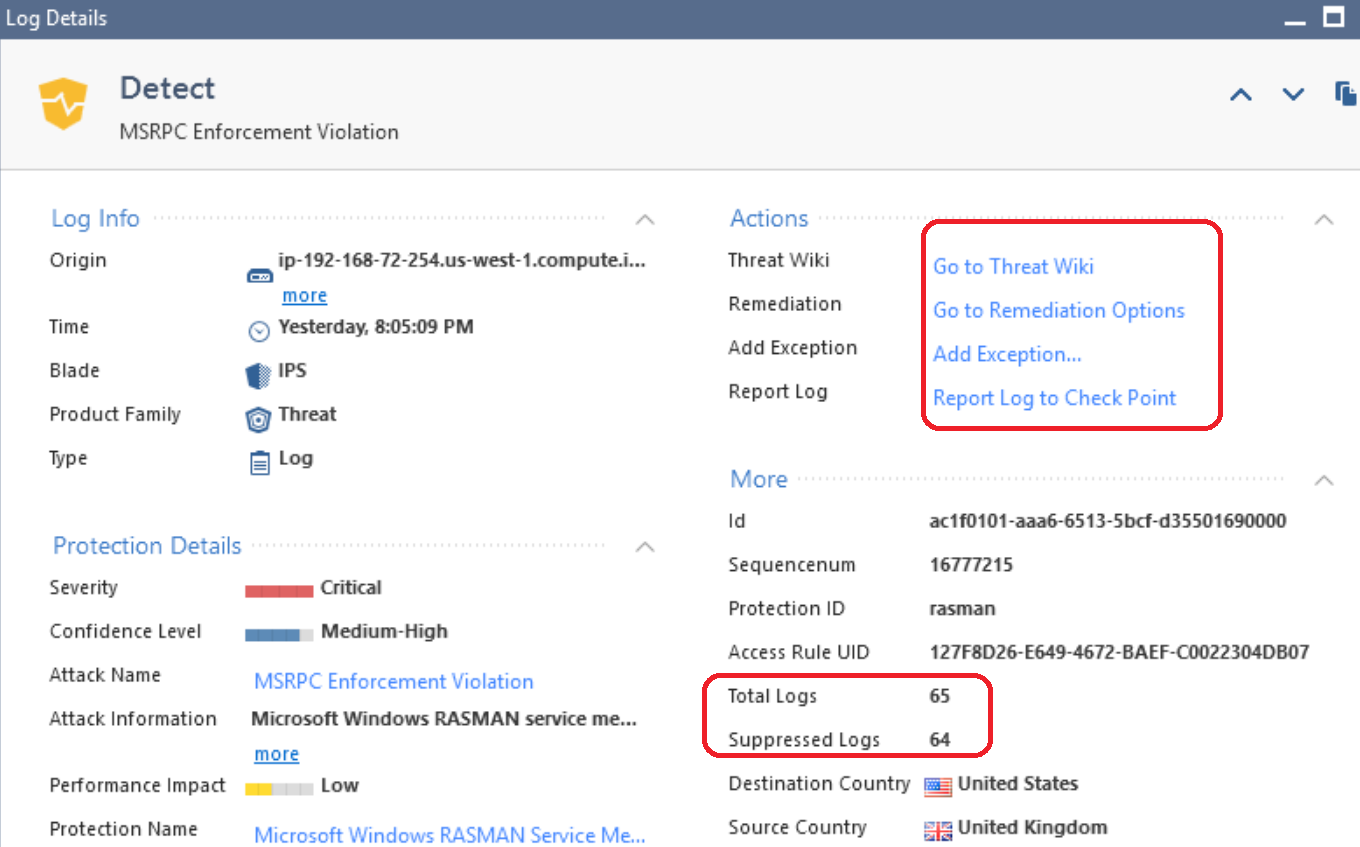
- When a ThreatCloud IPS Protection is matched and Track is set to Log, a log entry is generated. Within a period of two minutes, if the same IPS Protection is matched again with all the same connection attributes (IP addresses, ports, etc) a second log entry is not generated. The Suppressed Logs counter of the original log entry is simply incremented. Note that Log Suppression does not occur for logs generated by Core Activations or Inspection Settings.
- After two minutes measured from the first detection of this attack, if the same attack is still ongoing a new log entry is created and its Suppressed Logs counter is incremented.
- Note that when viewing an IPS Log Entry, numerous actions are available including:
◦ Viewing the attack attributes at the Check Point ThreatWiki website
◦ Creating an Exception (covered later in this module)
◦ Viewing Remediation Options
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 16 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


