Hi,
thanks for the tip.
File Name Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
MD5 7111558360b5d000e7452576fb76934b
SHA1 cd26cc0b793e80afead0cf559340c23fb9df7f3d
SHA256 0a56cf2a2c4c6b136f408d1827ddf4b18116ac6dbe512566a76a0cf7f71b2e6b
Download file with Iron Version 108.0.5500.0 (Official Build) (64-bit) to a windows box.
---
Appears on windows:
Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
PS C:\Users\... Get-FileHash Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
Algorithm Hash Path
--------- ---- ---
SHA256 0A56CF2A2C4C6B136F408D1827DDF4B18116AC6DBE512566A76A0CF7F71B2E6B ...
---
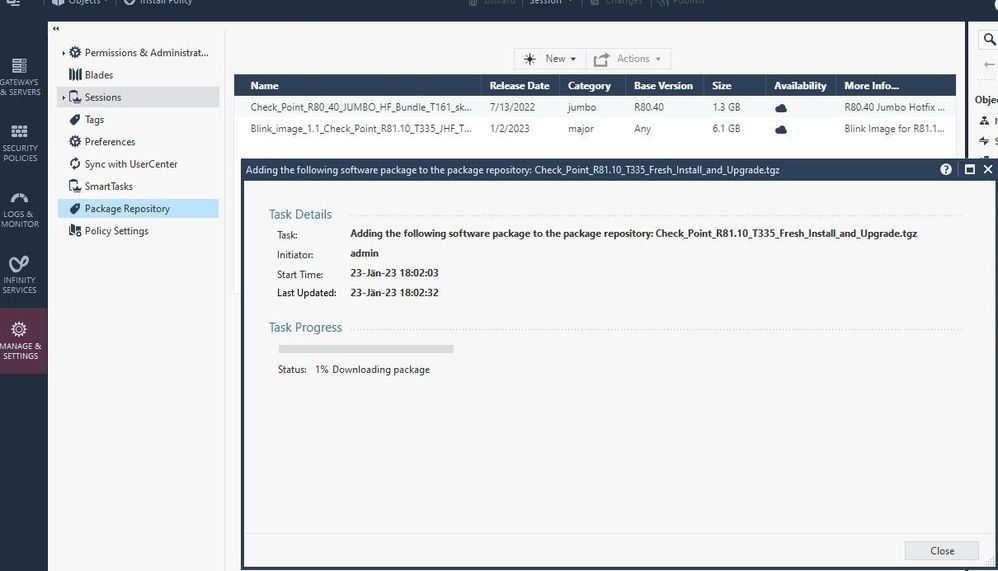
Upload to CheckPoint Management
[Expert@MDS:0]# find ./ -name Check_Point_R81.10_T335_Fresh_Install_and_Upgrade*
./var/log/CPda/repository/CheckPoint#Major#All#6.0#5#3#R81.10_ignis_main_T335/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tgz
./var/log/CPda/metadata/CheckPoint#Major#All#6.0#5#3#R81.10_ignis_main_T335/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade_METADATA.tgz
./var/log/opt/CPsuite-R81.10/fw1/tmp/RepositoryManager/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
./var/log/opt/CPsuite-R81.10/fw1/tmp/RepositoryManager/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
./var/log/PackageRepository/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade
./var/log/PackageRepository/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade/metadata/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade_METADATA.tgz
./var/log/PackageRepository/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade/metadata/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade_METADATA
./var/log/PackageRepository/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade/metadata/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade_METADATA_EXTENDED.tar
./var/log/PackageRepository/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade/package/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
./var/log/SOFTWARE/Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar
So at the end
When I search in SmartConsole | Upgrade Version , there is a need to have the exact file name in tgz format
Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tar -> NOTHING found
Check_Point_R81.10* -> NOTHING found
Check_Point_R81.10 -> NOTHING found
Check_Point_R81.10_T335_Fresh_Install_and_Upgrade.tgz -> found
Digging into that, I can't see a browser issue.
However, doing now Package Verification for a specific gateway, it ends up with verification failed.
Package is not valid for installation on the relevant Security gateways.
b.t.w.
we used this package already multiple times on the same gateway model but with CPUSE/CLISH and it worked perfect.
Looks like I need to raise a TAC case.
Thanks again
Regards