- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: NAT Rules for multiple IP Addresses?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NAT Rules for multiple IP Addresses?
This may be a pipe-dream, but can I somehow create a NAT Rule and/or Policy to tell CP to protect a group of IP addresses instead of a single IP? I've got a situation where my customer has multiple PIPs to protect, and I'd hate to create a NAT rule for each one.
I was thinking perhaps even connecting to Azure, then creating a NAT rule based on multiple Azure Objects/IPs?
Any insight is super appreciated ![]()
Cheers,
Oscar
Labels
- Labels:
-
Policy Installation
-
SmartConsole
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please elaborate with example of what you want to acheive
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I understand well, you would like to simply add more than one object on a NAT rule ?
If so, you've alright, we cannot do that; but: this object could be a group of objects... That's the solution I would propose.
BTW: that could be the What is your Check Point Idea of the Year? what do you think Dameon Welch Abernathy ? ![]()
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Xavier, any chance you can provide an example of group of Objects which represent Public IPs? The Original Services uses a Port, which is different for each IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Oscar, Vladimir Yakovlev proposed you what I thought ![]()
Regarding , you'll be able to look at available articles on Check Mates, like Video Link : 5568
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Xavier Bensemhoun . I have modified the #Ansible Playbook and running it on my local OS X. I already enabled the API via the Mangement Server and tested login via Postman, all works.
Now I am just overcoming running the Playbook locally on OS X as it wants to SSH into localhost, and I enabled SSH. But now get another error. Figuring out what that actually is now...
I've used Ansible before but never forced it to SSH to local machine but rather remote machines like Linux and Windows via WinRM as well.
fatal: [127.0.0.1]: FAILED! => {
"changed": false,
"module_stderr": "/bin/sh: [path: command not found\n",
"module_stdout": "",
"msg": "MODULE FAILURE",
"rc": 127
}
to retry, use: --limit @/Users/sharepointoscar/Downloads/check_point_mgmt_v1.0.1/plays/cpmanagement/checkpointmanagement.retry
____________
< PLAY RECAP >
------------
\ ^__^
\ (oo)\_______
(__)\ )\/\
||----w |
|| ||
127.0.0.1 : ok=0 changed=0 unreachable=0 failed=1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK ; so at this point, you should create another "question" article in Developers (Code Hub) section so that everyone involved on using Ansible will be able to help you ![]()
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Xavier Bensemhoun . I'll post on the other forum. I got past this issue, but have others....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You mean something like this:
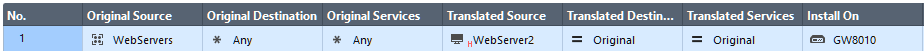
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
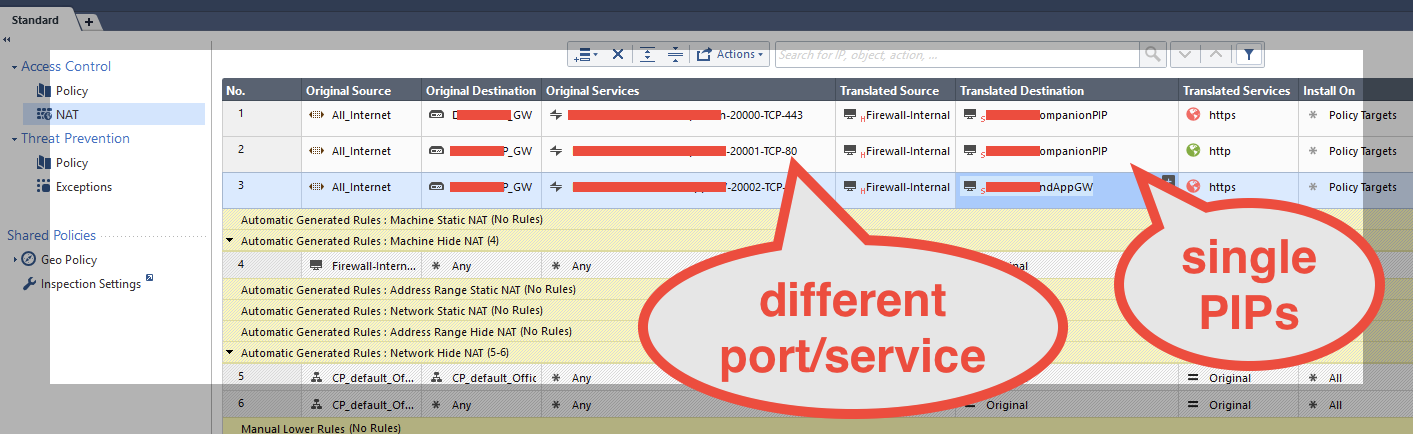
Thanks Vladimir - so here is a screenshot of my existing configuration. Basically I have about 80 more PIPs to protect, right now each line protects a PIP since we have different Service/Port for a given protocol.
I don't see how I can avoid using the Service/Protocol if I were to group the PIPs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK. Let's see if I understand your environment setup:
1. You are probably using your public DNS to translate URLs to the IP of the gateway with high ports.
2. Inbound traffic to the high ports hitting gateway is then NATed to the static private IPs with standard ports and forwarded to the servers.
If this is the case, you can implement another device between gateway and your servers that will perform NAT and PAT. Something like F5 will do the trick, I believe.
This should allow you to use single static destination in a single rule with "Original Services" containing a group comprised of all custom HTTP HTTPS services you have defined for your hosts and "Translated Services" remaining "Original".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Vladimir Yakovlev we did not want to add yet another device for this scenario, hence why it would not work for us.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're doing port translation for a specific destination IP, which will redirect to a different IP based on destination port.
Don't know of a way to do this without creating lots of rules, like you describe.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Dameon Welch Abernathy My next approach will be to use Ansible to create a batch of Hosts, Rules and publish them ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the challenge is to deliver on a server farm you can setup a logical server, it's not the most advanced but will allow you to add more than one server to receive the at the same destination port/service.
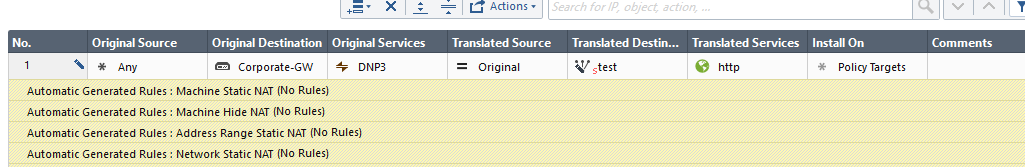
If it's just trying to map several services on a single public IP and deliverer it to it's own different IP, on a per service bases, then I think it might be like Dameon says. I do have a question though.
If the "world" is going for a high-port on the gw IP, why are you forcing the redirect to a standard port like http? Why don't you put the listening http at the same port you published to outside world?, by simply assuming you MUST redirect destination port you are narrowing down your options by your self:
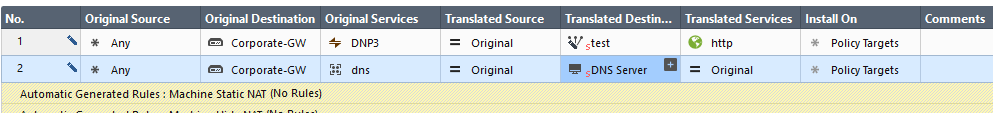
The above screenshot might has well be a group of high ports or what ever you need, just make the services on the server side match the original destination service and you are on with a bundle of ports in a single NAT rule.
Hope this helps
Carlos Santos
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 14 | |
| 13 | |
| 9 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


