This is not an official guide. This is just a tutorial from my lab.
It describes how Keycloak works as an Identity Provider for SmartConsole login using SAML. Btw: Mobile Access Login / VPN Login works the same way.
Starting with R81.20 Jumbo Take 89, you will need to modify the metadata file (step 6) as follows.
1. Version
Keycloak: 21.1.1
Check Point SmartCenter: R81.20
2. Select Realm in Keycloak

3. Create User
Create a User and assign a password (under credentials). Or use LDAP as a Source, etc.
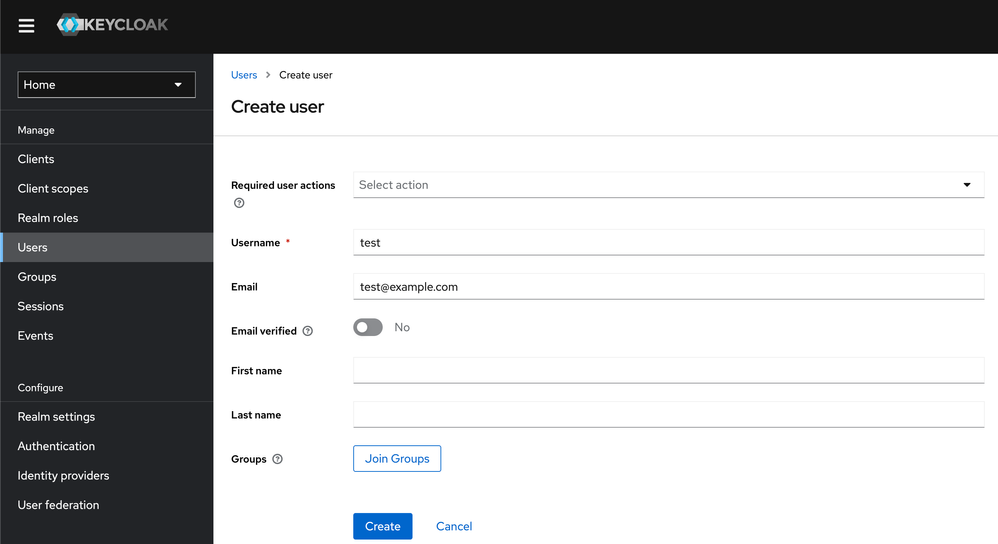
3.1 Set password
4. Client Scopes
The SmartConsole application integration in your Identity Provider must have attribute mappings for "username" and “groups”. In Keycloak this is done via “Client scopes”
Select “Client Scopes” and click “Create client scope”.
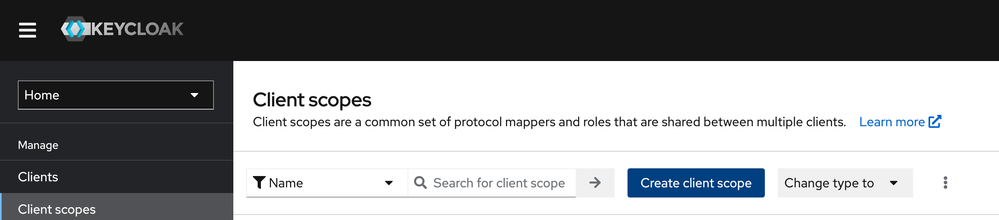
4.1 Create client scope “SmartConsole”
Name: SmartConsole
Protocol: SAML

5. Select the client scope “SmartConsole”

5.1 Click “Add mapper - by configuration” for username
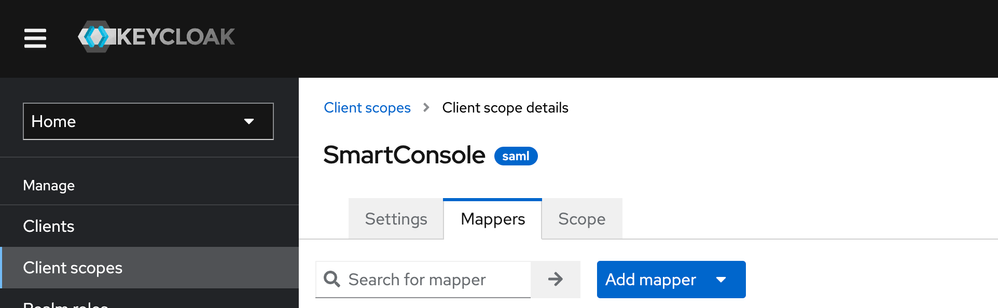
5.2 Select “User Attribute”
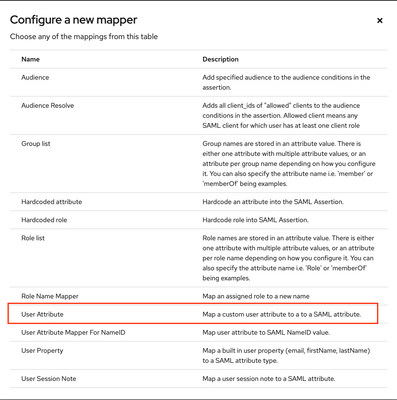
5.3 Enter “username” in the highlighted fields
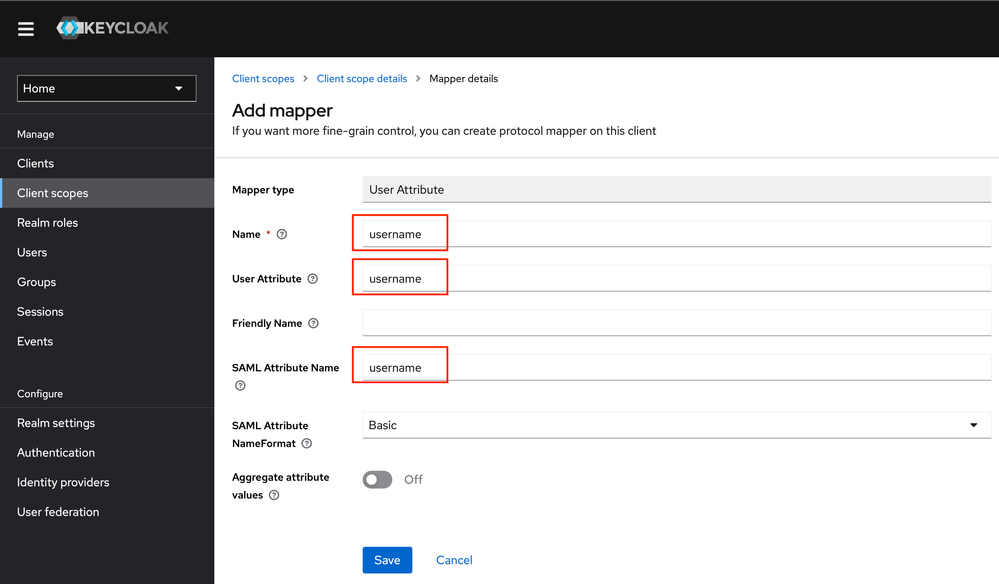
5.4 Click “Add mapper - by configuration ” for groups

5.5 Select Group List
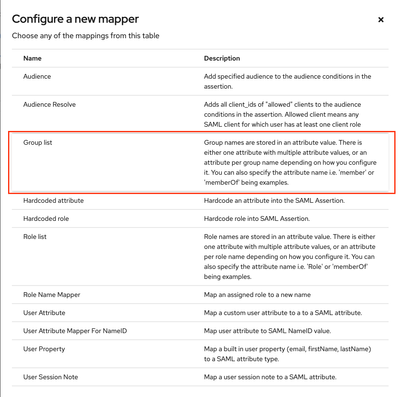
5.6 Enter “groups” in the highlighted fields
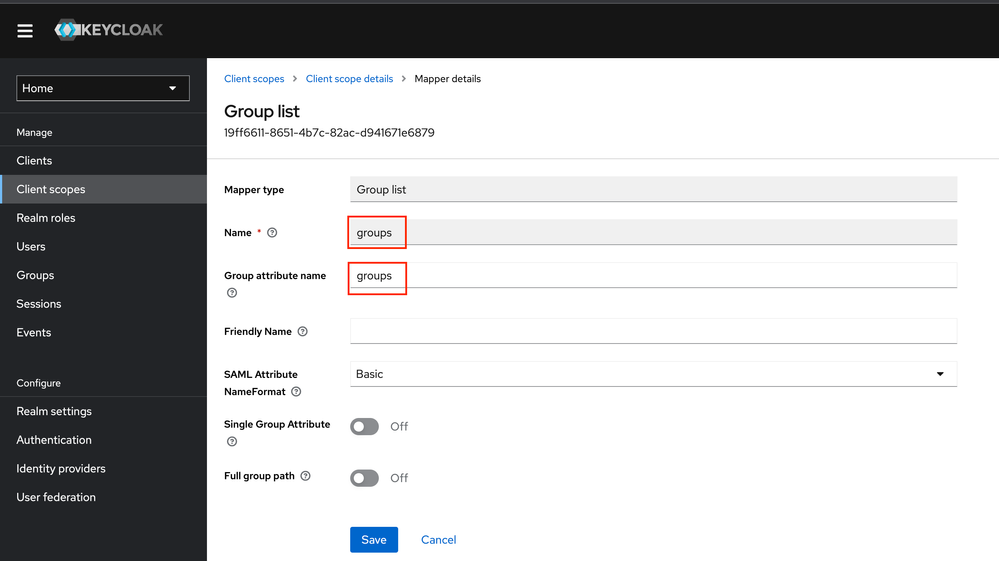
5.7 Client scope - Overview

6. Realm settings
Go to Realm settings and click on “SAML 2.0 Identity Provider Metadata” and save the XML File. This file is used in step 7.
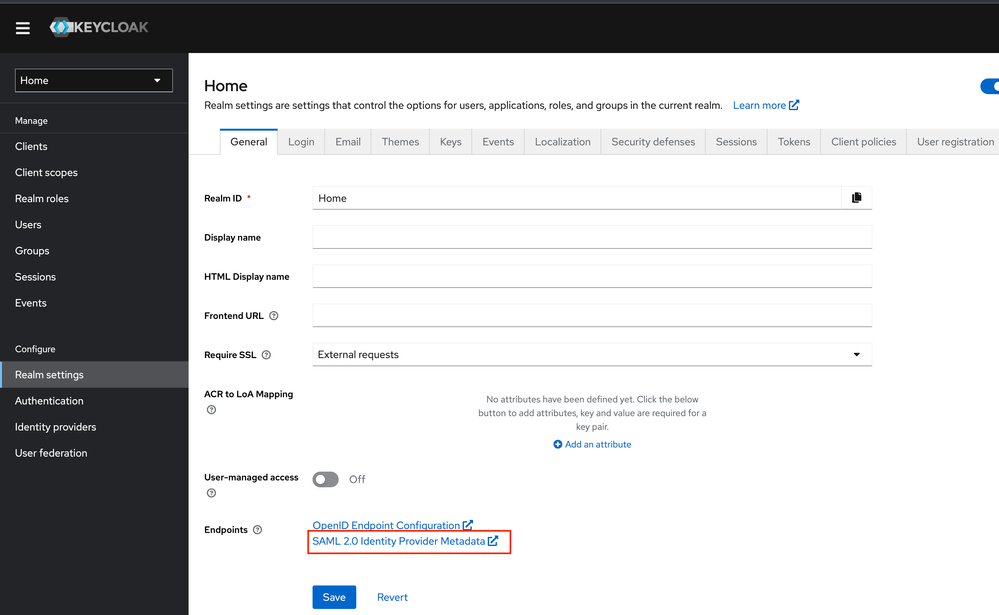
Starting from R81.20 Jumbo Take 89:
Open the metadata file (descriptor.xml) and modify the value "WantAuthnRequestsSigned" from "true" to "false".
7. Create Identity Provider Object
Create an Identity Provider Object in SmartConsole. Click “Import From File” and select the XML File from step 6. Publish the changes.
Copy the Identifier (Entity ID) and Reply URL in a text file.
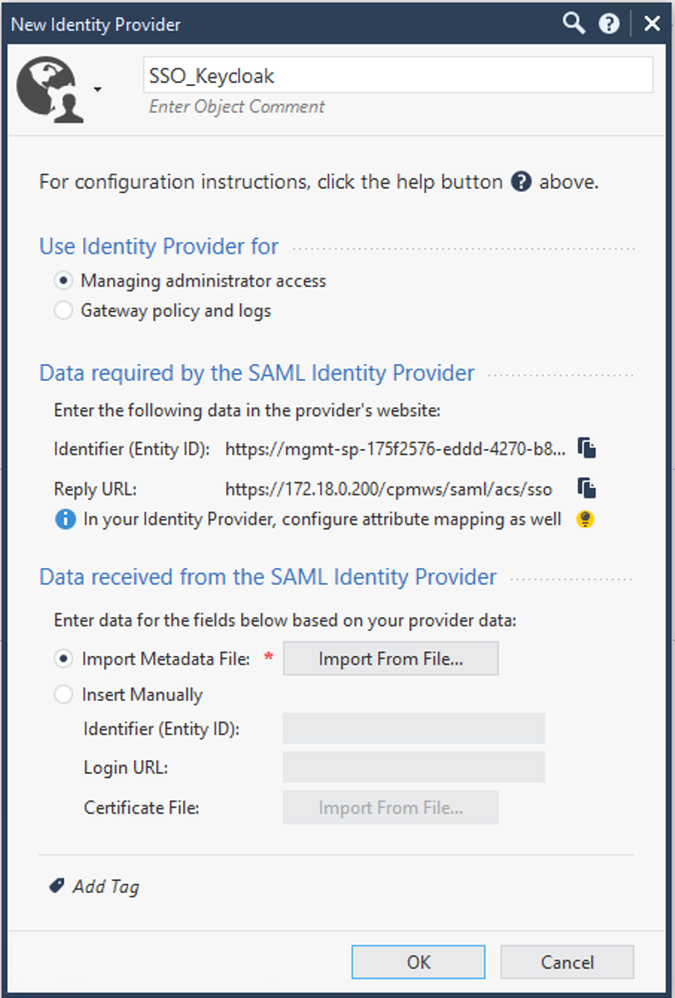
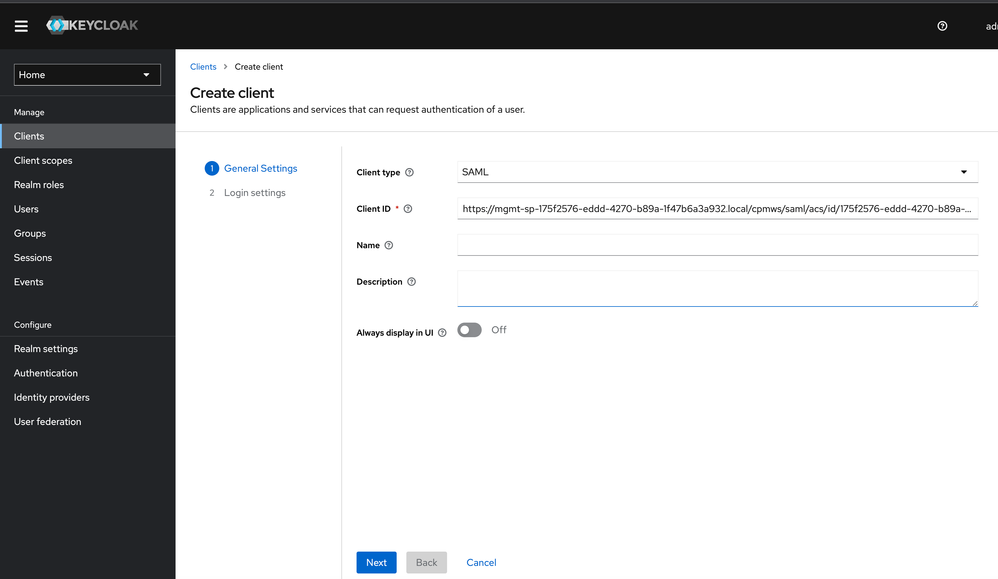
8. Clients
Click on Clients and select “Create Client”

8.1 SAML Client
Under “Client ID” enter the information from “Identifier (Entity ID)” (SmartConsole), from step 7.
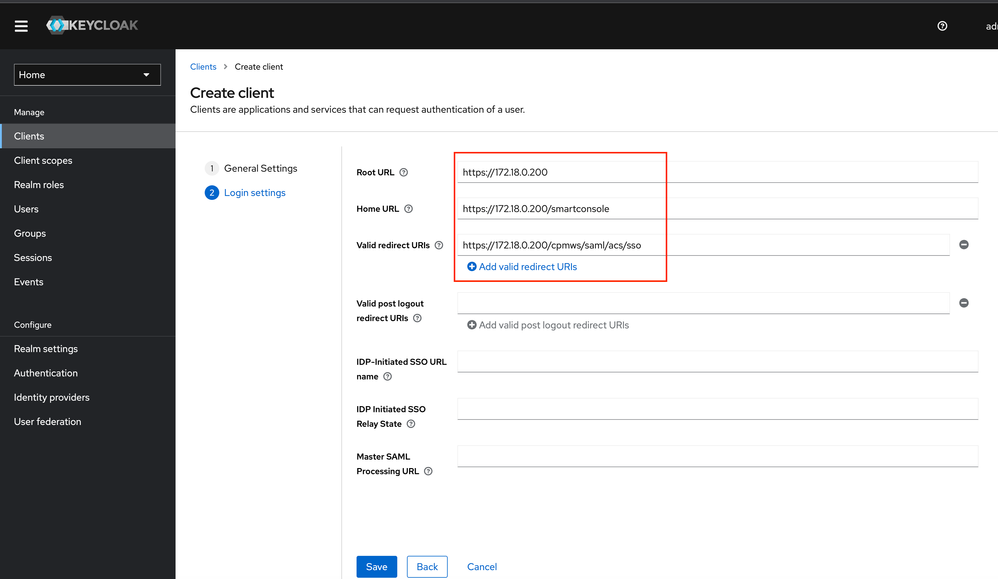
8.2 Login settings
Root URL and Home URL = IP Address from the SmartCenter
Under Valid redirect URIs enter the “Reply URL” from the Identity Provider Object (SmartConsole), see step 7.
8.3 Disable Client Signature
I don't know, if this can be configured at all with Check Point, so it must be disabled for it to work. Does anyone know if this can be enabled?

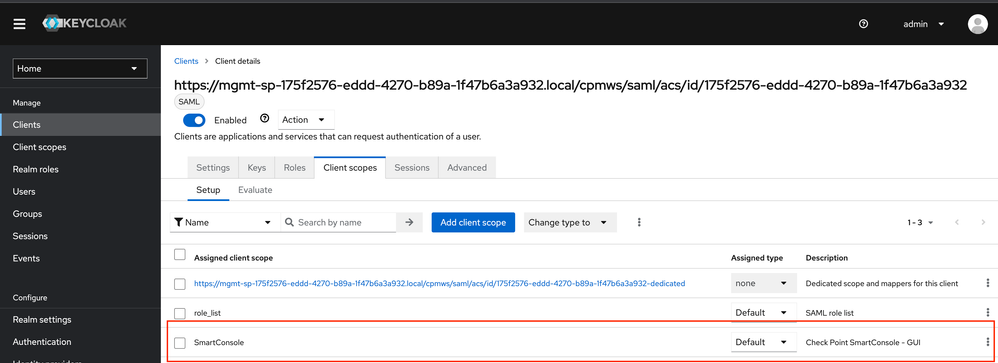
8.4 Client scopes
Check, if the client scope “SmartConsole” is assigned to the Client.
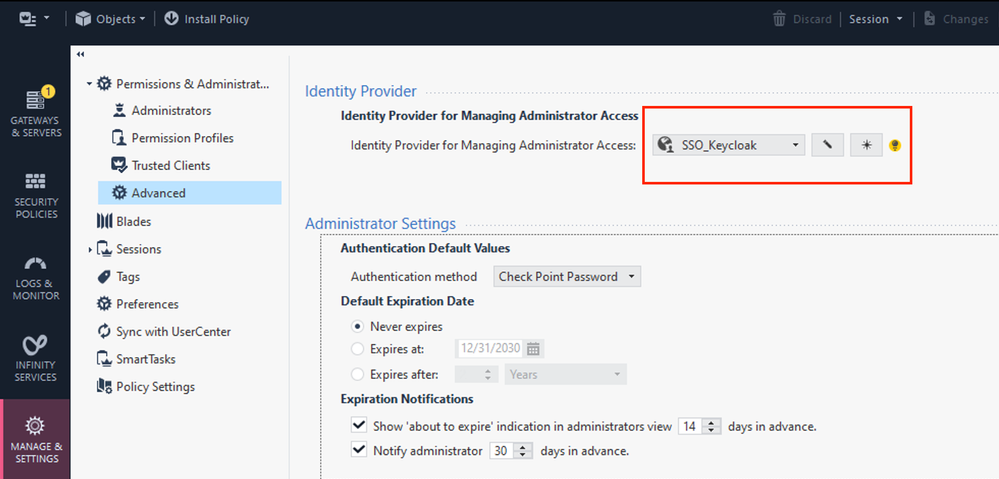
9. Select Identity Provider in SmartConsole
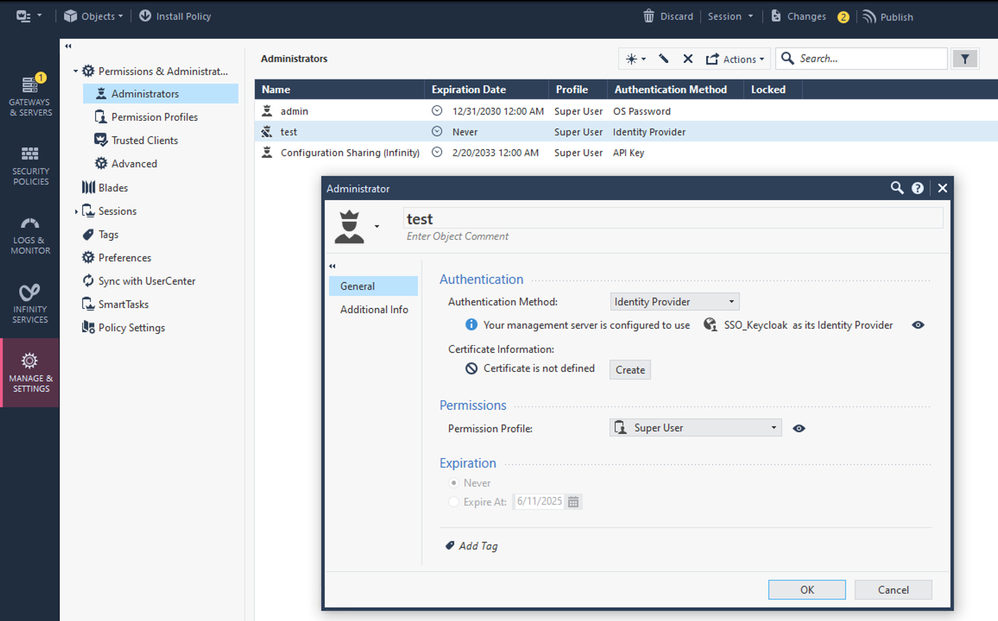
9.1 Create SmartConsole Admin
Create User, same Username as in Keycloak. Publish all changes.
9.2 Login SmartConsole
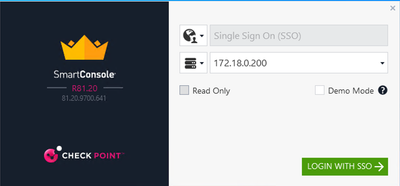
9.3 Redirect to Browser
Login using username “test".

9.4 Login successful
After successful login, SmartConsole opens.
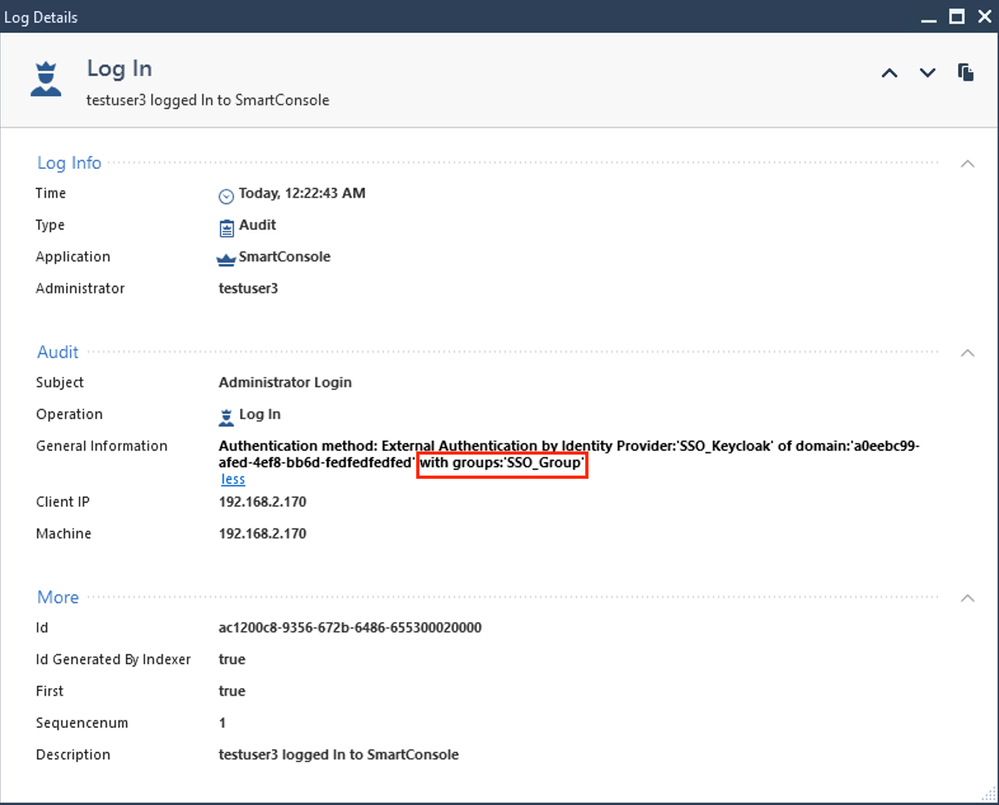
9.5 Logfile
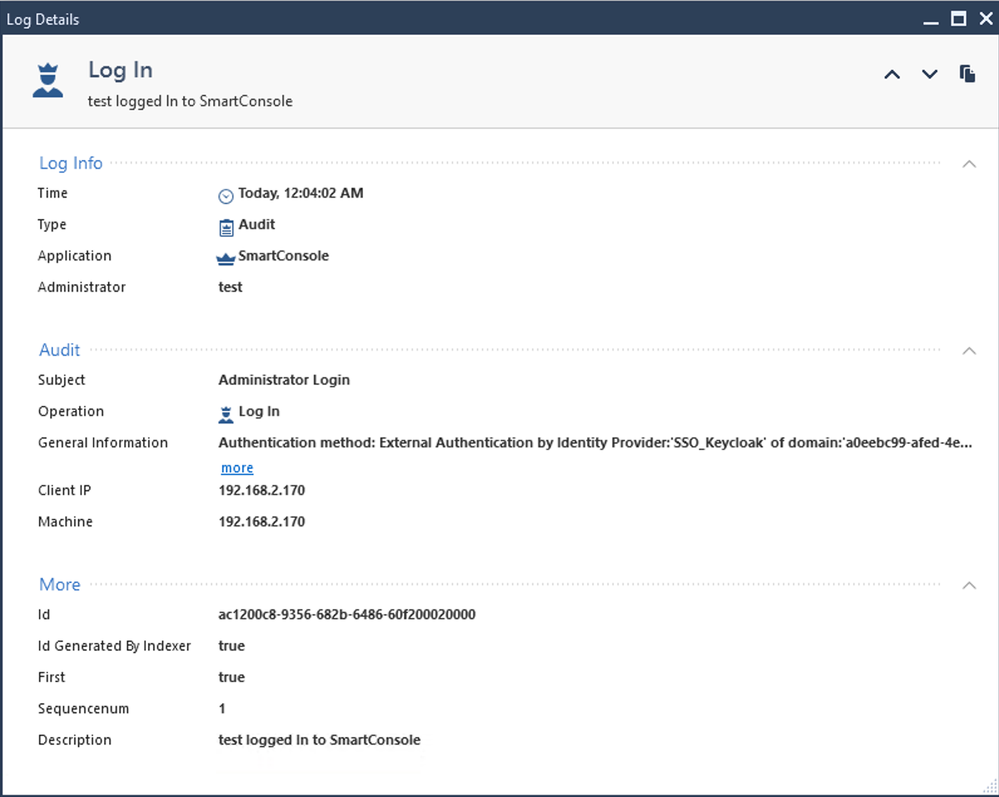
Login is also possible, using the Identity Provider for an Administrator Group. The Group Name must be the same on Check Point and on Keycloak. In this example, testuser3 is member of the group “SmartCenter-GUI” only.
10. Create "New Identity Provider Administrator Group
Group ID / Name: SmartCenter-GUI
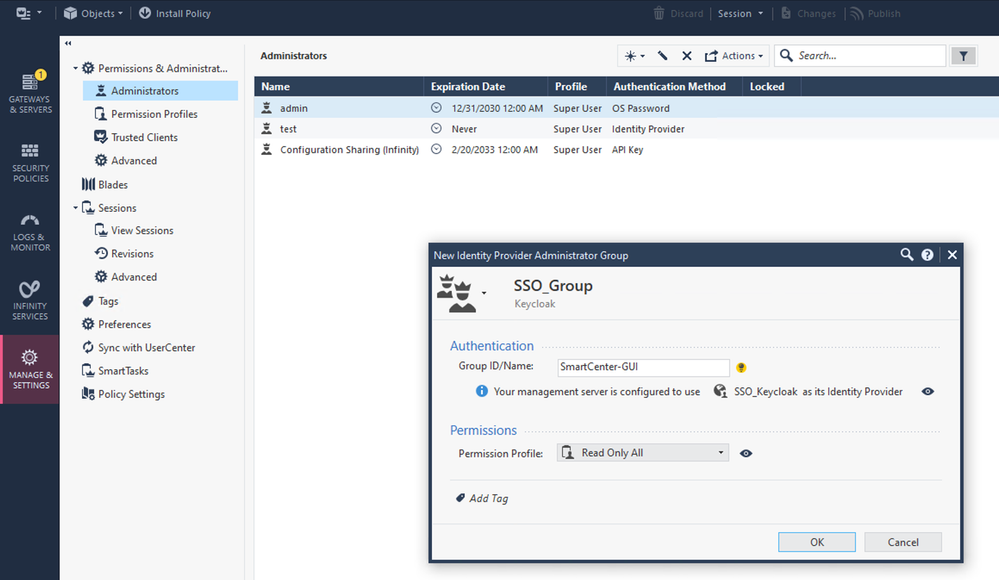
10.1 Overview
Object “SSO_Group” was created and all members in this group, are able to login to the SmartCenter.
10.2 Keycloak User Group
Create User Group “SmartCenter-GUI” in Keycloak and add a user to this group, in this example, “testuser3”

10.3 Login using testuser3