- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Is it possibly to bypass the Threat Prevention/Emu...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possibly to bypass the Threat Prevention/Emulation blade entirely via URL?
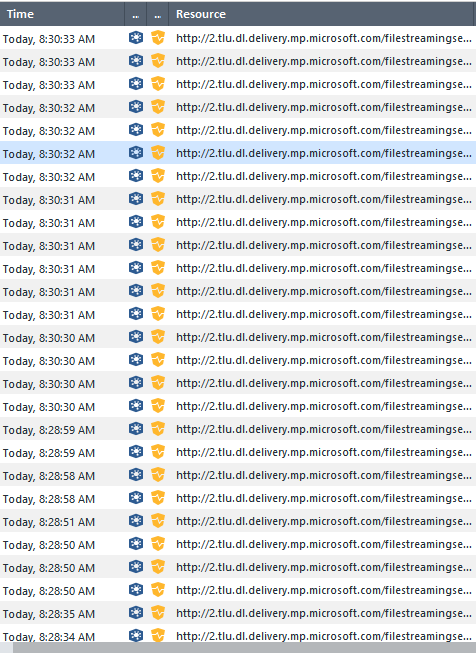
Lately my firewalls have been getting slammed with Threat Emulation tasks whenever a client reaches out to the Microsoft servers for windows update. It appears my clients are using HTTP to grab files from http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice and the download is causing TE to kick in and try to emulate the files, which causes increase load on the firewall. I know that I can create a Threat Prevention rule with all the Microsoft IPs/Networks as the Protected Scope and then assign a TP profile with TE/AV turned off, but I really don't want to have to maintain the list of Microsoft's IPs just to have it bypass TE when the URL is very clearly showing in the logs. It doesn't appear you can create a TP profile based on URL's, only scope. I just upgraded to R80.40 on one of my firewalls so I just tried using the new Updatable Objects as part of this. The docs for the updatable objects uses HTTPS inspection exceptions as the example, but I was presuming it could also be used in the Protect Scope column of a TP rule? I tried this, but it is skipping right over my TP rule with TE/AV disabled and is hitting the next rule where TE is still kicking in just like always.
Is there any other way to handle this? I thought I've seen references to a CSV file you can use with URL's loaded in it, but I'm not sure how to do that. I'll I'd really like to do is just bypass TP entirely on selective URL's/domains.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bump.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Rob_Bush !
Yes you can definitely use the Updateable Objects in the Threat Prevention policy as you intuitively understood - in the Protected Scope, Source or Dest columns. You can also use a custom URL exception.
To help you it'd be great if you can share a screenshot of the policy in question - and I'll help you configure it. You can also do that via a DM but I'd rather it be public so that others can enjoy the question&answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much for being willing to help!!
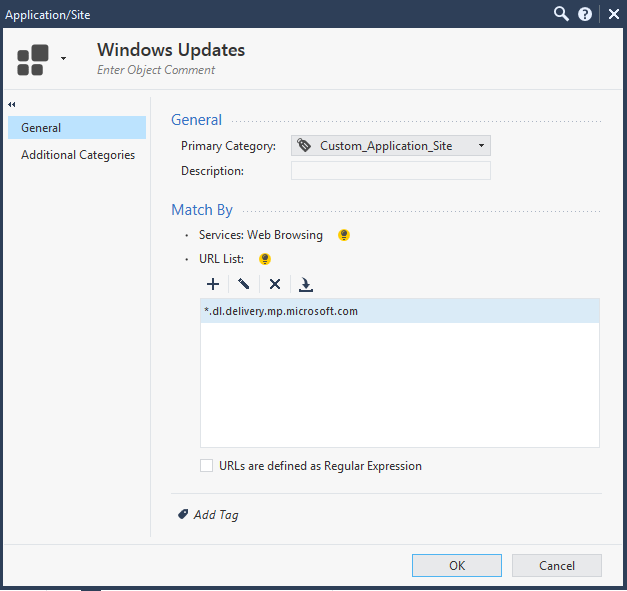
Attached is a screenshot of what I attempted. Unfortunately this Threat Prevention rule did not work as I still have TP being engaged on the Microsoft Update traffic (and just to be clear, I am also bypassing this same for HTTPS, but the TP is kicking in on non-HTTPS traffic to Microsoft update, which I'll include a screenshot of as well.)
The only thing I can think is that the "Microsoft - recommended HTTPS bypass" updatable object says it is grabbing all IP's related to "*.dl.delivery.mp.microsoft.com" and "*.delivery.mp.microsoft.com" (among the many url's) but this traffic that I'm seeing is "2.tlu.dl.delivery.mp.microsoft.com" so it's possible it's not matching because it's one level deeper ("tlu") than the deepest level shown on sk163595? I wasn't sure how the wildcard on the SK matched, and if would require the match to be to "*.tlu.dl.delivery.mp.microsoft.com" to work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@TP_Master - Bump.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Rob_Bush let's try another way.
Create a custom site with your site
Then add an exception using this newly created object
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to mention that in this case there is another, more performance oriented way and it is to use the so called "Null TP Profile". It is essentially profile with all TP blades deactivated and it is described with details in @Timothy_Hall's Max Power book which I highly recommend.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Creating an exception does not bypass the TP blades, it simply changes the final decision to Inactive or Detect. I suppose this approach could be construed as "bypassing" them since traffic matching the exception cannot be blocked, but that traffic still goes through all the relevant TP blades with the resulting overhead. As Hristo said a null TP profile is the best way to accomplish this.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks all.<br>
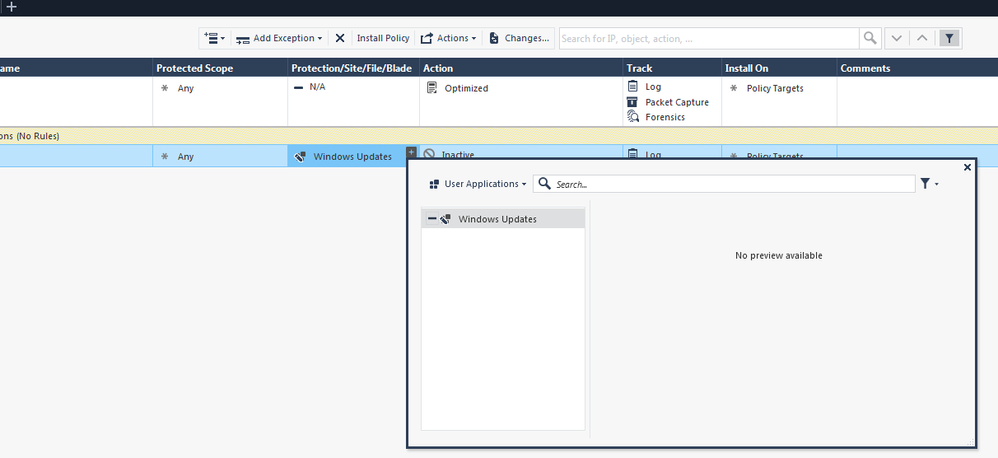
I'm not sure if you guys looked at the screenshots I put up? I think you'll see I'm attempting to use a Null profile with all blades turned off for the "Microsoft - recommended HTTPS bypass" updatable object. It is not working. (In my screenshot you'll see I named my null profile "Internal_All_Off".)<br>
I'm not trying to handle this via exceptions as I already know that exceptions serve a different purpose.<br>
I'm guessing you cannot use updatable objects in the "Protect Scope" column of TP profiles, otherwise this traffic would not be hitting the TP blades right now, and yet clearly it is. OR... as I wrote/questioned before...<br>
"The only thing I can think is that the "Microsoft - recommended HTTPS bypass" updatable object says it is grabbing all IP's related to "*.dl.delivery.mp.microsoft.com" and "*.delivery.mp.microsoft.com" (among the many url's) but this traffic that I'm seeing is "2.tlu.dl.delivery.mp.microsoft.com" so it's possible it's not matching because it's one level deeper ("tlu") than the deepest level shown on sk163595? I wasn't sure how the wildcard on the SK matched, and if would require the match to be to "*.tlu.dl.delivery.mp.microsoft.com" to work?"<br>
I don't have access to a good lab environment to test this out. Is there any chance anyone could try the same in a lab environment and tell me if you get it to work when using updatable objects? It doesn't even have to be the "Microsoft - recommended HTTPS bypass" updatable object, any one of the updatable objects will work just to prove it out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ever got this to work ? it is still doing on 81.10... VERY annoying
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm curious too if you got this to work. I'd still like TP to work but to create exceptions for Microsoft.
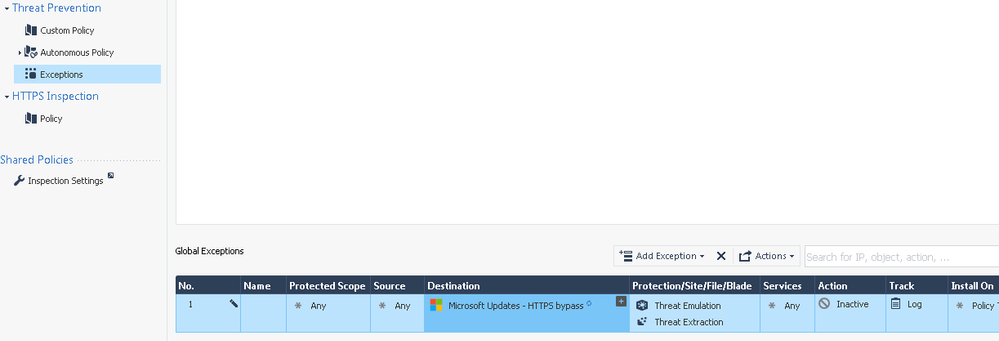
I'm getting a lot of logs for cab files to microsoft.com even though we've added a an Global exception.
I'm not using a Null profile though, since I don't want the server to completely bypass TP blade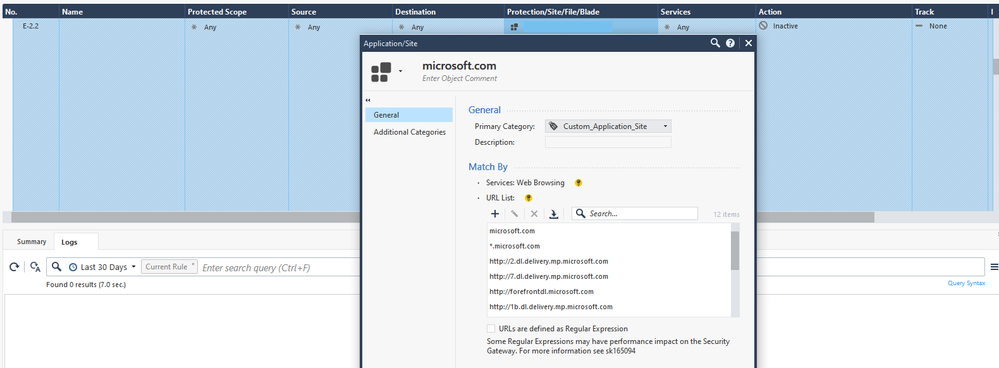
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You just don't want to see the logs or there is another reason for the exception?
The verdict returned in those logs is "trusted source" or "file size exceeded" ...
Refer also:
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
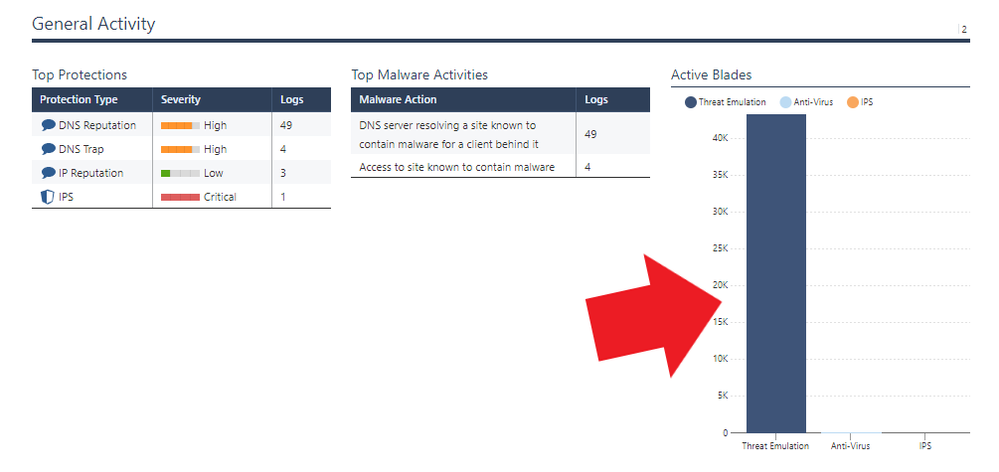
I guess it's annoying me again because I looked at the Threat Prevention reports and was wondering why the amount of the logs is extremely high due to the Threat Emulation. I'll take a look at those threads/SKs again. Apparently, I've been on that thread too due to this activity. 😅
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Understood, maybe there is a case for an RFE please raise it with your local SE.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tagging @Rob_Bush @FrankK @TP_Master
The following blade-based global exception should do what you want. Unlike a protections-based exception which only changes the final verdict (Prevent/Detect) but still performs the full deep inspection, a blade-based exception with an Action of Inactive completely skips processing the matching traffic for the configured TP blades, thus saving large amounts of overhead.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter