- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Install policy failure: Reason Crypt.def
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Install policy failure: Reason Crypt.def
Hi all,
System:
- R81 take 42
- Platform: ST-4150-00
- Model: Smart-1 5150
- dir: /opt/CPsuite-R81/fw1/lib
This is a huge enviroment and I'm facing this issue since 2 days. We edited the file crypt.def Jan/16, but all the policies was intalling normally. The only difference between the crypt.def Jan/16 and crypt.def before Jan/16 it is one dst I added to the file.
As I said I did a lot policy install to several SG, VSX and NON-VSX. Now SMS is not able to install for both enviroments VSX and NON-VSX.
I follow this sk139174 but still getting same error when installing policy.
Also the SK suggest to run:
# update_inspect_files -f
Environment is invalid.
I returned the orignal crypt.def before Jan/16 and also get same error. Also I put here both crypt.def
SMS r81
here is the 1st policy installation failed:
Tks,
Victor C
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The solution was fix a incorrect configuration about networks on user.def
After I fixed user.def all the policy installations works as expected.
Tks,
Victor C
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does issue occur if you copy back original crypt.def file?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
He wrote above: I returned the orignal crypt.def before Jan/16 and also get same error.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, yes, you are right, I was not sure if thats what that meant. Good suggestion though in your other response, lets see if that helps.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
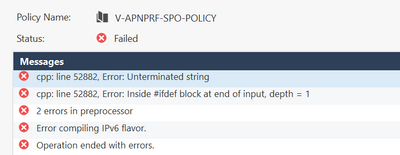
Look at the first error:
cpp Line 387, Error: Redefining variable "NON_VPN_TRAFFIC_RULES"
This is line 387 from crypt.def:
#define NON_VPN_TRAFFIC_RULES ((src=191.19.253.171...
You define for IPv4, but we see:
Error compiling IPv6 flavor
I can see in sk108357 that #ifndef NON_VPN_TRAFFIC_RULES is left out - maybe try that format ? Could be worth the test.
To exclude only IPv4 address:
change from old version
#ifndef NON_VPN_TRAFFIC_RULES #define NON_VPN_TRAFFIC_RULES 0 #endif
to
#ifndef IPV6_FLAVOR #define NON_VPN_TRAFFIC_RULES (dst=Destination_IPv4_Address,dport=Destination_Port) #else #define NON_VPN_TRAFFIC_RULES 0 #endif
Rather looks like something for TAC...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I changed crypt.def to this:
#ifndef IPV6_FLAVOR
#define NON_VPN_TRAFFIC_RULES ((src=191.19.253.171 and dst=167.114.76.96) or (src=167.114.76.96 and dst=191.19.253.171) or dst=191.8.179.132 or dst=3.12.63.214 or dst=40.84.128.42 or src=191.19.253.71 or dst=74.208.159.136 or dst=200.243.224.147 or dst=200.229.193.242 or dst=142.40.176.180 or dst=200.186.114.181 or dst=187.33.8.10 or dst=200.186.114.173 or dst=54.227.72.56 or dst=54.165.35.50 or dst=104.196.118.88 or dst=201.131.209.10 or dst=167.114.76.96)
#else
#define NON_VPN_TRAFFIC_RULES 0
#endif
and did push policy:
Do you guys have any idea?
Tks,
Victor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
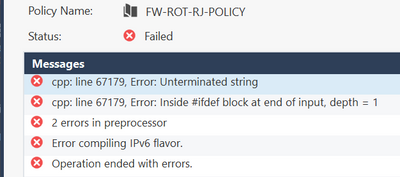
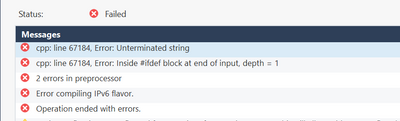
Hey Victor,
Does not like something with line 67184. Can you copy that line here, so we can have a look?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is all the lines. Doesnt exist line 67184.
#ifndef __crypt_def__
#define __crypt_def__
//
// (c) Copyright 1993-2005 Check Point Software Technologies Ltd.
// All rights reserved.
//
// This is proprietary information of Check Point Software Technologies
// Ltd., which is provided for informational purposes only and for use
// solely in conjunction with the authorized use of Check Point Software
// Technologies Ltd. products. The viewing and use of this information is
// subject, to the extent appropriate, to the terms and conditions of the
// license agreement that authorizes the use of the relevant product.
//
// $RCSfile: crypt.def,v $ $Revision: 1.12.44.16 $ $Date: 2002/07/16 13:51:00 $
//
#include "vpn_formats.def"
#include "vpn_table.def"
#define accept_fwz_as_clear(type) \
( \
(call KFUNC_ACCEPT_FWZ_CLEAR<>) or 1 \
)
#define VPN_ACTIVE(rule) \
( (<1> in vpn_active) or \
(LOG(long, LOG_NOALERT, rule), reject) )
/*
* Will be used in filter.cc before calling ENCRYPTION,
* only if rule supports ippools
*/
deffunc APPLY_IP_POOL(rule) {
set sr2 call KFUNC_APPLY_IP_POOL<>,
sr2
or
drop
};
#define IPPOOLS_ENCRYPTION(rule) \
( \
APPLY_IP_POOL(rule), \
ENCRYPTION(rule) \
)
#define IPPOOLS_ENCRYPTION_WITH_SCV(rule) \
( \
APPLY_IP_POOL(rule), \
ENCRYPTION_WITH_SCV(rule) \
)
/*
* As far as INSPECT is concerened, encrypting a connection
* is writing it to the connection table with CONN_ENC_NO_ENTRY
*/
deffunc ENCRYPTION_EX(rule,flags) {
(
VPN_ACTIVE(rule),
set r_entry CHANGE_TYPE(r_entry,CONN_ENC_NO_ENTRY),
RECORD_CONN_EX(rule, r_entry, flags)
)
};
#define ENCRYPTION(rule) \
( \
ENCRYPTION_EX(rule, 0) \
)
/*
* r_scvres holds the results of the SCV check.
*/
#define ENCRYPTION_WITH_SCV(rule) \
( \
( r_scvres = SCV_PENDING_VERIFICATION, \
ENCRYPTION_EX(rule, NEEDS_SCV) ) \
or \
( ( (r_scvres = SCV_VERIFIED) or (r_scvres = SCV_DONT_VERIFY) ), \
ENCRYPTION_EX(rule, 0) ) \
)
#define COMMUNITY_ENCRYPT(COMMUNITY_TABLE_NAME,COMMUNITY_NUMBER,SRCIP) \
( \
SRCIP in COMMUNITY_TABLE_NAME, dst in COMMUNITY_TABLE_NAME, \
(call KFUNC_SET_VPN_COMMUNITY_ID<COMMUNITY_NUMBER> or drop) \
)
#define COMMUNITY_NEED_TO_SET(id) \
( \
id != COMM_MY_ENC_DOAMIN, \
(id = COMM_NOT_IN_ANY_COMMUNITY) or (call KFUNC_SET_VPN_COMMUNITY_ID<id>) \
)
#define SET_VPN_COMMUNITY_IDS(id_client, id_server) \
( \
set r_community_left 0, \
((id_client!=COMM_MY_ENC_DOAMIN), \
set r_client_community id_client, \
set r_community_left (r_community_left +1), 0) \
or \
((id_server!=COMM_MY_ENC_DOAMIN), \
set r_server_community id_server, \
set r_community_left (r_community_left +1), 0) \
or 1 \
)
/*
* this macro is true if there is no gw2gw community.
* It used to prevent SR tagging in case that there is a commuity
*/
#ifdef VPN_COMMUNITY_DEFINED
#define NO_GW2GW_COMMUNITY(id) ( not ( (id),(id!=COMM_NOT_IN_ANY_COMMUNITY) ) )
#else
#define NO_GW2GW_COMMUNITY(id) (1)
#endif
/*
* How we classify simultaneous SR connection/site-to-site
* If NO_SR_IN_PEER_DOMAIN is true, we tag those connections as GW2GW and the use
* of the NO_GW2GW_COMMUNITY will prevent them from being tagged as SR community
* If NO_SR_IN_PEER_DOMAIN is false, we won't tag them as GW2GW if they look like
* they are SR connection so they won't pass the policy on GW rules and the
* NO_GW2GW_COMMUNITY won't stop them from being tagged as SR
*/
#ifdef NO_SR_IN_PEER_DOMAIN
#define ALLOW_GW_TAG_FOR_SR(addr) 1
#else
#define ALLOW_GW_TAG_FOR_SR(addr) (not (addr in userc_users))
#endif
#define GET_CLIENT_COMM \
( \
ALLOW_GW_TAG_FOR_SR(src), \
( (get <src> from local_vpn_routing to sr2) or \
/* handle DAG address sr1 = IP to look in routing table*/ \
(( (get <src> from DAG_IP_to_ID to sr1) or \
(get <src> from my_daip_ip_to_id to sr1) or \
(get <src> from Robo_ranges to sr1, set sr1 sr2) or (set sr1 src)),\
/* sr1 = source community ID (4th value in table) */ \
(get <sr1> from vpn_routing to sr2 or set sr5 COMM_NOT_IN_ANY_COMMUNITY))\
),\
set sr1 sr5 \
)
#define GET_SERVER_COMM \
( \
ALLOW_GW_TAG_FOR_SR(dst), \
/* sr6 = dest community ID */ \
(get <dst> from local_vpn_routing to sr3) or \
((set sr2 call KFUNC_GET_DST_POOLED_IP<dst>, sr2) or \
(get <dst> from DAG_IP_to_ID to sr2) or \
(get <dst> from Robo_ranges to sr2, set sr2 sr3) or \
(get <dst> from my_daip_ip_to_id to sr2) \
or (set sr2 dst), \
get <sr2> from vpn_routing to sr3 or \
set sr6 COMM_NOT_IN_ANY_COMMUNITY) \
)
#define IS_COMMUNITY_CONN \
( \
<1> in vpn_active, \
GET_CLIENT_COMM, /*sr1 client comm id */ \
(( \
(sr1 != COMM_NOT_IN_ANY_COMMUNITY, (sr4 & DEFAULT_ROUTER_FLAG)), \
/* if we are the default router for the source, */ \
/* do not require the server side to be in a community */ \
GET_SERVER_COMM /*sr6 server comm id */ \
) or ( \
GET_SERVER_COMM, /*sr6 server comm id */ \
/* if the destination is for a gateway for which we are default */ \
/* router, do not require the client side to be in a community */ \
( sr6 != COMM_NOT_IN_ANY_COMMUNITY, \
(sr1 != COMM_NOT_IN_ANY_COMMUNITY or (sr5 & DEFAULT_ROUTER_FLAG)) \
) \
)), \
( sr1 != COMM_MY_ENC_DOAMIN or sr6 != COMM_MY_ENC_DOAMIN) \
)
#define COMMUNITIES_TAG \
all@all drop \
( \
SET_VPN_COMMUNITY_IDS(r_ro_client_community,r_ro_server_community), \
0);
#define get_community_ \
( \
IS_COMMUNITY_CONN, \
(sr1 != COMM_NOT_IN_ANY_COMMUNITY, \
COMMUNITY_NEED_TO_SET(sr1), set r_client_community sr1, 0) or \
(sr6 != COMM_NOT_IN_ANY_COMMUNITY, \
COMMUNITY_NEED_TO_SET(sr6), set r_server_community sr6) \
)
#ifndef NAT_TRAVERSAL_PORT
#define NAT_TRAVERSAL_PORT 4500
#endif
#ifndef DPORT_IS_IKE
#define DPORT_IS_IKE ((dport = ISAKMPD_DPORT) or (dport = NAT_TRAVERSAL_PORT))
#define SPORT_IS_IKE ((sport = ISAKMPD_DPORT) or (sport = NAT_TRAVERSAL_PORT))
#endif
/*
* USER_CHECK_CONNECTION:
* This function calls KFUNC_CHECK_SR_USER which is responsible for:
* 1. Encryption domain enforcment.
* 2. User destination restriction enforcement.
* 3. IP pool allocation (and logging thereof).
* If KFUNC_CHECK_SR_USER returns 1 then the connection should be d/encrypted
* and so we write the connection to the connection table with the CONN_ENC_NO_ENTRY_SR.
* If KFUNC_CHECK_SR_USER returns 0 then the connection needs to go thorough
* Otherwise, we drop the connection.
*/
deffunc USER_CHECK_CONNECTION(rule, is_decrypt, intersect) {
( set sr2 call KFUNC_CHECK_SR_USER <rule, is_decrypt, intersect; origdst>,
sr2,
(
VPN_ACTIVE(rule),
sr2 = 1
#if !defined ( VPN_COMMUNITY_DEFINED)
,set r_entry CHANGE_TYPE(r_entry,CONN_ENC_NO_ENTRY_SR)
#endif
)
or
drop
)
};
deffunc USER_PASS_CONNECTION(rule) {
(
set r_mflags (r_mflags | MFLAGS_SRC_MATCHED_SC_RULE),
RECORD_CONN_EX(rule, r_entry, 0)
or
drop
)
};
/*
* r_scvres holds the results of the SCV check.
*/
deffunc USER_PASS_CONNECTION_SCV(rule) {
(
(
( r_scvres = SCV_PENDING_VERIFICATION, RECORD_CONN_EX(rule, r_entry, NEEDS_SCV) )
or
( ( (r_scvres = SCV_VERIFIED) or (r_scvres = SCV_DONT_VERIFY) ),
set r_mflags (r_mflags | MFLAGS_SRC_MATCHED_SC_RULE),
RECORD_CONN_EX(rule, r_entry, 0) )
)
or
drop
)
};
/*
* User client encryption (SecuRemote) macro (server side):
* --------------------------------------------------------
* The user should first successfully pass the key exchange protocol, and as
* a result his IP address will be placed in userc_rules (<src,rule>).
*
* The first packet from the user will be intercepted by this rule and if the
* source and this rule (<src,rule>) or the destination (<dst,0>) are in
* userc_rules, then this connection will be checked to see if it
* is from/to the encryption domain and that the connection adhere to the user's
* destination restrictions.
*/
define USER_ENCRYPT_CONN_CHECK(rule) {
( USER_CHECK_CONNECTION(rule, 0, 0)
)
};
define USER_DECRYPT_CONN_CHECK(rule, intersect) {
( USER_CHECK_CONNECTION(rule, 1, intersect)
)
};
#define IS_MY_ACCEPT_ALL_ENCRYPTED \
( \
set sr1 call KFUNC_IS_MY_ACCEPT_ALL_ENCRYPTED <r_ro_client_community, r_ro_server_community>, \
sr1 \
)
/* COMMUNITIES_RULEMATCH: look in vpn_rulematch table for an entry consists of <rule number, client (src) community,
server (dst) community > exists.
this procedure is only relevant for simplified mode.
*/
deffunc VPN_RULEMATCH(rule) {
(
set sr1 call KFUNC_DO_VPN_RULE_MATCH <rule, r_ro_client_community, r_ro_server_community, r_client_ifs_grp,r_server_ifs_grp, 10>,
sr1
)
};
deffunc USER_CLIENT_ENCRYPTION_CHECK(rule) {
(
(
(NO_GW2GW_COMMUNITY(r_client_community)),
(<src> in userc_rules, USER_DECRYPT_CONN_CHECK(rule,rule)) /*intersect for non-implied rules*/
)
)
};
/*
* USERC_DECRYPT_SRC checks whether the connection should be decrypted.
* The services appearing should not be decrypted even if the source
* is a client that has exchanged keys with the gateway and the
* destination is in the encryption domain.
* The following macro should be the 'not' of the accept_without_encryption
* macro defined in clcrypt.def.
*/
define USERC_DECRYPT_SRC {
(
#ifndef ENCDNS
not(dport = SERV_domain, (udp or tcp)),
#endif
#ifdef SECUREMOTE
not(<ip_p,dport> in userc_noncrypt_ports),
#else
not(dport = FWD_TOPO_PORT, tcp),
not(dport = FWD_SVC_PORT, tcp),
not((inbound, DPORT_IS_IKE) or (outbound, SPORT_IS_IKE), udp or tcp),
not(dport = FW_ICA_SERVICES_PORT, tcp),
not(_fwz_encapsulation),
not(_esp),
not(_ah),
#endif
not(dport = RDPPORT, udp),
not(sport = RDPPORT, udp)
)
};
#define DST_IS_POOLED_SR \
( \
call KFUNC_POOLED_IP_IS_SR<;dst,src> , \
USER_ENCRYPT_CONN_CHECK(rule) \
)
deffunc ACCEPT_CLIENT_ENCRYPTION_CHECK(rule) {
(
USERC_DECRYPT_SRC,
#if defined (VPN_COMMUNITY_DEFINED)
(
(r_ro_src_sr, USER_DECRYPT_CONN_CHECK(rule,0))
or
(r_ro_dst_sr, USER_ENCRYPT_CONN_CHECK(rule))
)
#else
( /* traditional */
(
(NO_GW2GW_COMMUNITY(r_client_community), <src> in userc_users, USER_DECRYPT_CONN_CHECK(rule,0))
or
(NO_GW2GW_COMMUNITY(r_server_community), <dst> in userc_users, USER_ENCRYPT_CONN_CHECK(rule))
)
or
(DST_IS_POOLED_SR)
)
#endif
)
};
/*
* USERC_CHECK checks whether the connection may match the client encryption
* rule. This macro does not perform any action. It is assumed that this
* macro appears in rules where trapping to the daemon and
* encryption/decryption will be handled by other macros (such as rules
* with resources)
*/
define USERC_CHECK(rule) {
(<src> in userc_rules)
};
#ifndef IPV6_FLAVOR
#define NON_VPN_TRAFFIC_RULES ((src=191.19.253.171 and dst=167.114.76.96) or (src=167.114.76.96 and dst=191.19.253.171) or dst=191.8.179.132 or dst=3.12.63.214 or dst=40.84.128.42 or src=191.19.253.71 or dst=74.208.159.136 or dst=200.243.224.147 or dst=200.229.193.242 or dst=142.40.176.180 or dst=200.186.114.181 or dst=187.33.8.10 or dst=200.186.114.173 or dst=54.227.72.56 or dst=54.165.35.50 or dst=104.196.118.88 or dst=201.131.209.10 or dst=167.114.76.96)
#else
#define NON_VPN_TRAFFIC_RULES 0
#endif
#endif /* __crypt_def__ */
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would say contact TAC and let them fix it, might be much easier over zoom meeting. By the way, I remember ages ago, customer had to do triple brackets at the beginning and end of that line, so ((( and )))
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please delete these lines, they do not help ! The file with wrong line 67184 is FW-ROT_SP_POLICY.pf that calls fwui_head.def that calles base.def that calls crypt.def and hereby fails.
Contact TAC !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The solution was fix a incorrect configuration about networks on user.def
After I fixed user.def all the policy installations works as expected.
Tks,
Victor C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would you mind sharing exactly what you did?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any sort of corruption or syntax error in user.def would cause the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I specified a invalid network on user.def. It was just one wrong digit.
sk30919
Tks,
Victor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it!
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter