- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Import a list of certificates!
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Import a list of certificates!
Is there any option to update all the trusted CAs list?
Where can I find the complete packet of trusted CAs to download?
Is there any option to import my own list?
Thank you
Labels
- Labels:
-
Policy Installation
-
SmartConsole
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The list of CAs is updated regularly.
You can export a single CA (not the whole list), but you can see the whole list.
You can also import a single CA (you have to repeat this step multiple times):
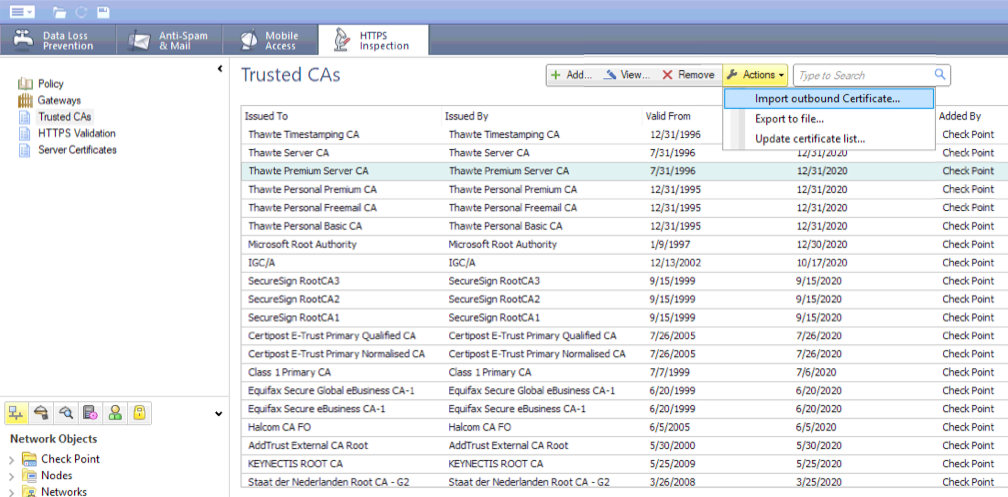
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The list of CAs is updated regularly.
You can export a single CA (not the whole list), but you can see the whole list.
You can also import a single CA (you have to repeat this step multiple times):

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see, my problem is from time to time we have to import all the governamental certificates and they are more than 100, so it's time-wasting to import one by one.
Should be a nice feature to import many at the same time.
Thank you Dameon!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, there isn't an out-of-the-box solution for this at the moment. We will consider this request in our next releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response Tomer Sole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One of my customers needs to import a new Trusted Root as several sites are having issues with the fact this is not recognized by Check Point. Dameon Welch-Abernathy you saying that for this we should be using "Import outbound Certificate" as this looks more like the the one used for HTTPS Inspection and not Trusted CA i'm looking for. The only other option is to update the whole list with a zip of "unknown" contents with "unknown format" as per sk64521.
According to sk122973 we could easily solve this issue by importing the Root CA of Digicert Inc. however this SK is inaccurate for 80.20. There is no such thing as 'SmartConsole > HTTPS Inspection > Advanced > Trusted CA > Import' . However looking at how SmartConsole looks in R80 (using the traditional console app for HTTPS Inspection) there is no such menu:
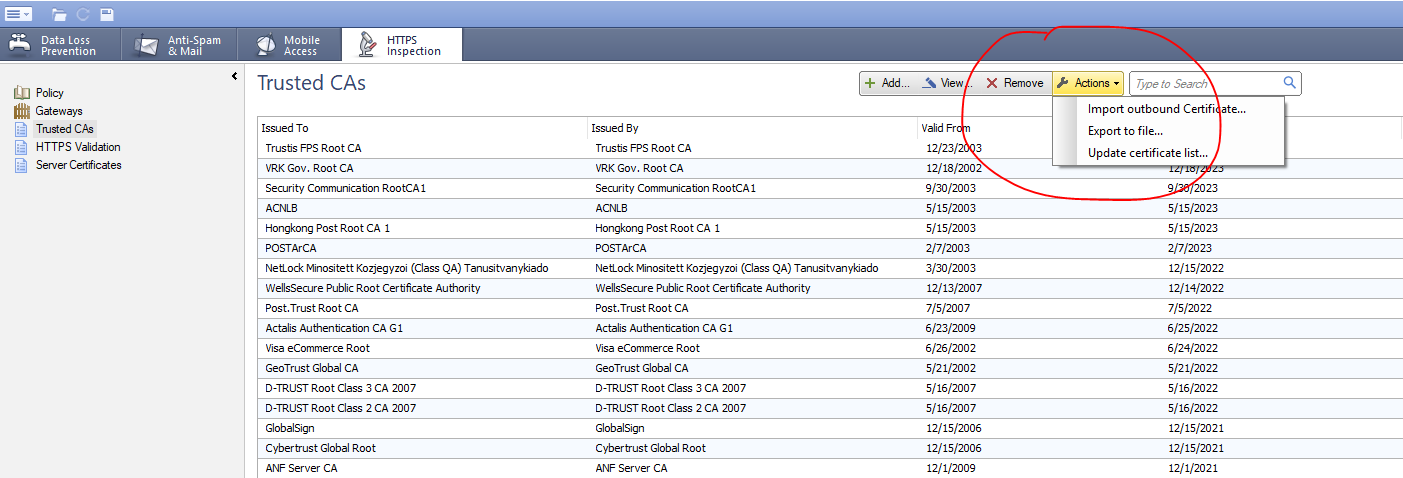
Regardless i've put 1-2 stars and Feedback on both SKs and waiting for updates. Check Point actually takes things into consideration and updates them when they get bad feedback.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Cezar,
The sk64521 is to update the list of certificates provided by CheckPoint and it's a ZIP file that CheckPoint TAC can provide you if you open a Ticket.
As per sk122973 the SK says the problem is only for 77.30 and 80.10, for other versions above r80.10 take 112 it seems to not have ever being seen.
If you are experienciend such a problem with those websites mentioned in the SK you should contact TAC.
To import the trusted CA certificate in R80.20 is the same way as in R80.10 (SmartConsole > HTTPS Inspection > Advanced > Trusted CA > Import outbound certificate) as Dameon Welch-Abernathy mentioned.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just checked myself, R77.30 and R80.20 show exactly the same option pictured in the post cezar varlan pasted.
The option is there, though perhaps it is not labeled exactly as noted in the SK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon Welch-Abernathy i believe in R77.30 you would have an "Advanced" Tab which is missing in my screenshot from 80.20. However the naming of the button is probably the same.
The SK is still wrong however ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The naming of the menu is the same.
Please make sure to leave feedback in the SK so we can improve it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The wording using "outbound" is what i believe unfortunate.
Just confirmed with TAC via a SR now. After they have checked, they have confirmed this is the correct import button.
Probably the SK should have either the full button label, or the label should be shortened.
Issue is fixed. For some reason the default Check Point trusted list of Root CA's is not complete. Microsoft looks like it trusts this particular cert chain out of the box. Error for " untrusted" Certificate Chain has dissapeared and has been repalced with invalid (OSCP cannot connect) but the traffic works this time.
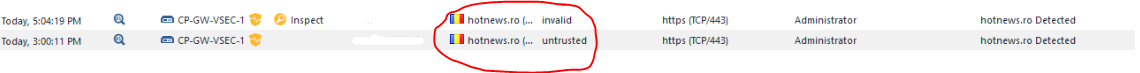
Untrusted is automatically blocked, while invalid is allowed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have a question, I need to get blade updates from an SMS working. The SMS is using a third party proxy to reach the internet. The Proxy does deep SSL inspection. I've updated the ca-bundle.crt file on the SMS to include the cert that the Proxy is using. This gets the GAIA level updates working.
Now when attempting to do application level updates for example IPS update this still fails. I did attempt to install the cert in the 'Trusted CA's section (Import outbound certificate), but still no luck.
Any suggestions? I do have a TAC case open but TAC have not come back to me in about 2 days now.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


