Hello guys,
I am currently building a small lab to test some things related to the CCSE exam. So I set up a small network with two sites, one site (Site A) contains two security gateways (running Gaia R80.10) that work together as a VRRP cluster. The same site also contains the corporate SMS which manages the just mentioned cluster as well as the second site (Site B). On site B we can find another security gateway, this time a single one, not running any cluster solution whatsoever. Each site has a internal network for the clients and the A site (the main one containing the cluster) also has a management and DMZ network, containing the SMS and a web server respectively.
So long story short; I tried to establish a IPsec site to site vpn connection connection between the VRRP gateway cluster and the single gateway on the other site. To achieve this I created a meshed VPN community, placed the cluster & single gateway in it + configured the details such as the encryption suite and to disable NAT within the tunnel/VPN community. On the gateway objects itself I just configured the VPN domain (the internal, user networks, for each site). Now the problem is, when I try to initiate connections from site 1 to site 2 and vice versa no traffic is actually passing. However, I can see that a phase 1 tunnel can be established from site 1 (VRRP clster site) to site 2:

As you can see the second direction is completely empty. The shown IP addresses are btw. not public ones, I just use them in my lab which runs completly offline. So, as I checked this and saw that Site 2 (B-GW) was unable to set up a connection with site 1 (A-GW cluster) I saw the need to verify the logging and...
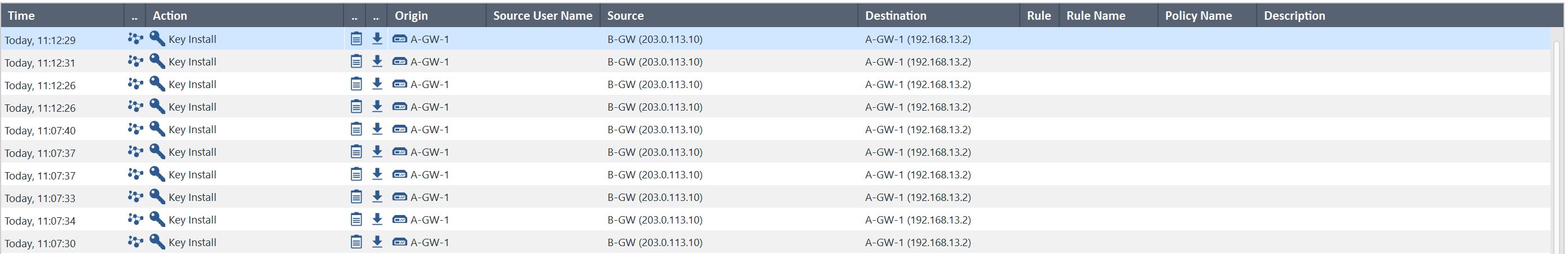
I could see that the necessary keying information was being sent out from B-GW (still the single one) to the A site (running the cluster). But it seems like that the B-GW is currently not sending out its traffic to the virtual cluster IP of A-Cluster but instead to the real IP of the first cluster member (A-GW-1). This is leading the key negotiation to the point where it fails with the "invalid certificate" message, as the VPN & related cert has been conifgured for the cluster IP:
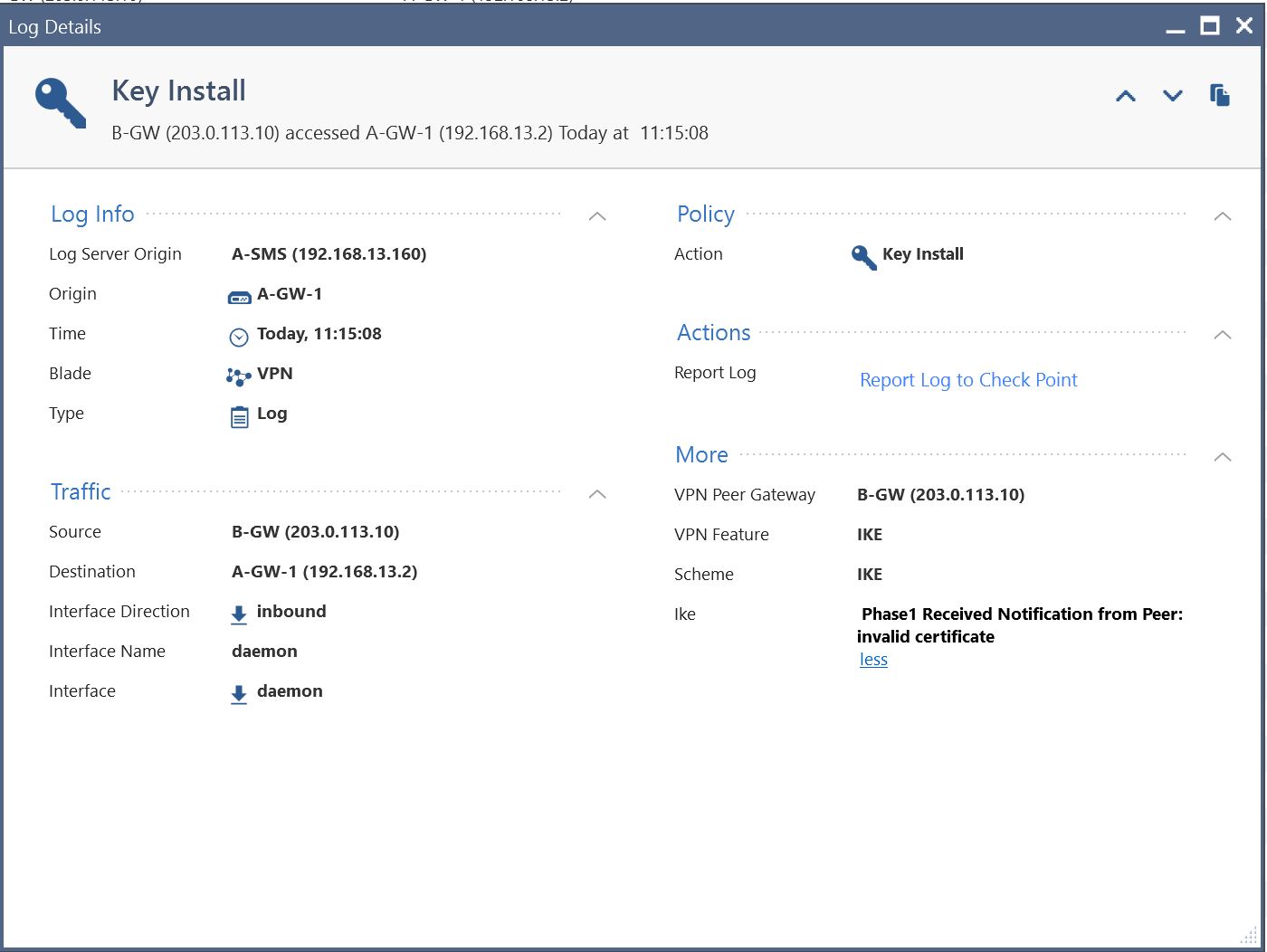
All the traffic is dropped from a A-GW-1 - which is indeed the acrive VRRP member. But now my question is - what am I missing? And why is A-GW-1's IP being used instead of the cluster virtual IP (which is .1 for the related networks of A)?
Further information:
203.0.113.0/24 is the "internet" within my lab, where both sitea are connected to via their gateways - the .10 in the fourth octett represents the management IP for the single gateway on the B site.
192.168.13..0/24 is the management network of site 1 - the .1 in the fourth octett represents the management IP for the VRRP cluster.
Thanks in advance for any advice.


