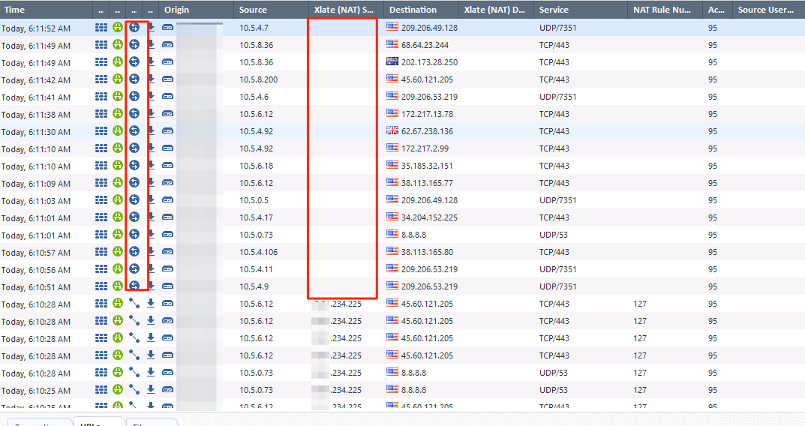
I have recently had some customers that have had challenges with the connection based logging. With connection based logging the number of logs are sometimes in multiples of 8-10 more than session based logging depending on the traffic. One of the things I have gotten in the habit of doing is changing all connection based logging to session based. Especially if turning on new blades and log storage is an issue. This recently bit me because all of a sudden there was no NAT appearing in the logs and the only way that NAT is visible is if you do log connections. This seems like an important thing to be logging, but if you are trying to conserve space you are out of luck. I have also seen another example of where the clean-up rule was session based and therefore not logging and only after cussing a bit and pulling my hair out did I do a zdebug drop and see the traffic dropping? Am I off base here? Shouldn't there be a happy medium between session and connection based logging, log storage, and getting all of the information you need?
Here is an example. The highlighted log shows my traffic as I would expect. Not until I turned back to connection based logging did I see the erroneous NAT. Hours of time troubleshooting other pieces of the network because Check Point is not providing me something that thy have provided me for the past 20 years.
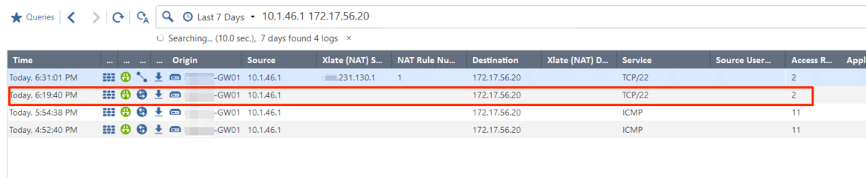
Below is the output while nothing shows up with session based cleanup logging:
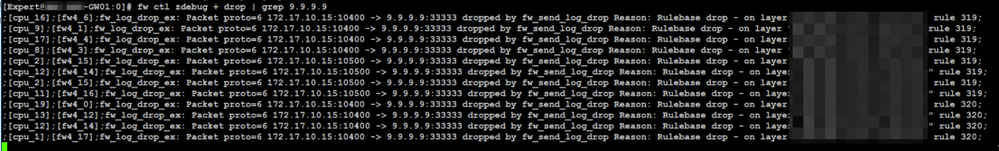
There has to be a happy medium between getting the information you need and blowing up your disk. When you talk to TAC about this you get a snarky "you should have read the upgrade guide before you upgraded." OK. Fair enough. You should read the upgrade guide. But who would think that an upgrade is going to quadruple your logs or even more. A lot of my customers can't afford to redo their logging architecture because of an upgrade so they are stuck with getting some of what they need in the logs because they can't afford the space.
I write today because I hope I'm wrong and I'm just overlooking something. Maybe I'm configuring it wrong? I am constantly second guessing Check Point logs now because I'm unsure of what I'm seeing is actually what the firewall is doing and that's clearly not good.
I welcome any feedback.
Thanks,
Paul