- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: CPT - Check Point Packet Trace Utility ?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CPT - Check Point Packet Trace Utility ?
25 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just do it. Would be very appreciated and useful for many mates, I am quiet sure. ![]()
There is the packet injection tool from CP but something similar to the packet tracer would be very nice.
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only thing I know of is Packet Injector (sk110865), but that is done from the gateway itself via CLI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think you might see something similar in R80.20. Checkpoint will implement the rule assistance utiliy which can be used to determine if there is a rule or not for certain traffic and it helps you to place the rules in the correct location.
Checkpoint has another utility that injects the packets but you have to run it from the gw
Check Point Packet Injector
In R80.10 gateways there is another utility (not documented) that doesn't inject packets but it does go through the policy files and database and tells you which rules the traffic will match but it doesn't inject the packets.
[Expert@GW01:0]#fw up_execute
Usage: fw up_execute [src=<IP>] [dst=<IP>] ipp=<ip protocol> [sport=<source port>] [dport=<dest port>] [protocol=<protocol>] [application=<application/category>]
Notes: Parameters can be omitted, except the ipp (and dport in case of TCP or UDP).
The order of the parameters does not matter.
Applications can be entered multiple times.
Examples:
1) fw up_execute src=126.200.49.240 dst=10.1.1.1 ipp=1
2) fw up_execute src=10.1.1.1 ipp=6 dport=8080 protocol=HTTP application=Facebook application=Opera
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is also packet mode from SmartConsole: Use R80.10 New Packet Mode Feature to Search Through Policy - YouTube
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
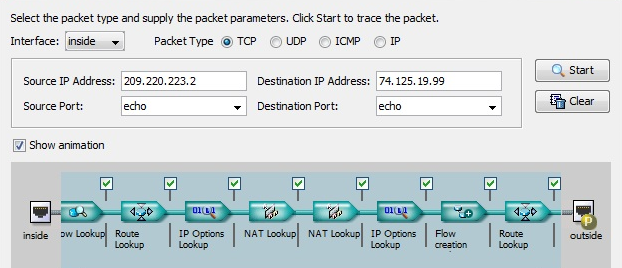
Packet Inject tool isn't bad, but I agree with others that some kind of simulation graphic tool will be appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use:
fw monitor -p all -e "accept(...);"
-> The old classic!
fw ctl zdebug + monitorall | grep -A 1 <IP w.x.y.z>
-> It's an undocumented command that's very helpful. It is nice that no "fwaccel off" is necessary. With this command you can see even more details than "fw monitor" 🙂 The firewall worker and the CPU core are also displayed here. For more informtions: "fw ctl zdebug" Helpful Command Combinations
Example view:
...
eth0:O12 (tcpt outbound)[940]:10.1.1.1 -> 10.1.1.81 (TCP) len=940 id=18052;
;[cpu_2];[fw4_1];TCP: 22 -> 10058 ...PA. seq=4ced07e1 ack=75e09a88;
eth0:O13 (TCP streaming post VM)[940]:10.1.1.1 -> 10.1.1.81 (TCP) len=940 id=18052;
;[cpu_2];[fw4_1];TCP: 22 -> 10058 ...PA. seq=4ced07e1 ack=75e09a88;
eth0:O14 (IP Options Restore (out))[940]:10.1.1.1 -> 10.1.1.81 (TCP) len=940 id=18052;
;[cpu_2];[fw4_1];TCP: 22 -> 10058 ...PA. seq=4ced07e1 ack=75e09a88;
...
and Packet Injector:
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, please do it. I came from a Cisco ASDM environment and this is definitely a feature that I miss. In fact, I have been asking about it for a few years now with several of the SE's that have been assigned to my account. This would be especially useful with layered rules that contain both tradition policies as well as blade specific (i.e. app/url/Antibot) policies to be able to test possible policy updates and get a graphical depiction of success or failure before they are actually installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should start, do not wait for checkpoint. There is packet tracer on cisco firepower and also checkpoint packet injector, you can customize these and this would be useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Danny,
Sorry to dig into such an old thread, but since no clarification regarding an Check Point implementation was mentioned (I guess it is not planned due to packet mode search/pinj/fw monitor/fw vtl debug) - did you start with an own implementation? Or would you think it makes sense to open a thread where we ask the whole community if they would be interested in such a solution? Maybe Check Point is willing to implement it in a future release if enough people show their interest. ![]()
I personally would benefit from such a tool, maybe placed on the SMS itself to be able to search through multiple policies and/or layers at the same time without the need to do it locally on the gw.
Regards,
Maik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I haven't started developing this yet as I'm currently working on an accompanying Bash script to Timothy Hall's Max Power Firewalls book.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Lets vote ![]()
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When all the competitors have it, it should be a question of when not if ![]() .
.
Palo Alto:
test security-policy-match
test nat-policy-match
test pbf-policy-match
https://www.linkedin.com/in/yurislobodyanyuk/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We already have this capability in the CLI, at least for the Access Policy.
See above comment that I marked "correct."
Check Point does not not currently have this for NAT (which would be nice to have) or Policy Forwarding (which assumes routing based on Application, something not currently in the product).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the GUI or the API: How to use R80.10 Packet Mode feature to search in Access Control Policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw up_execute is really great tool and it works well. The only issue I see is that you need to run it from specific gateway.
The best will be to execute it from management with parameter for which gateway you want to find a match (or search all policy packages).
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw up_execute is considered an "internal tool" according to my sources in R&D.
This tool does not support all the objects in the rulebase (e.g. Access Roles).
Packet Injector is the supported way to do this: Check Point Packet Injector
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ETA when will be "pinj" available for R80.20 gateways ?
[Expert@GWA_R8020:0]# tar -zxvf pinj_v1.4.6_R80.10.tgz
CPPinj-R80-00.i386.rpm
[Expert@GWA_R8020:0]# rpm -ihv CPPinj-R80-00.i386.rpm
Preparing... ########################################### [100%]
1:CPPinj ########################################### [100%]
[Expert@GWA_R8020:0]# cat /opt/CPInstLog/install_Pinj_R80.elg
#####################################################
Start Pinj preinstall script...
Set umask for this session...
End Pinj preinstall script...
#####################################################
#####################################################
Start Pinj postinstall script...
Set umask for this session.
Activate profile
1. Add keys to Check Point registry
0
Pinj registry key will be set to 0
0
2. Add lines to environment files
2.5. Update HFA registry keys
XInstall: /opt/CPPinj-R80/bin/hook_Pinj_HOTFIX_R80_10 file not found
Fail in call to ExecuteFile!
WARNING: No postinstall found at /opt/CPPinj-R80/system/install/postinstall
End Pinj postinstall script...
#####################################################[Expert@GWA_R8020:0]# cd /opt/CPPinj-R80/
[Expert@GWA_R8020:0]# ./pinj
Traceback (most recent call last):
File "main.py", line 11, in <module>
import generator
File "/opt/CPPinj-R80/scripts/generator.py", line 15, in <module>
from scapy.all import *
File "/opt/CPPinj-R80/scripts/packetmaker.zip/scapy/all.py", line 28, in <module>
File "/opt/CPPinj-R80/scripts/packetmaker.zip/scapy/route6.py", line 271, in <module>
File "/opt/CPPinj-R80/scripts/packetmaker.zip/scapy/route6.py", line 29, in __init__
File "/opt/CPPinj-R80/scripts/packetmaker.zip/scapy/route6.py", line 42, in resync
File "/opt/CPPinj-R80/scripts/packetmaker.zip/scapy/arch/linux.py", line 245, in read_routes6
IOError: [Errno 12] Cannot allocate memory
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is nice thread as we came to know all possibilities of troubleshooting ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some news here? Are there some new tools ready for R80.20 or R80.30 to check if traffic is already allowed or not? via CLI.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
really a nice tool 'fw up_execute' and definetely worth to enhance/improve
However, I did not understand until now what a 'clob' is and what Rule 16777215' means. As well, more cosmetic, it does not properly show the rule number when using Global Policy / Inline layer.
Regards,
Rulebase execution ended successfully.
Overall status:
----------------
Active clob mask: 0
Required clob mask: 0
Match status: MATCH
Match action: Accept
Per Layer:
------------
Layer name: Network
Layer id: 0
Match status: MATCH
Match action: Accept
Matched rule: 2
Possible rules: 2 16777215
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the utility is useless in the real world.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds great!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 15 | |
| 9 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter