- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: IPS Profile & Exception - Priority - Exception...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IPS Profile & Exception - Priority - Exception not working
Hi all,
I've created a IPS profile according to our needs and almost everything is working well, except of one thing:
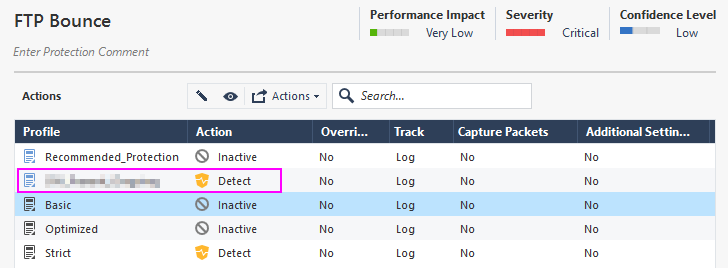
In my IPS profile I've set the IPS protection FTP Bounce to Action: Detect
This works fine and a lot of logging information is generated. Most of the detected attacks are generated by a single external IP which is is unknown to us and fills up our logs.
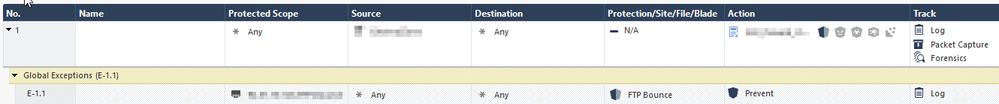
Therefore I've created an exception for this single IP where I want to have "prevent" as an action for this protection.
I've tried several ways to create the exception (Protected scope vs Src/Dst) but for this IP the FTP Bounce protection stays in detect mode and the same logs as shown above are generated.
Do I miss something in general? Are there some priority levels which keeps the FTP Bounce Protection to be in Prevent mode for this single IP?
Our firewall cluster is on V80.20 while our Mgmt Server is on V80.30
Kind regards
Oliver
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is why in R80.30:
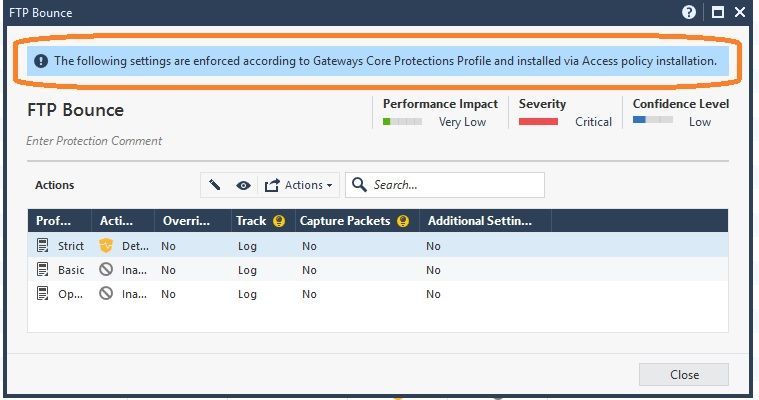
The FTP Bounce protection became a "Core" Protection in R80.30 and no longer part of the IPS blade (even though the log card says it is) so your Threat Prevention exception will have no effect, since FTP Bounce is part of the Access Control Policy. Strangely this signature says it is a Core Protection in R80.30 but it doesn't have the "shield w/ firewall" icon like a typical Core Protection (example: FTP Commands). This is really strange and I don't know what to make of it, but is probably due to the very old age of this protection (2002) dating back into the SmartDefense days which were not a fun time.
Because it is a Core Protection in R80.30 the only exceptions that can be added will completely inactivate the protection, you are not allowed to set Prevent (or Detect) in an exception like you can with an IPS ThreatCloud Protection. So as mentioned earlier your only play here is to set Inactive; this is due to the "no-mans land" that Core Protections sit in between Inspection Settings and IPS ThreatCloud Protections as described in my IPS Immersion class.
You can see a prior issue like this here: https://community.checkpoint.com/t5/IPS-Anti-Virus-Anti-Bot-Anti/FTP-Bounce-prevent-instead-of-inact...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not have any idea why your exception is not working, but honestly, any IPS protection set to Detect will cost resources without adding any security ! I would suggest to switch it to prevent after the IPS deployment testing phase is over.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many thx for the notice on the resources of the gateway, but unfortunately I cannot set the protection to prevent as this would cause some ftp connections from our customers to be dropped.
Kind regards
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So why not switch it off completely ? Remember, this is an EServ 2.97 vulnerability from 2002 !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probabely this will be the final solution, but still doesn't explain why the exception is not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is why in R80.30:
The FTP Bounce protection became a "Core" Protection in R80.30 and no longer part of the IPS blade (even though the log card says it is) so your Threat Prevention exception will have no effect, since FTP Bounce is part of the Access Control Policy. Strangely this signature says it is a Core Protection in R80.30 but it doesn't have the "shield w/ firewall" icon like a typical Core Protection (example: FTP Commands). This is really strange and I don't know what to make of it, but is probably due to the very old age of this protection (2002) dating back into the SmartDefense days which were not a fun time.
Because it is a Core Protection in R80.30 the only exceptions that can be added will completely inactivate the protection, you are not allowed to set Prevent (or Detect) in an exception like you can with an IPS ThreatCloud Protection. So as mentioned earlier your only play here is to set Inactive; this is due to the "no-mans land" that Core Protections sit in between Inspection Settings and IPS ThreatCloud Protections as described in my IPS Immersion class.
You can see a prior issue like this here: https://community.checkpoint.com/t5/IPS-Anti-Virus-Anti-Bot-Anti/FTP-Bounce-prevent-instead-of-inact...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Timothy,
many thx for clarification. IPS have been easier in V77.30 without the split in the different "classes".
Kind regards
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this, I would have never noticed that banner at the top about it being a core protection.
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter