- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: exclude checkpoint public/external ip from enc...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
exclude checkpoint public/external ip from encryption domain?
Hello.
Yes another one of these regarding crypt.def file that needs to be modified but slightly different.
there are currently 2 sites with a checkpoint cluster.
both are managed by the same SMS located in site 1 ( site1 cluster managed via internal ip, site2 cluster via public ip)
the 2 clusters also make a s2s vpn.
(this is running now with no modifications to crypt.def file)
the company wants a multi vendor approach and has decided to change the roll of the checkpoint to internal/dmz firewall and bought palo alto firewalls to be the internet facing firewall.
the main site will be migrated first which means there will be an intermediate setup where the internet facing firewall on site 1 will be palo alto and the remote site will still be checkpoint.
(also requiring a s2s tunnel from palo alto to remote checkpoint)
I already want to prepare the crypt.def file right now (when it's still checkpoint to checkpoint) but am a bit confused which entries I then have to configure to make sure both checkpoint clusters don't send the remote public ips inside the tunnel.
so far I got:
vpn_exclude_1={<"site1 1st public ip","site1 3rd public ip">};
vpn_exclude_2={<"site2 1stpublic ip","site2 3rd public ip">};
#define NON_VPN_TRAFFIC_RULES ((src=vpn_exclude_1) or (src=vpn_exclude_2) or (dst=vpn_exclude_1) or (dst=vpn_exclude_2))
but I'm not sure if this is not too much.
open questions:
1: they are both clusters so the checkpoints have a vip ( 1st ip), gw1(2nd ip), gw2(3rd ip) hence the vpn_exclude objects contain a range of 3 ip's.
I'm not entirely sure if this is necessary? do I need to exclude each ip defined on a checkpoint ( vip and physical interface ip) or would i only need to exclude the vip?
or should I just exclude the entire public ip subnet of each site (eg /28) ?
2: both checkpoints clusters will have to use this crypt.def file to exclude the other's public ip from the tunnel
my logic:
I need to include "src=vpn_exclude_1" and "dst=vpn_exclude_2" for the cluster on site 1 to make sure it does not send its own public ip in the tunnel and so that it knows it can accept the public ip of site2 outside the tunnel
I need to include "src=vpn_exclude_2" and "dst_vpn_exclude_1" for the cluster on site 2 to make sure it does the exact same.
so 4 statements required to get this to work between 2 checkpoint peers
Am I correct here or do I not need to include those 4 statements in the non_vpn_traffic_rules
During migration (intermediat setup with 1 side palo alto) as long as the peer ip used by the palo to setup the vpn tunnel is one of the 3 addresses that is already excluded it should require no further modification on the remote checkpoint once the local gateway becomes a palo alto.
goals of doing this:
I do not want to lose my mgmt connection to the remote gateway when installing this policy (with the new crypt.def file)
I do not want to lose my mgmt connection to the remote gateway over public ip when we install the palo alto in front of the checkpoint on site 1. (at this point the public ip is moved away from the site1 checkpoint and natting behind public ip will be done by the palo alto)
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Tommie,
Indeed, to exclude the public IP address form the encryption domain , you will need to modify the crypt.def file. I'm still hoping for a check box to enable/disable this in the future !
There is no real need for this exclusion just to setup a VPN tunnel to a 3th party, only if you need communication over the IP addresses outside the tunnel (icmp, webserver running on the same Public IP and outside of the tunnel, ..)
I think your syntax is correct, but a bit too much with only OR's, I would create it like this :
vpn_exclude_1={<"site1 1st public ip","site1 3rd public ip">};
vpn_exclude_2={<"site2 1st public ip","site2 3rd public ip">};
#ifndef NON_VPN_TRAFFIC_RULES
#ifndef IPV6_FLAVOR
#define NON_VPN_TRAFFIC_RULES ((src in vpn_exclude_1 and dst in vpn_exclude_2) or \
(src in vpn_exclude_2 and dst in vpn_exclude_1))
#else
#define NON_VPN_TRAFFIC_RULES 0
#endif
#endif
question 1 :
I think only the VIP is needed and not the physical IP addresses, but no harm to add them.
question 2 : indeed, should be like this :
(src in vpn_exclude_1 and dst in vpn_exclude_2) or
(src in vpn_exclude_2 and dst in vpn_exclude_1)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed, to exclude the public IP address form the encryption domain , you will need to modify the crypt.def file. I'm still hoping for a check box to enable/disable this in the future !
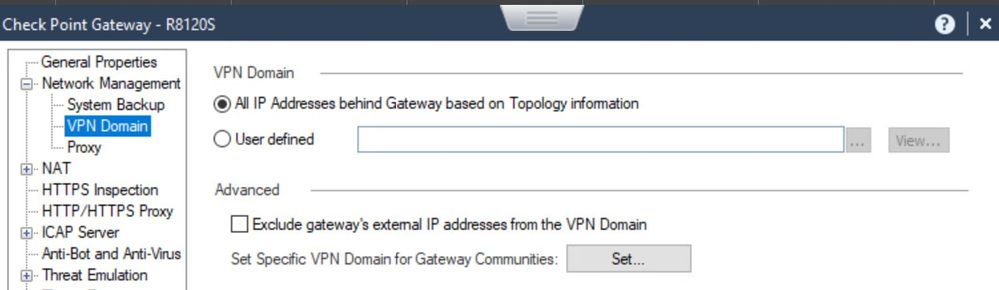
It's there in R81.20:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will this option "Exclude gateway's external IP addresses from VPN Domain" be available for SMB Devices as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see no reason why we wouldn't, but it doesn't seem to be supported at present.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've noted that "vpn-domain-exclude-external-ip-addresses" is not available in the API (2.0) which is set when you enable "Exclude gateway's external IP addresses from VPN Domain" from the GUI. Do we know when this will be available?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Offhand, I do not.
However, there are many things relative to the gateway object that still need API support.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 10 | |
| 10 | |
| 9 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter