Hello everyone!
I need your help...
I have 3 different FW clusters on my network, on different sites, let's call them:
Cluster 1 at site 1 (holds network A)
Cluster 2 at site 2 (holds network B)
Cluster 3 at site 3 (holds network C)
while each of them is responsible for a network:
10.0.0.0/24 Network A
20.0.0.0/24 Network B
30.0.0.0/24 Network C
I point out that in each of the sites where there is a cluster, the FW also has legs for the benefit of the other networks, for users of these networks who are on these sites.
In addition to this I have several small satellite sites where there are users who will connect to any of my networks.
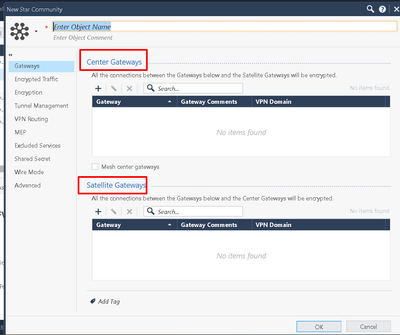
I created 3 VPN Community between the relevant satellite sites and the clusters in a star configuration, for the benefit of each of the networks.
That is, I have 3 VPN Communities, each of which has a different cluster that is defined as a Center and a number of small FWs that are defined as satellites.
The sites themselves have an encryption domain that contains all the networks that exist on the site.
This is my existing situation, now I will explain the problem...
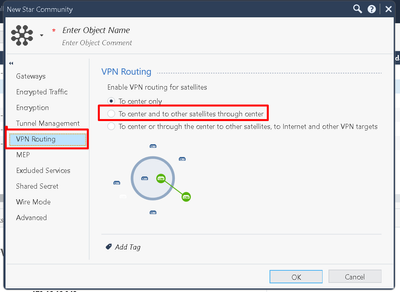
When I am at a satellite site sending a ping from a computer located on network A to a computer at another satellite site on the same network (A), I expect the traffic to go through cluster 1 that holds network A, and from there to the other satellite site.
What actually happens is that when I send a ping from one satellite site on network A to another site on network A, I recognize that the traffic goes through cluster 2, for example, which serves as a center for VPN Community that is not relevant to network A.
I saw that there is an option to define in the Rule itself which VPN it will be associated with, I tried it and the situation did not change.
- Is this the normal situation?
- If this is not a normal situation, what do I need to change / specify in order for it to be resolved?
I would appreciate your advice