- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Updatable objects with geo policy
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updatable objects with geo policy
Hi,
We have an R80.30 Gateway and management, we apply a geo policy to allow only specific countries to our org.
now we transfer our mail service to 365 cloud and keep our on-perm mail relay and we want all outgoing emails to continue going through the on-prem mail relay.
the issue is geo policy does not support the updateable objects and we cant update the 365 cloud ip addresses every other day.
any solution ?
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The traditional Geo Policy does not support Updatable Objects, nor is this planned.
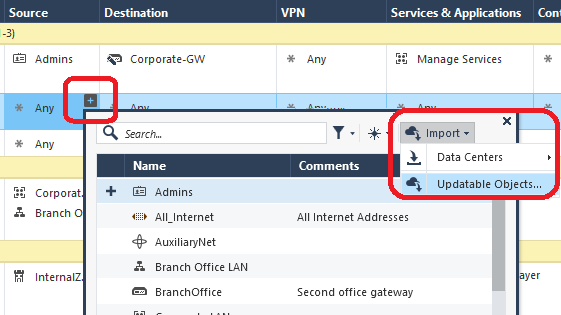
You can use Updatable Objects for different geographies in the Access Policy, however.
And, in fact, this is the approach we recommend for implementing Geo Policy in general in R80.20+ as it permits far more flexibility than the traditional Geo Policy provides.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also Geo Policy is hidden starting from R81 > see sk126172
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Geo Policy is still supported in R81, but it will be hidden in the SmartConsole if nothing has been changed in Geo Policy from the default settings "out of the box".
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you please elaborate on "dfferent geographies in the Access Policy" ? how do we implement this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
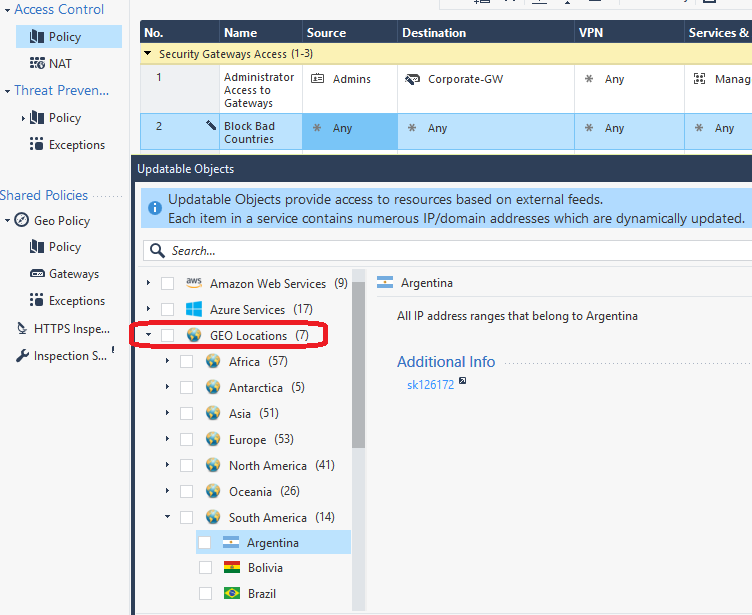
Here are some screenshots from my book showing how to utilize Geo Updatable Objects in R80.20+:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue with these objects is that you can not fully trust your log files. This is because security gateways update their GeoIP database automatically (sk126172) while security managements don't (sk120261). Checking to which region a security gateway actually resolves an IP address also is a manual process that includes some calculation and range checking and CLI command handling (sk94364).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Danny, did you actually catch any mismatch? Just to make sure your distrust is justifiable 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fair enough. Please raise it to TAC, thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Done. SR closed. Reason: That's the design of the product. Security Managements don't update their GeoIP database by themself. Workaround: Manual via sk120261 as I mentioned above or via my One-liner to update IpToCountry data on Security Managements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry to hear that. I will check internally and let you know
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Danny I have spoken to the product owners. We do have dynamic update of Geo IPs on MGMT side on the road map, but the exact time frame is not clear. I hope it will be done soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To add to Tim's message -
The R80.20 way of updateable objects is the most recommended solution.
In order to migrate from the geo policy to this new way, simply create an ordered layer prior to your firewall layer at the access control policy, and recreate the country rules. This will basically keep the same logics as the geo policy, only with up to date IP address ranges for the countries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomer_Sole,
We want to allow only connections from Israel to our org and allow our org to all countries.
I have created a new access Policy layer beforce our default FW policy with these two rules attached, will these be OK ? the traffic will continue to the second access layer and will be processed according to our default policy ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A connection must match an Accept rule in each ordered layer.
If the connection doesn't get blocked by your first rule as shown, then it hits an Accept rule and must hit an Accept rule in subsequent layers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I wanted to share a bit more on this topic:
- It's important to emphasize that the flags that you see on the logs are cosmetic information and do not affect the enforcement. They are calculated according to the csv (mentioned in other comments) during the log query.
- We do understand that it's confusing to see a flag that is not updated to the latest categorization of an IP. Even more so, if that IP was blocked on a geo rule. As stated, we don't yet update the flag csv file automatically, but following the feedback in the thread, we will make sure to update it more regularly in JHFs.
- If you are using updatable objects for geo-blocking in your policy (which is a good way to do it), then inside the log details (double click the log), you will also see the exact updatable object that was matched. This will include its name and icon. In case of a geo updatable object, that will include the country name and flag. That is the most accurate way to see which country was matched in the rule, especially since that value is attached during enforcement and not calculated later during the query.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to add an "exception" to the country objects? How do I allow an IP to connect from an otherwise blocked country?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There aren't really true exceptions in an Access Control policy. In that case just add a separate Accept rule for the permitted IP, somewhere above the rule using the Geo Updatable Object to block that country.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's what I suspected. It's kind of a bummer because an exception in the geo policy meant that the IP could come from the blocked country but still had to traverse the rule base as it's laid out.
I can overcome this with layers where the the "entrance criteria" for the inline layer rule allows the exceptions to enter the layer. Below that rule is the country block rule. Then below that rule is another inline layer rule where the entrance criteria is all internet.
Using the layers like this allows me to simulate the traversing of the rule base for exceptions but it makes things a little ugly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you everyone, the issue is resolved.
the old GEO policy was changed to inactive and the new GEO policy is applied by a new ordered layer before the access control policy !
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 21 | |
| 12 | |
| 9 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 | |
| 7 |
Trending Discussions
Upcoming Events
Thu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter