- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Terrapin Vulnerability - All Linux servers are...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Terrapin Vulnerability - All Linux servers are vulnerable globally including CheckPoint
Hi Team,
All of my CheckPoint firewalls have been scanned recently, and it appears that they are all displaying vulnerable hosts due to a recently disclosed vulnerability known as Terrapin. Though I patched my Linux hosts with Customized Ciphers but wondering how do I start with CheckPoint?
Any comment from CheckPoint staff?
@PhoneBoy @Chris_Atkinson 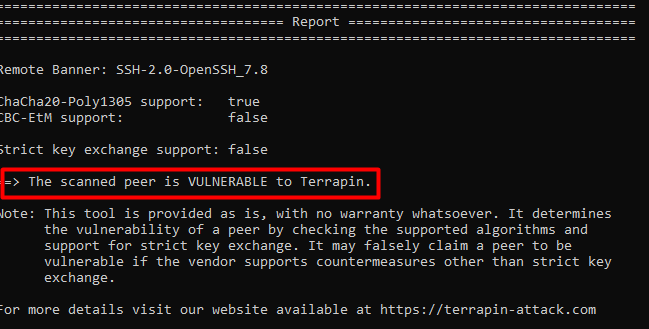
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just did that for training, it was easily done in clish:
enabled cipher:
--------------------------------
aes128-cbc
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-ctr
aes256-gcm@openssh.com
chacha20-poly1305@openssh.com
set ssh server cipher chacha20-poly1305@openssh.com off
enabled cipher:
--------------------------------
aes128-cbc
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-ctr
aes256-gcm@openssh.com
enabled mac:
--------------------------------
hmac-sha1
hmac-sha1-etm@openssh.com
hmac-sha2-256
hmac-sha2-256-etm@openssh.com
hmac-sha2-512
hmac-sha2-512-etm@openssh.com
umac-64-etm@openssh.com
umac-64@openssh.com
umac-128-etm@openssh.com
set ssh server mac hmac-sha1-etm@openssh.com off
set ssh server mac hmac-sha2-256-etm@openssh.com off
set ssh server mac hmac-sha2-512-etm@openssh.com off
set ssh server mac umac-64-etm@openssh.com off
set ssh server mac umac-128-etm@openssh.com off
enabled mac:
--------------------------------
hmac-sha1
hmac-sha2-256
hmac-sha2-512
umac-64@openssh.com
umac-128@openssh.com
--------------------------------
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The new SK is published to address the issue: https://support.checkpoint.com/results/sk/sk181833
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you remove aes128-cbc cipher?
31 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This actually came out today
https://www.helpnetsecurity.com/2023/12/19/ssh-vulnerability-cve-2023-48795/
I searched for CVE and also Terrapin on support site, nothing so far, except link to your post.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This attack isn't terribly practical. It requires full control over a router or proxy in the path between client and server. The firewall itself could execute this attack on connections flowing through it. From the OpenSSH team:
While cryptographically novel, the security impact of this attack
is fortunately very limited as it only allows deletion of
consecutive messages, and deleting most messages at this stage of
the protocol prevents user user authentication from proceeding and
results in a stuck connection.
The most serious identified impact is that it lets a MITM to
delete the SSH2_MSG_EXT_INFO message sent before authentication
starts, allowing the attacker to disable a subset of the keystroke
timing obfuscation features introduced in OpenSSH 9.5. There is no
other discernable impact to session secrecy or session integrity.- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree but since it has a cve given most of the vulnerability vendor by tomorrow wil be updated with the the relevant signatures and scan will start showing as vulnerable. Though currently modifying sshd_conf file and removing chacha plus etm Mac's mitigating the vulnerability
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would agree with that, hope it gets addressed soon.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I expect we are evaluating internally and will provide further details when able.
In the interim please open a case with TAC and loop in your local CP SE as relevant.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Per the FAQ provided on the site mentioned:
I am an admin, should I drop everything and fix this?
Probably not.
The attack requires an active Man-in-the-Middle attacker that can intercept and modify the connection's traffic at the TCP/IP layer. Additionally, we require the negotiation of either ChaCha20-Poly1305, or any CBC cipher in combination with Encrypt-then-MAC as the connection's encryption mode.
If you feel uncomfortable waiting for your SSH implementation to provide a patch, you can workaround this vulnerability by temporarily disabling the affected chacha20-poly1305@openssh.com encryption and -etm@openssh.com MAC algorithms in the configuration of your SSH server (or client), and use unaffected algorithms like AES-GCM instead.
That makes this issue less urgent to fix and something you can potentially mitigate:
- Starting from R81.10, the relevant ciphers can be disabled via a clish command: https://support.checkpoint.com/results/sk/sk165685
- For R80.40 and R81, the relevant ciphers can be disabled by editing sshd_config: https://support.checkpoint.com/results/sk/sk106031
- This issue is not relevant in R80.30 and earlier since the relevant ciphers are not used.
Based on the public information available at current, this seems like the best course of action to take.
For an official response, refer to the TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just did that for training, it was easily done in clish:
enabled cipher:
--------------------------------
aes128-cbc
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-ctr
aes256-gcm@openssh.com
chacha20-poly1305@openssh.com
set ssh server cipher chacha20-poly1305@openssh.com off
enabled cipher:
--------------------------------
aes128-cbc
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-ctr
aes256-gcm@openssh.com
enabled mac:
--------------------------------
hmac-sha1
hmac-sha1-etm@openssh.com
hmac-sha2-256
hmac-sha2-256-etm@openssh.com
hmac-sha2-512
hmac-sha2-512-etm@openssh.com
umac-64-etm@openssh.com
umac-64@openssh.com
umac-128-etm@openssh.com
set ssh server mac hmac-sha1-etm@openssh.com off
set ssh server mac hmac-sha2-256-etm@openssh.com off
set ssh server mac hmac-sha2-512-etm@openssh.com off
set ssh server mac umac-64-etm@openssh.com off
set ssh server mac umac-128-etm@openssh.com off
enabled mac:
--------------------------------
hmac-sha1
hmac-sha2-256
hmac-sha2-512
umac-64@openssh.com
umac-128@openssh.com
--------------------------------
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right - I managed to mitigate around 50+ R81.10 and 5+ R80.40 since this morning 🙂
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The new SK is published to address the issue: https://support.checkpoint.com/results/sk/sk181833
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks and thats great
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Val,
Have followed the steps in SK, Qualys still reports the Vulnerability..
Before disabling Cipher - ChaCha20-Poly1305
RESULTS:
SSH Prefix Truncation Vulnerability (Terrapin) detected on port: 22
ChaCha20-Poly1305 Algorithm Support: True
CBC-EtM Algorithm Support: True
Strict Key Exchange algorithm enabled: False
After disabling Cipher - ChaCha20-Poly1305
RESULTS:
SSH Prefix Truncation Vulnerability (Terrapin) detected on port: 22
ChaCha20-Poly1305 Algorithm Support: False
CBC-EtM Algorithm Support: True
Strict Key Exchange algorithm enabled: False
Only piece what is shown under both results is CBC-EtM Algorithm Support is set as True. I know we did not disable anything else other than ChaCha20-Poly1305, but Qualys still reports its vulnerable and CBC-Etm Algo support is set as true.
Do you have any further insight?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes disable that as well and it should be good. For R81.10 and R81.20 it has CBC-Etm
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
great! Would you also please share how did you disable that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Run below command and then we can confirm which can be disabled
show ssh server kex supported
show ssh server mac supported
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried this before, but 1st command is available on R81.20.. 2nd Command i also tried
Below is the output
xxx> show ssh server kex supported
CLINFR0329 Invalid command:'show ssh server kex supported'.
xxx> show ssh server mac supported
--------------------------------
supported mac:
--------------------------------
hmac-md5-96-etm@openssh.com
hmac-md5-etm@openssh.com
hmac-sha1
hmac-sha1-96-etm@openssh.com
hmac-sha1-etm@openssh.com
hmac-sha2-256
hmac-sha2-256-etm@openssh.com
hmac-sha2-512
hmac-sha2-512-etm@openssh.com
umac-64-etm@openssh.com
umac-64@openssh.com
umac-128-etm@openssh.com
umac-128@openssh.com
--------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should not be the case. Are you sure you rebooted after the changes? Can you confirm the vulnerable methods are no longer showing in enabled ciphers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did not reboot, as its not mentioned on the SK. But after disabling particluar cipher, i see qualys report found it disabled, but at the same time it talks about CBC-EtM - Enabled..
After disabling Cipher - ChaCha20-Poly1305
RESULTS:
SSH Prefix Truncation Vulnerability (Terrapin) detected on port: 22
ChaCha20-Poly1305 Algorithm Support: False
CBC-EtM Algorithm Support: True
Strict Key Exchange algorithm enabled: False
*****show ssh server cipher enabled
--------------------------------
enabled cipher:
--------------------------------
aes128-cbc
aes128-ctr
aes128-gcm@openssh.com
aes192-ctr
aes256-ctr
aes256-gcm@openssh.com
--------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you are right, the reboot is not required, but you need to restart sshd. Disable all vulnerable ciphers and restart the daemon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I disabled Vulnerable Cipher - ChaCha20-Poly1305, but did not find any option where i can find CBC-EtM enabled and disable it then..
I am using R81.10
And i tried sshd restart too, and waiting for scan to be completed..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nothing changed after restarting sshd. CBC-EtM is still marked as enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you remove aes128-cbc cipher?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not yet! Will disabling AES128-CBC cipher disable CBS-EtM?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CBC-EtM, not CBS as you wrote. I suspect it will. Try and see, worst case you, you will need to re-enable the cipher.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its typo error... I meant CBC-EtM only as mentioned above in all my messages..😅
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disabling AES128-CBC cipher helped. Qualys is not reporting Terrapin Vulnerability now...
Thank All!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great to hear.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mitigation of CBC-EtM sub-vulnerability is not mentioned in relevant article. Only chacha20-poly1305.
What is preffered/optimal option to mitigate CBC-EtM support?
Disable cipher aes128-cbc:
set ssh server cipher aes128-cbc off
or
Disable all, by default enabled, Macs relevant for -etm:
set ssh server mac hmac-sha1-etm@openssh.com off
set ssh server mac hmac-sha2-256-etm@openssh.com off
set ssh server mac hmac-sha2-512-etm@openssh.com off
set ssh server mac umac-64-etm@openssh.com off
set ssh server mac umac-128-etm@openssh.com off
or even both ?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


