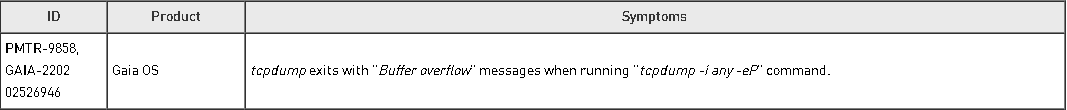
Reported version of tcpdump/libpcap did not change between R77.30 and R80.10 (3.9.4/0.9.4), at least between R77.30 vanilla and R80.10 jumbo HFA take 42 which is what I have readily available in my lab. But I am seeing the same problem you are with tcpdump crashing on R80.10 when you use the -Penni options.
Taking a closer look at the tcpdump crash with strace in R80.10:
recvfrom(8, "E\0\0004\37\272@\0\200\6VS\300\0\2\1\300\0\2\265. \0\26"..., 80, MSG_TRUNC, {sa_family=AF_PACKET, proto=0x800, if2, pkttype=PACKET_HOST, addr(6)={1, 005056c00001}, [18]) = 52
access("/proc/net", R_OK) = 0
access("/proc/net/unix", R_OK) = 0
socket(PF_FILE, SOCK_DGRAM, 0) = 9
ioctl(9, SIOCGIFNAME, {ifr_index=2, ifr_name="eth0"}) = 0
close(9) = 0
open("/dev/tty", O_RDWR|O_NONBLOCK|O_NOCTTY) = 9
writev(9, [{"*** buffer overflow detected ***"..., 34}, {"tcpdump", 7}, {" terminated\n", 12}], 3) = 53
Even though the reported tcpdump version number was not changed in R80.10, I'm guessing that Check Point must have ported in the tcpdump fixes mentioned here: Multiple Vulnerabilities in tcpdump - SANS Internet Storm Center and the fixes are running afoul of the interface determination mechanism used by tcpdump when -P is invoked.
Curious thing is while the -P option (capitalized) is shown as a valid option by the tcpdump usage statement, it does not appear to be officially documented anywhere that I can find.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
New Book: "Max Power 2026" Coming Soon
Check Point Firewall Performance Optimization